Phantom Script is a very easy web challenge created by Xclow3n on Hack The Box. This challenge is simple as the answer is on the page. However, I believe the purpose of this challenge is to understand why one works but not the other. Hello world, welcome to haxez where today I will be exploiting an XSS vulnerability.
Phantom Script Application Enumeration
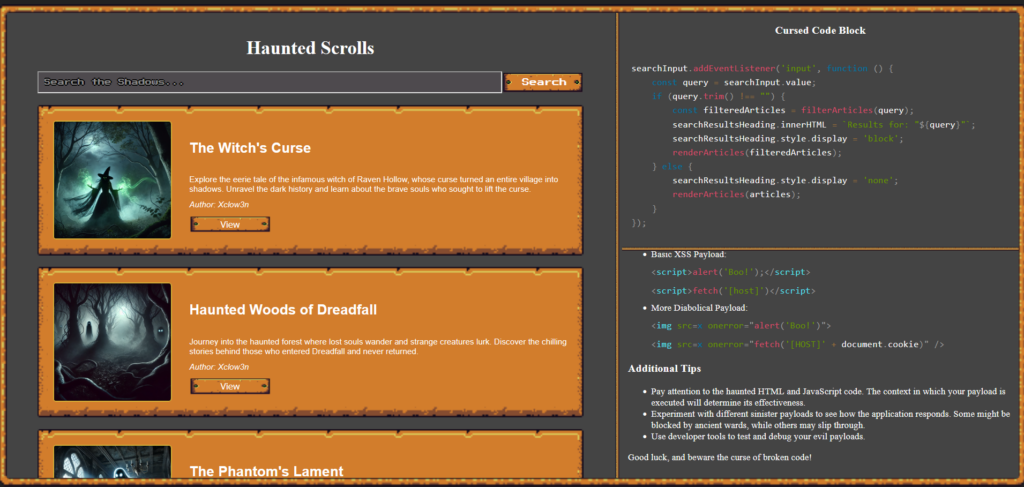
The application is very basic offering only a search box to search through the different scrolls on the page. To the right of the search box is the vulnerable code. Finally, underneath the vulnerable code are some example payloads. The answer is right there on the page, all you need to do is test the different payloads and eventually the flag will pop up. But why does it pop up.
HTML Child Elements
When we test the first payload of:
<script>alert('Boo!');</script>The browser renders the script tag as plain text rather than executing it. This happens because the script tag is not treated as a child element of the parent h2 tag. It is instead interpreted as part of the element’s textual content. As a result, the payload does not work for XSS in this case.
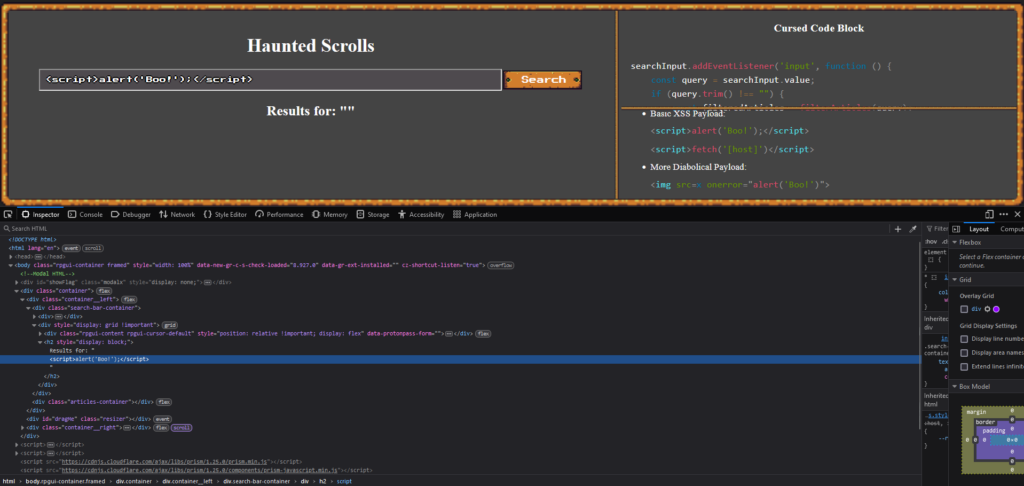
However, if we use an img element, it is rendered as HTML because the browser recognises img as a valid child element. The browser parses the img element properly, and attributes like onerror are processed, allowing for XSS execution.
<img src=x onerror="alert('Boo!')">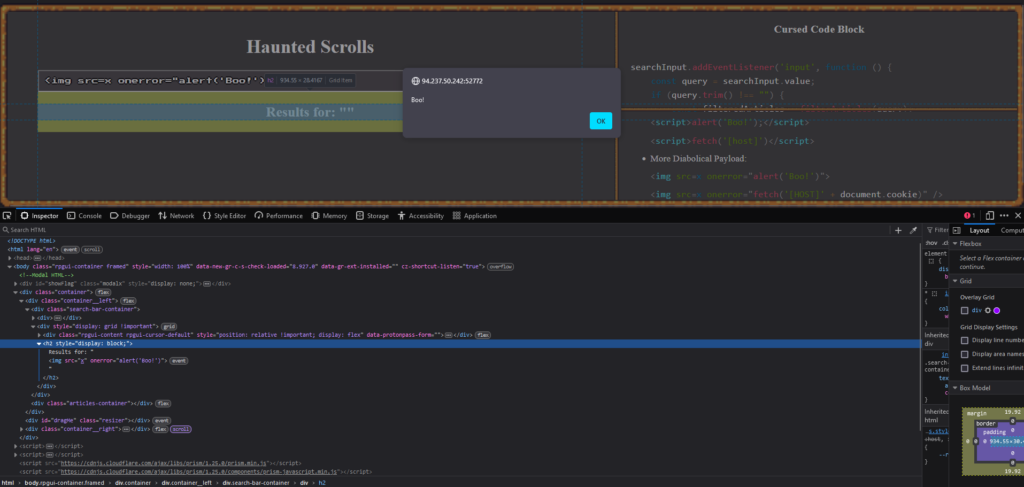
The Flag
After submitting the payload, click the alert blox to close it and the flag will appear on the screen like magic.
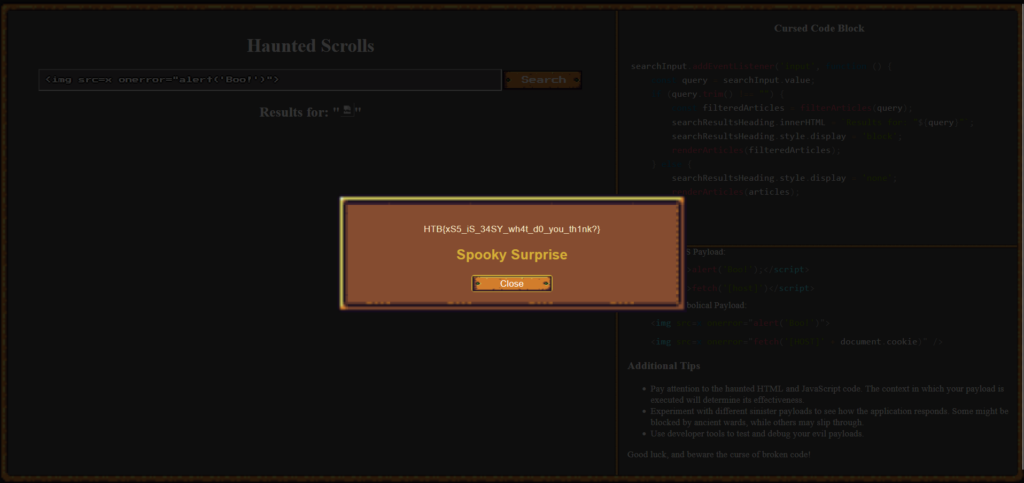
HTB{xS5_iS_34SY_wh4t_d0_you_th1nk?}Phantom Script Learnings
I must admit that this answered a question that I’ve been struggling with for a long time. It’s great being able to find bugs but understanding why they are there makes finding them easier. Before doing this challenge, I didn’t know that only child elements would work when rendered in a html tag. I suspect I have missed multiple oppertunities to get XSS because of this reason. This is why it is important to do additional reading when going through challenges and boxes.

