Hello world, welcome to HaXeZ where today we will be looking at the Hack This Site Extended Basic mission 5. This mission is another programming mission that requires you to review the contents of a PHP file and then subsequently a shell script that is used to edit the PHP file. There is an error in the shell script that prevents it from doing what it’s supposed to do. We need to fix it.
The Extended Basic 5 Code
The image below shows the code that Sam has written. The introduction message advises that Sam created a function called safeeval to run commands. However, on the page, he neglected to use safeeval and use eval() instead. Furthermore, it explains that he wrote a shell script to go through the PHP file and replace all values of eval() with safeeval. Unfortunately, there is an error in the shell script that prevents the script from working.
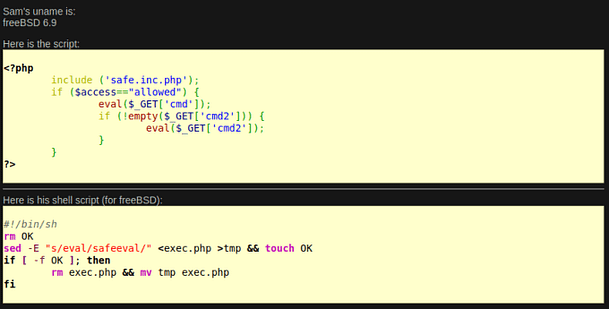
The PHP Code
<?php
include ('safe.inc.php');
if ($access=="allowed") {
eval($_GET['cmd']);
if (!empty($_GET['cmd2'])) {
eval($_GET['cmd2']);
}
}
?>The Shell Script
#!/bin/sh
rm OK
sed -E "s/eval/safeeval/" <exec.php >tmp && touch OK
if [ -f OK ]; then
rm exec.php && mv tmp exec.php
fiHack This Site Extbasic 5 Code Breakdown
We don’t need to break down the PHP code as that is the code we’re trying to amend with the shell script. So let’s break the shell script down line by line.
First, as with all shell scripts, we get a comment to explain that it is in fact a shell script. Nothing out of the ordinary here.
!/bin/shNext, we have the ‘rm’ command which on Linux means to remove something and after a bit of research, it appears that it is the same on FreeBSD too. So this line is saying remove ok.
rm OKThe next line is using the sed (stream editor) command which appears to be what is substituting eval for safeeval. It is then passing the exec.php file to the sed command using a less than sign. After that, it appears to be taking the results of the sed command and appending them to ‘tmp’ and creating a file.
sed -E "s/eval/safeeval/" <exec.php >tmp && touch OKNext, we appear to have some logic that checks if the command executed ok, and if it did it moves on to the next line.
if [ -f OK ]; thenFinally, the script removes exec.php and moves tmp to exec.php.
rm exec.php && mv tmp exec.phpHack This Site Extbasic 5 Solution
The final line is the end of the if statement so we don’t need to explain that any further. Upon closer inspection and reading the Wikipedia page for sed it appears substitutions with sed requires 2 characters. First, it explains that in some cases you need to start the argument with -E. This is true on MacOS which is a variant of free BSD. We know Sam is using free BSD so the -E at the start of his sed statement is correct. However, we also need the characters s and g. The s character tells sed to substitute one word for the other (eval with safeeval). The g character tells it to do it globally. In short, Sam needs a g at the end of his sed statement to replace all instances of eval with safeeval. The correct syntax should be as follows.
sed -E "s/eval/safeeval/g" <exec.php >tmp && touch OKWithout the g, the script only replaces one instance of eval. The script has multiple instances of eval so the script fails to complete its purpose. Fun challenge.