Delivery is an easy Linux box created by IppSec on Hack The Box and was released on the 09th Jan 2021. Hello world, welcome to Haxez where today I will be explaining how I hacked Delivery. To complete this box it is recommended that you have basic web enumeration and brute force skills. By completing this box you will learn email impersonation and intermediate password-cracking skills.
Delivery Service Enumeration
First, I connected to the Hack The Box VPN and spawned the Delivery box. After receiving the IP address, I sent it a ping to check that it was online. The box responded to my ping so I performed a Nmap scan to check all ports, request service versions and run default scripts. I set the minimum packet rate to 10000 packets per second and saved the output in all formats. As a result, I learnt that port 22 for Open SSH 7.9, port 80 for Nginx 1.14.2 and port 8065 for an unknown service were open. Furthermore, the SSH banner suggested that the OS was Debian.
┌──(kali㉿kali)-[~/HTB/Delivery]
└─$ sudo nmap -sC -sV -p- 10.129.207.229 --min-rate 10000 -oA Delivery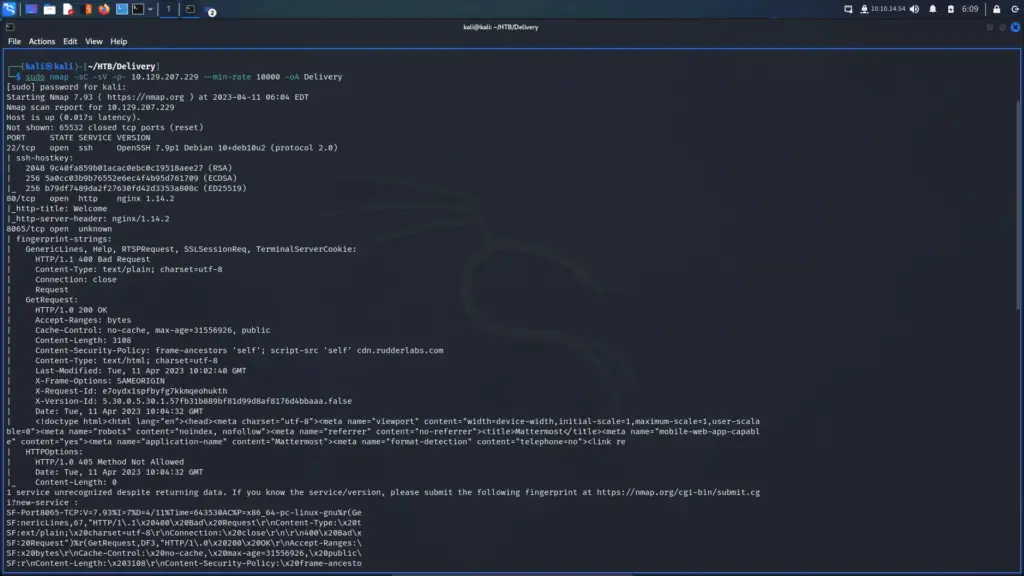
Delivery Web Application Enumeration
I navigated to the application on port 80 by visiting the IP address in my browser. After the application loaded, I saw that it was HTML 5 application that had two options. The first one I looked at was the contact us page. In short, the contact us page explains that unregistered users need to use the help desk to have an email address created. Once the email address has been created, the user will be able to access the MatterMost server.
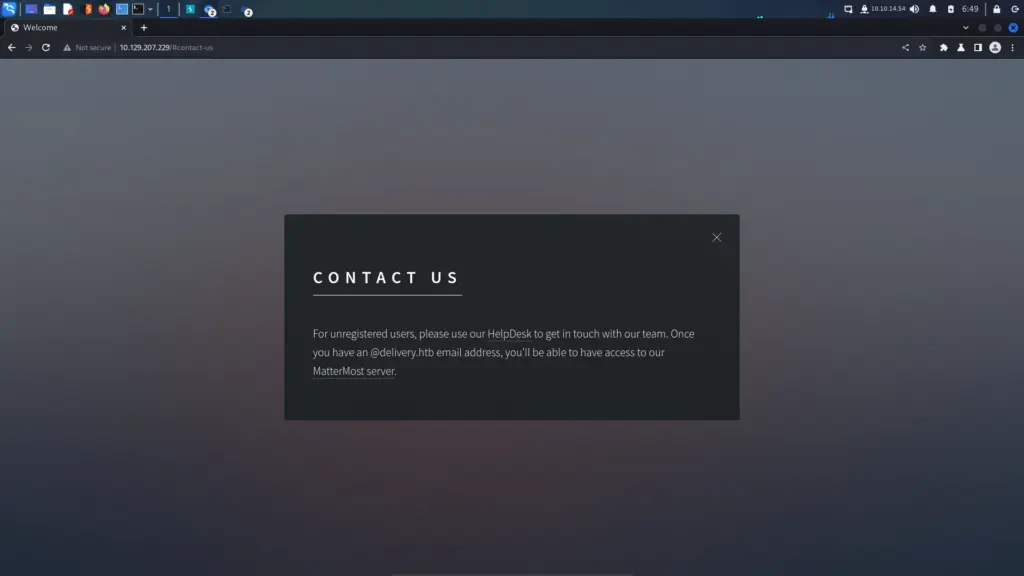
Next, I clicked the link for the MatterMost server but received an error. The application was redirecting to the domain delivery.htb on port 8065 (the mystery port). However, since that domain doesn’t exist in the real world it can’t resolve. I will fix this in a moment. The other link on the application was for the helpdesk. However, upon clicking the link I received an error as it was also trying to load a domain that didn’t exist.
In order to rectify this, I added the hostname to my host file through the use of echo and tee. Echo will echo the data you provide back to you. Tee will read from standard input and write to standard output and files. After adding the domains to my host file, I refreshed the page and was able to view the intended applications.
┌──(kali㉿kali)-[~/HTB/Delivery]
└─$ echo "10.129.207.229 delivery.htb helpdesk.delivery.htb" | sudo tee -a /etc/hosts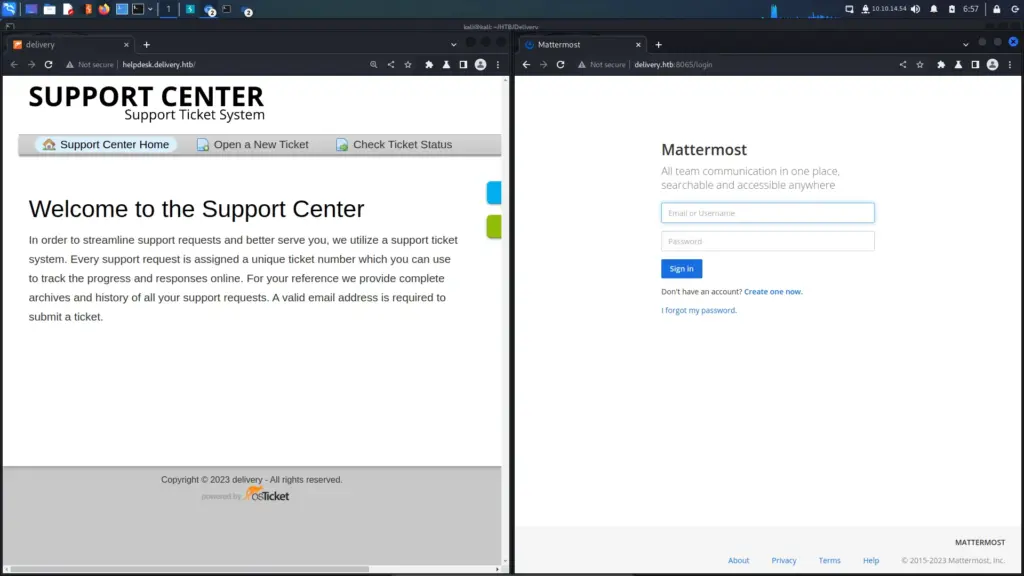
Exploiting The Ticketing System
I decided to create a new ticket to test the functionality. First I populated the contact information with bogus data. Then, I completed the CAPTCHA text and clicked Create a ticket. After creating the ticket the web application produced a response advising me of my ticket number. However, the application also informed me that I could reply to the ticket by emailing the address 4092106@delivery.htb. The mailbox appears to be created dynamically for use with the ticketing system.
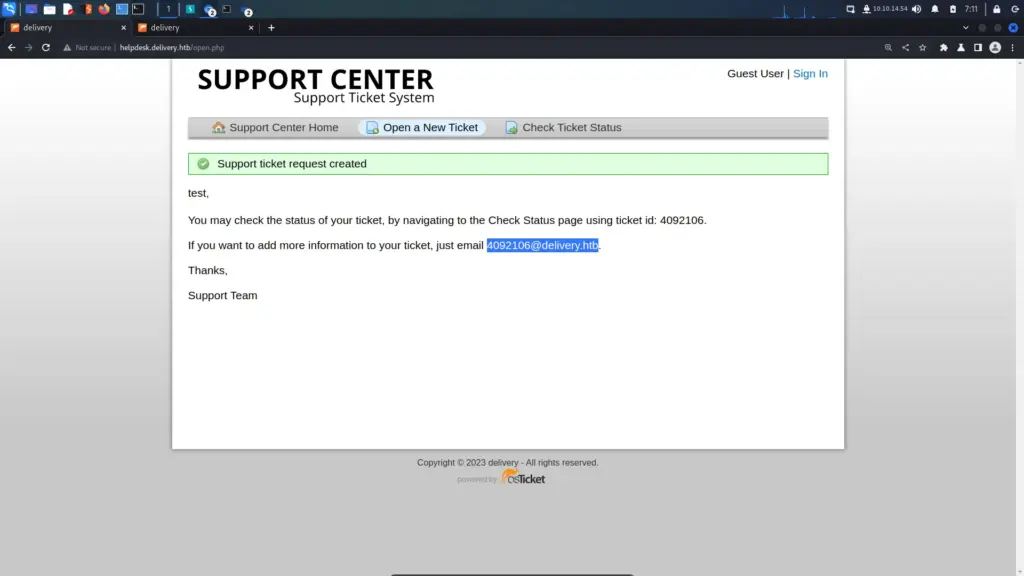
The MatterMost application required a corporate email address to sign up. I now had a corp email address where I could view its emails through the ticket system. I headed back to the MatterMost application and signed up with the 4092106@delivery.htb email address. Then, MatterMost responded and said that I needed to verify my email address (as most online sites do). I headed back to the ticketing system and could now view the verification email.
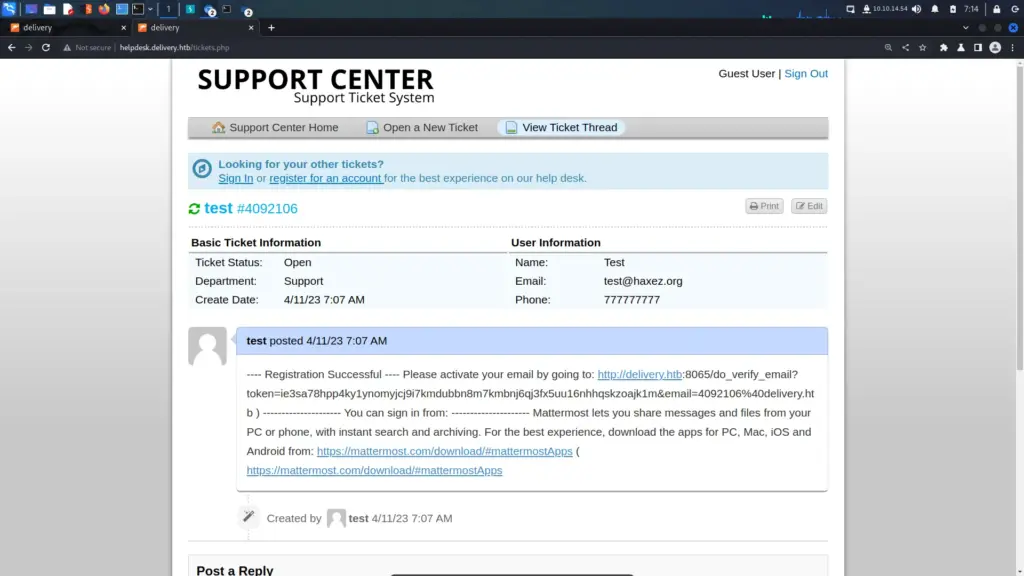
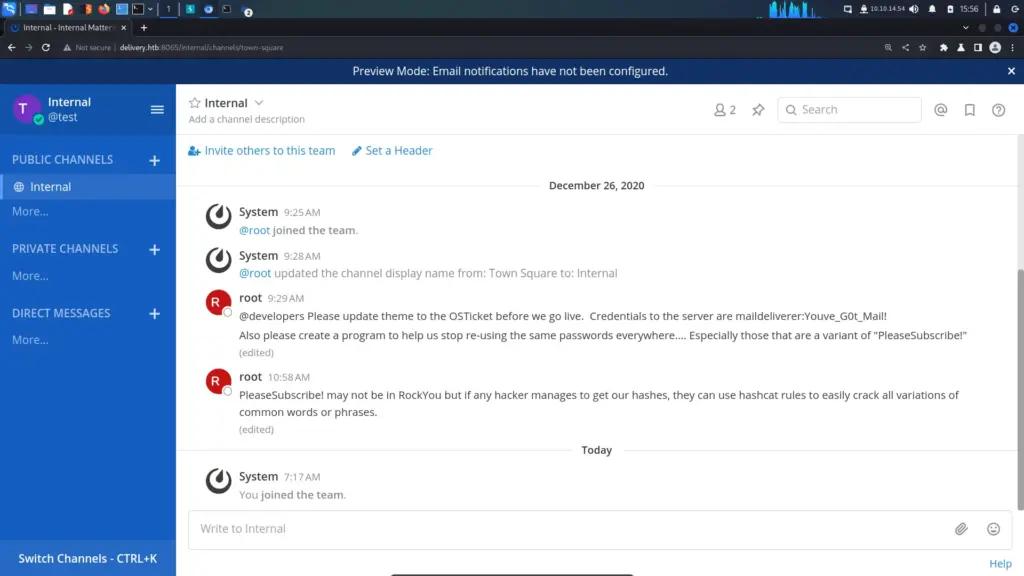
Exploring MatterMost
After logging in to MatterMost, there was an option to join the Internal channel. Joining the channel and reading through the messages I learnt that maildeliverer user had a password of Youve_G0t_Mail!. Furthermore, the root user has asked for a program to prevent password reuse. They go on to explain that while certain words may not be found within a wordlist, hashcat rules can be used to crack variations.
With the credentials found in the MatterMost application, I was able to SSH to the box as the maildeliverer user. Once on the box, I was able to capture the user.txt flag.
┌──(kali㉿kali)-[~]
└─$ ssh maildeliverer@10.129.207.229
maildeliverer@Delivery:~$ pwd
/home/maildeliverer
maildeliverer@Delivery:~$ ls
user.txt
maildeliverer@Delivery:~$ cat user.txt
29f▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓8f3Delivery Host Enumeration
Since MatterMost is a database-driven web application, there must be a database connection configuration file on the box. After a bit of poking around, I found the database connection details within the /opt/mattermost/config/config.json file in the SqlSettings section.
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/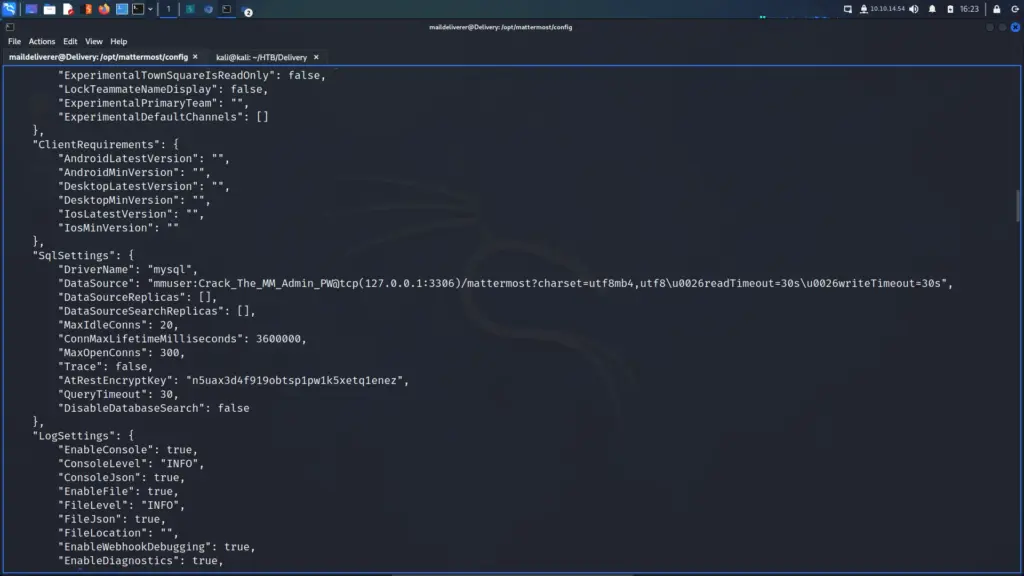
With the credentials, I was able to log in to MariaDB and query the databases. First, I asked MariaDB to show me the databases. As a result, I learnt that there was a database called mattermost. Next, I told MariaDB to use that database and asked it to show me the tables. The results revealed that there was a Users table. I then asked MariaDB to describe the table so that I could get the columns. Finally, I dumped the contents of a few columns from the Users table.
maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -p
MariaDB [(none)]> show databases;
MariaDB [mattermost]> show tables;
MariaDB [mattermost]> describe Users;
MariaDB [mattermost]> select Id, Username, Password from Users;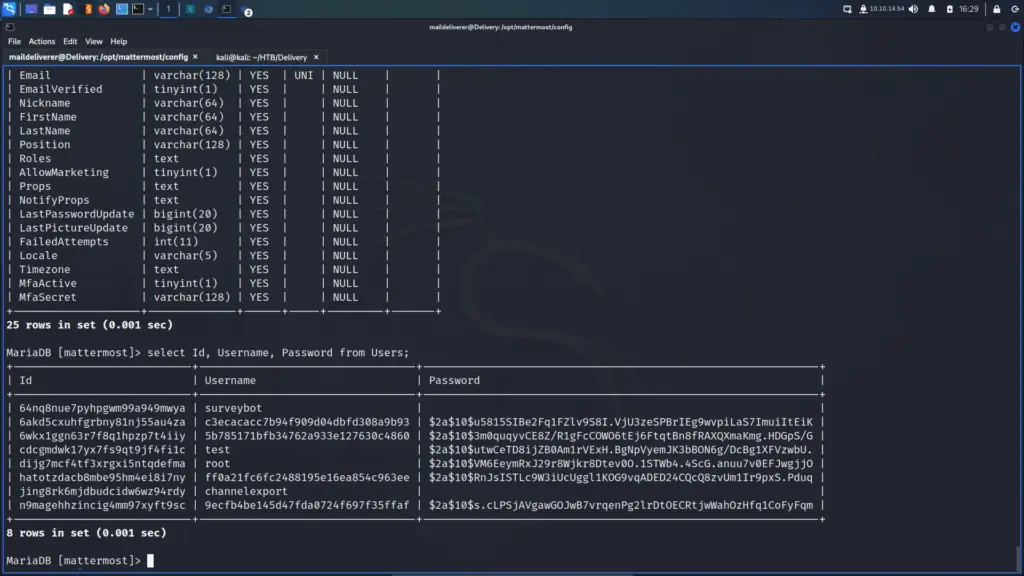
Delivery Privilege Escalation
The Users table included the password hash for the root user. After a bit of searching, I learnt that the type of hash was a bcrypt hash. I tried to blast the hash with rockyou.txt but after watching IppSec’s video I learnt that it wouldn’t work. Instead, I took the PleaseSubscribe! password from the MatterMost server and saved it to a file. I then saved the hash to a file and used hashcat with the best64.rule file to crack the hash.
┌──(kali㉿kali)-[~/HTB/Delivery]
└─$ hashcat -m 3200 hash.txt password.txt -r /usr/share/hashcat/rules/best64.rule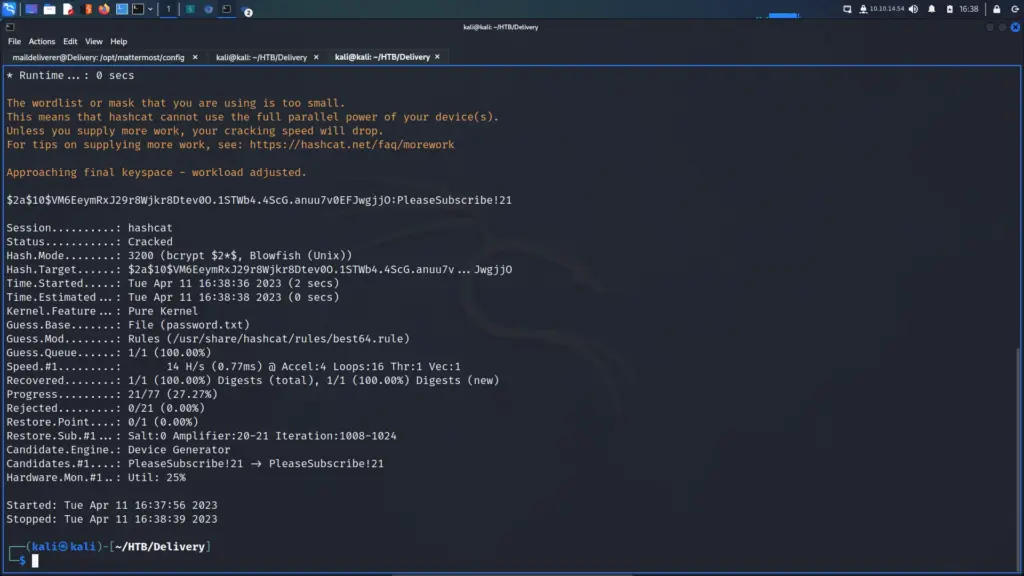
With the password cracked, I was able to switch to the root user and capture the root.txt flag and complete the box.
maildeliverer@Delivery:/opt/mattermost/config$ su root
Password:
root@Delivery:/opt/mattermost/config# cat /root/root.txt
bb6▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓6beDelivery Learnings
I thought this was a rather unique box compared to other boxes that I’ve completed. The initial foothold didn’t exploit a known vulnerability or configuration issue. It was more about understanding the psychology of the person who created the environment and exploiting their oversights. I thought it was really interesting and hopefully, it has changed the way I will think about security in the future.
The privilege escalation was great, I haven’t used hashcat rules before so I got to learn something new. All I want from completing a box is to learn something new or reinforce existing knowledge. This box fulfilled both of those so I’m happy. I don’t think I would have been able to complete this without the walkthrough but it’s hard to say. Thanks for the Box.

