Hell world, welcome to haxez. We have done it, we have made it to the Javascript 7 mission or the last Javascript mission on Hack This Site. After all those other missions I feel like I’m a scripting savant. Ok maybe not, but progress is progress. Furthermore, once we have completed this mission, we can move on to other more exciting missions. This mission is a lot like one of the previous missions that we did. However, instead of the password being encoded or obfuscated, this time the whole script is obfuscated.
Javascript 7 Introduction
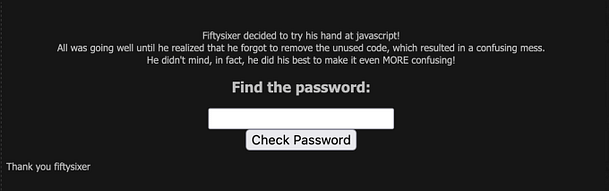
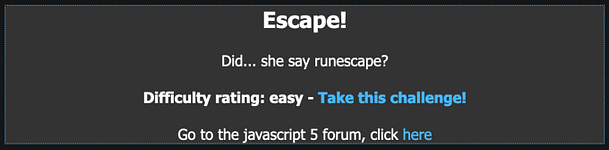
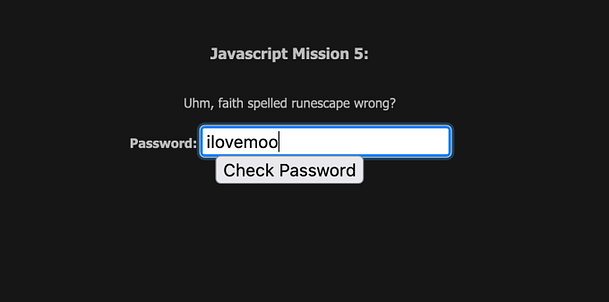
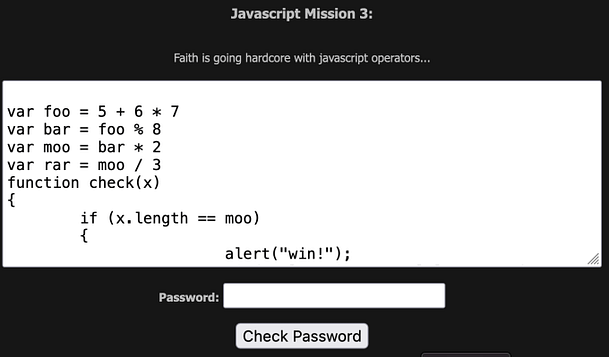
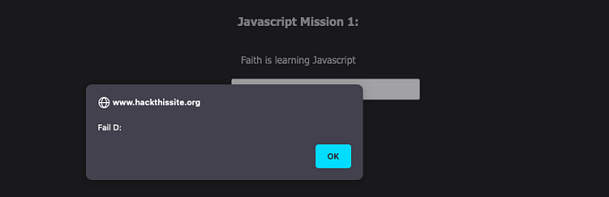
Navigating to the mission we can see a password input form. There isn’t much more information than that other than the title and a thank you message to the creator. If we submit test data to the password input form then we will get an incorrect error message. In order to see what’s going on, we need to view the page source of the application.
The Javascript
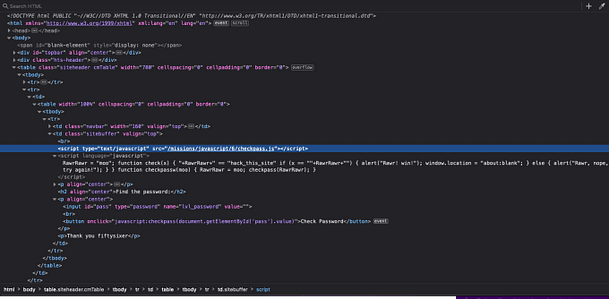
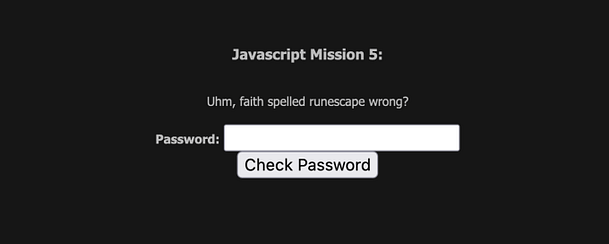
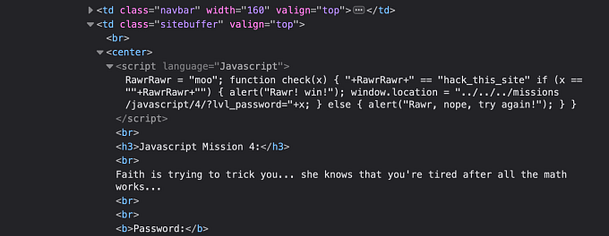
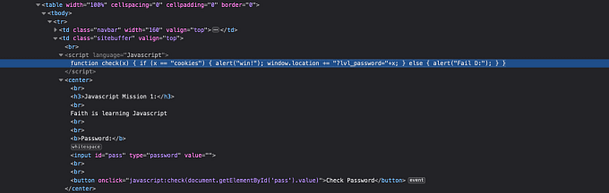
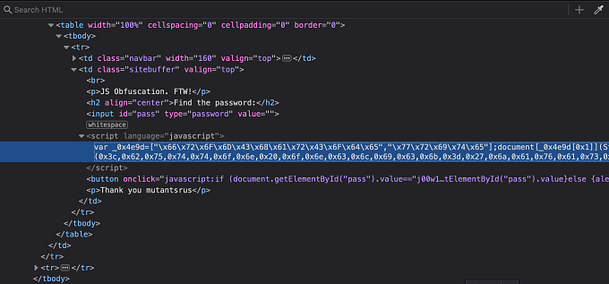
As you can see from the image below, the script appears to be garbled data. It’s all X’s followed by two-digit numbers. We could attempt to decode it online but there is a far easier solution. All we need to do is to right-click the Check Password button and inspect the functionality behind that.
The Button Javascript
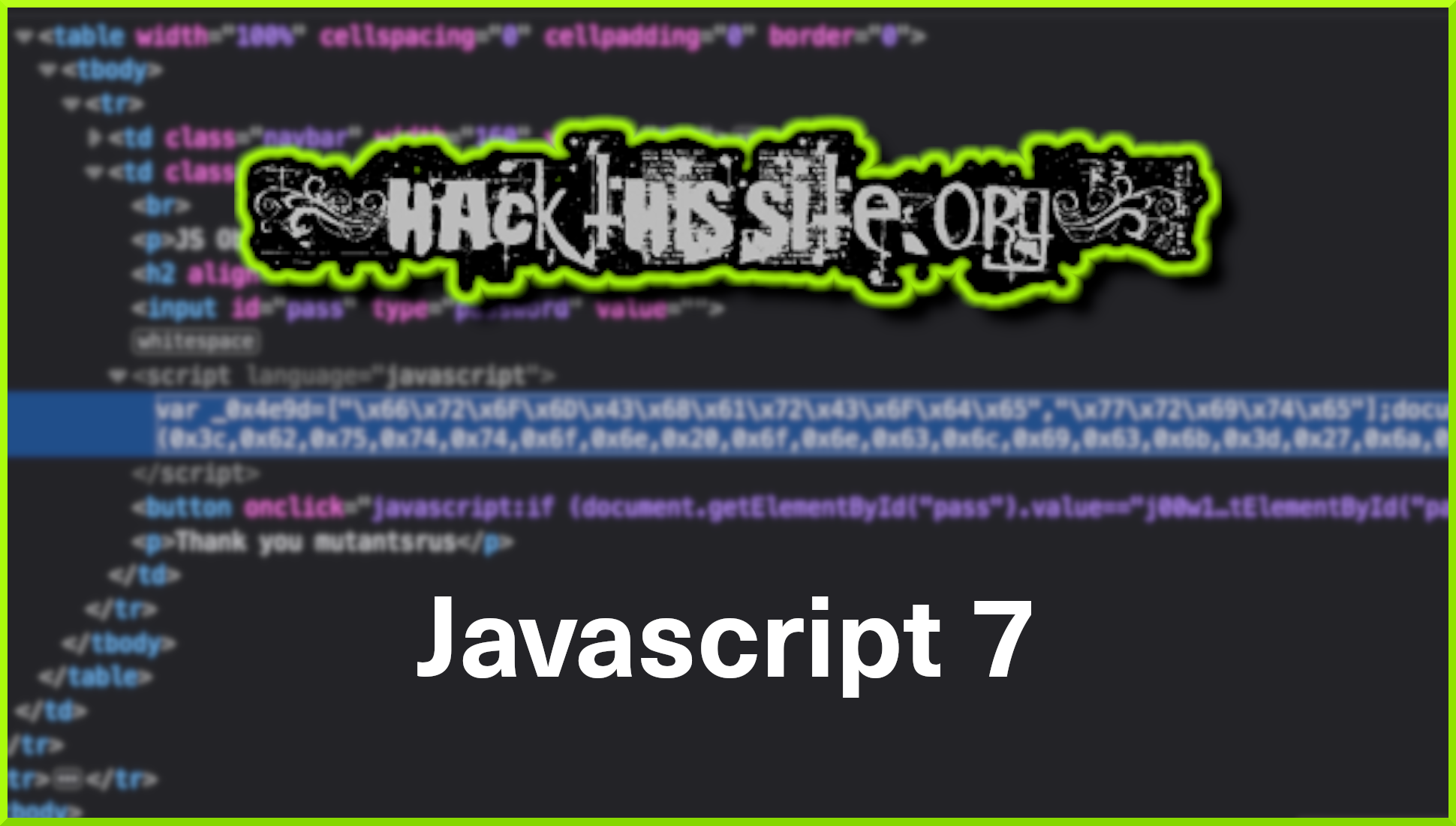
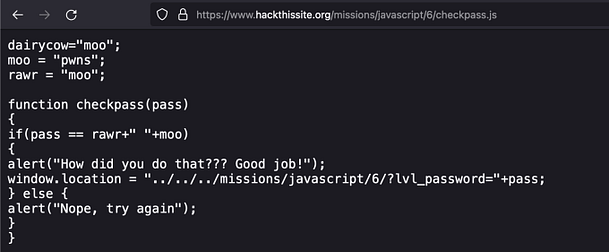
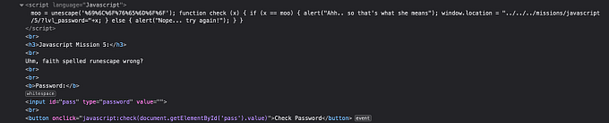
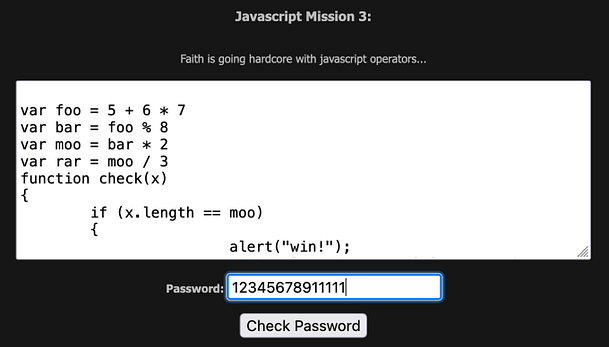
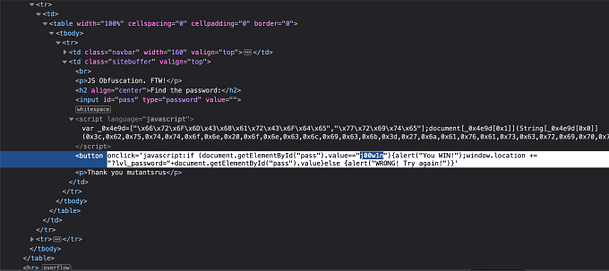
As you can see from the screenshot below, inspecting the button shows us the Javascript that is powering it. The Javascript is checking the value of user-submitted value ‘pass‘ to see whether it matches the value ‘j00w1n‘. If the values match then we get an alert saying “You WIN!”. If it doesn’t match then we get a message saying “WRONG! Try Again”.
The Javascript 7 Solution
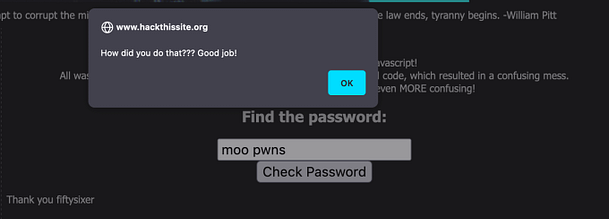
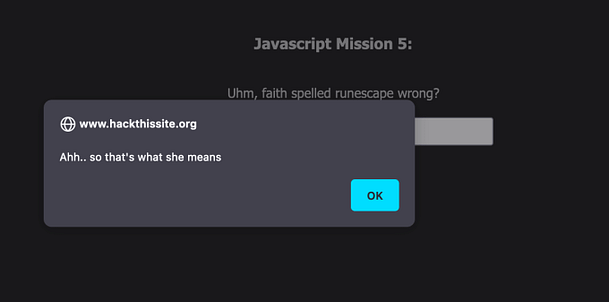
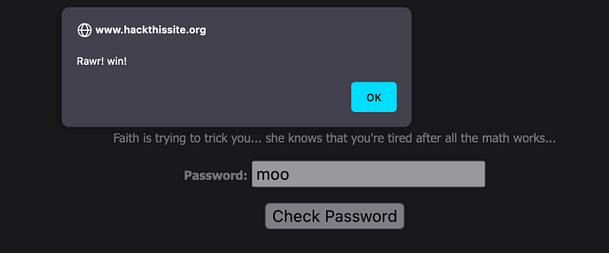
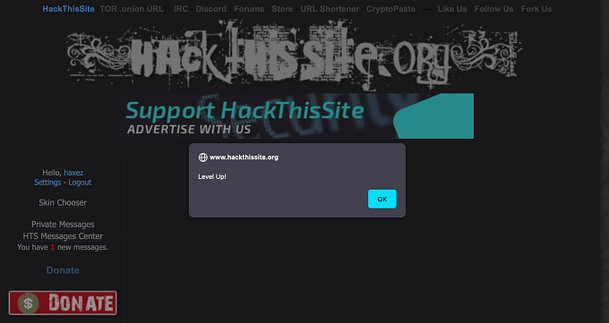
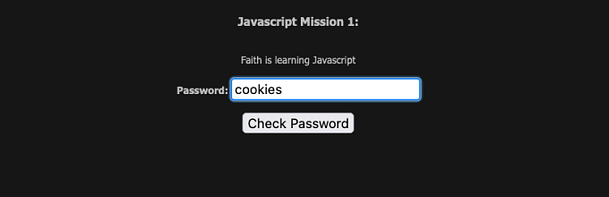
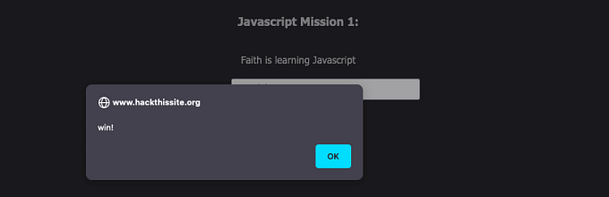
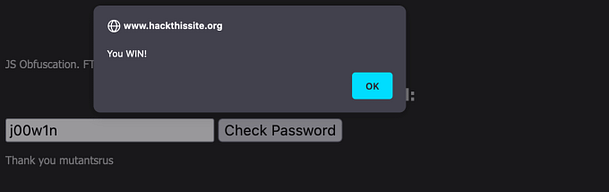
Therefore, in order to complete this mission and to complete the Javascript series. All you need to do is submit the value ‘j00w1n‘ to the password form. As you can see from the image below, we get the alert box that tells us that we have successfully completed the mission.
Alernative Method
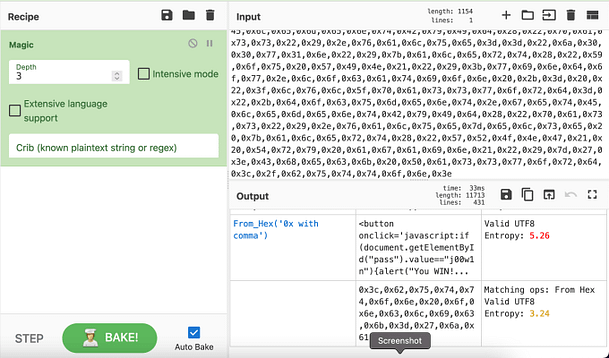
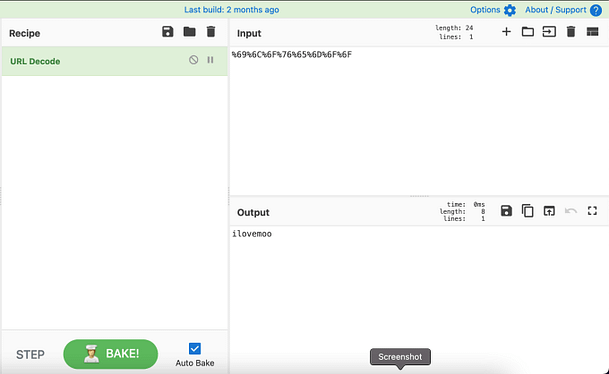
I’m sure the developers didn’t intend for this mission to be this easy. I fully believe that they wanted us to deobfuscate the code. So for that reason, the screenshot below shows me deobfuscating the code using the GCHQ tool CyberChef. As you can see from the screenshot, the output shows the button value with the password.