TimeKORP is a very easy web challenge created by makelaris on Hack The Box. This challenge requires performing a remote code execution attack. Hello world, welcome to haxez where today I will be putting my web hacking skills to the test by trying to compromise the TimeKORP very easy web challenge. Unlike some of the other challenges I’ve previously complete, this challenge doesn’t have any files to download. Lets crack on.
TimeKORP Application Enumeration
First, I launched OWASP ZAP (because I’m trying to learn it) and navigated to the provided IP address. Once the application loaded, I was presented with a fairly basic page that displayed the time. After clicking the ‘What is the date?’ link at the top of the page, I was shown the current date. That was the extent of the application functionality.
ZAP It
As I was viewing the application through ZAP, I decided to run the Ajax spidering tool to see if there was any content that I was missing. Other than a an assets and static directory which contained nothing interesting, there wasn’t anything else for me to look at.
As a result, I decided I should active scan the application. Granted, it isn’t always advised to use active scan. This is especially true with pages that contain sensitive functionality. However, these labs were designed to test out tools so that is exactly what I did.
TimeKORP Active Scan
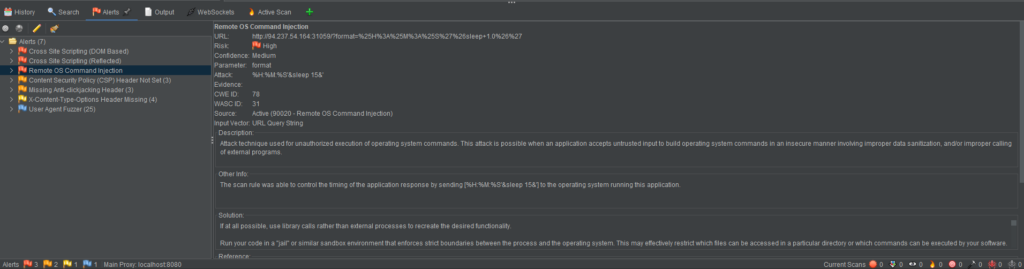
Using the OWASP ZAP browser HUD, I clicked the active scan button and waited for it to finish. As you can see from the image below, ZAP was able to find several issues ranging in severity from informational, low risk, medium risk and high risk. The informational, low and medium risk findings were all fairly standard misconfigurations such as a missing Content Security Policy header. However, the high risk finding was a Remote OS Command Injection vulnerability.
Poking The Bug
I navigated through the HUD to view and replay the request in the browser. The active scan performed a sleep command and I assume it detected that the page took a second to respond thus indicating the application was vulnerable. The URL below is the payload that active scan used to determine there was a vulnerability.
https://94.237.54.164:31059/?format=%25H%3A%25M%3A%25S%27%26sleep+1.0%26%27I modified that code to further confirm the vulnerability by running a few different commands. For example I ran the whoami command which told me I was www.
https://94.237.54.164:31059/?format=%25H%3A%25M%3A%25S%27%26whoami%26%27I ran a few other commands such as uptime to confirm I had code execution as the output on the screen wasn’t all that revealing.
https://94.237.54.164:31059/?format=%25H%3A%25M%3A%25S%27%26uptime%26%27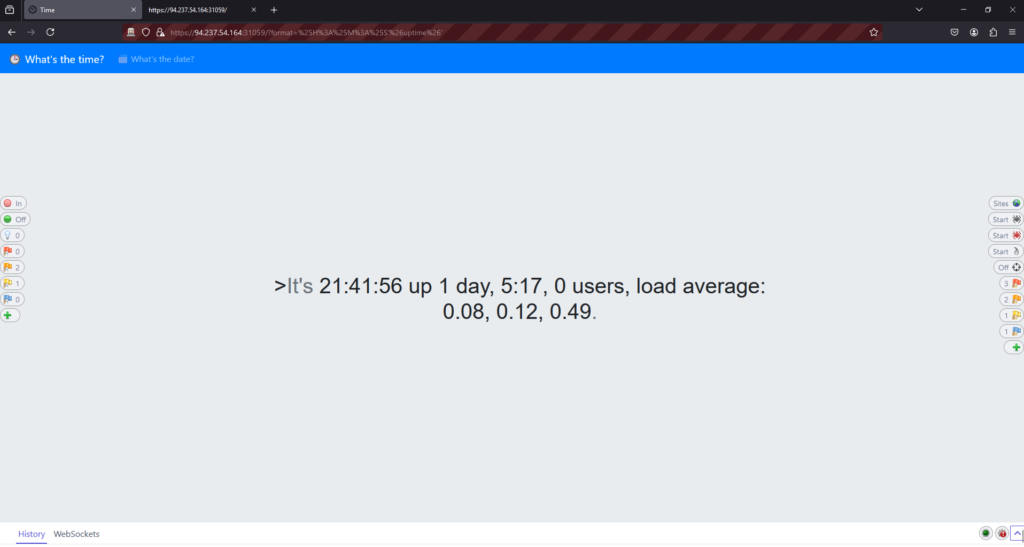
Finding The Flag
This is where things got a bit obscure. I used the ls flag and performed various directory traversals but I couldn’t find the location of the flag. What’s odd is that I could list out the views directory and see the index.php but not the flag. I didn’t think it could be a permissions issue as if I was allowed to read the flag file then I should be able to see it. Furthermore, the flag file didn’t start with a dot so it wasn’t a hidden file either. Anyway, I finally found the flag one directory above and was able to read it using the following URL.
https://94.237.54.164:31059/?format=%25H%3A%25M%3A%25S%27%26cat%20../flag%26%27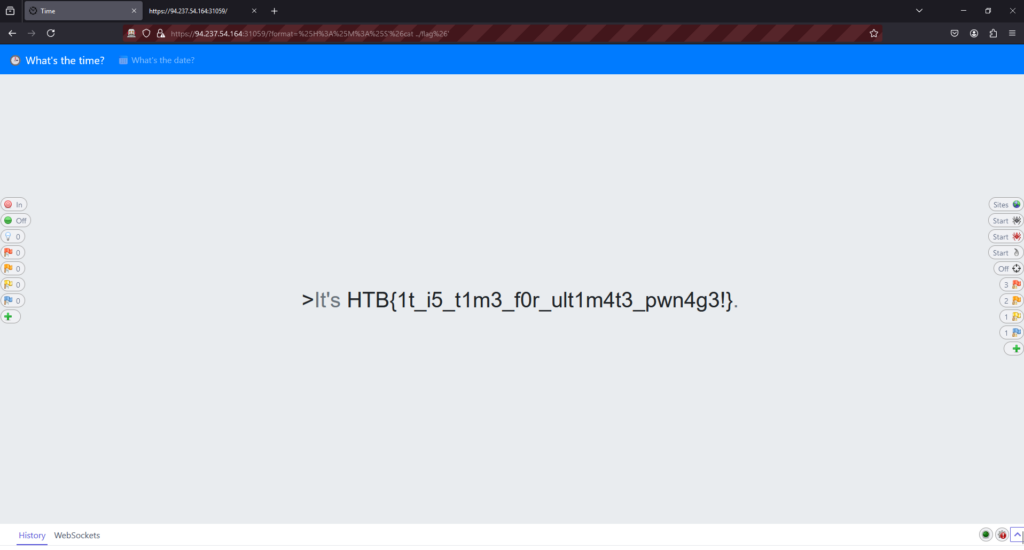
TimeKORP Learnings
I remember a quote, I think it was from Darknet Diaries. It said that hacking is like trying to navigate a maze in the dark. You have no way of knowing where you’re going or even if you are going in the right way. I’m paraphrasing but that reflects my thoughts on this challenge. When I first started penetration testing and doing web applications I was told never to use Burp Active Scan. They explained it was because it could break applications. I’ve looked at some of the payloads and believe it to be absolutely true. However, I’m trying to adopt a new mindset of active scan where you can but ensure the client has a backup.

