Hello World and welcome to haxez, today we’re going to be looking at Hack This Site Extended Basic 6. Solving this challenge requires some basic knowledge of PHP or any other language for that matter. It’s a simple challenge that shows how poorly coded web application authentication mechanisms can be bypassed.
The Extended Basic 6 Challenge
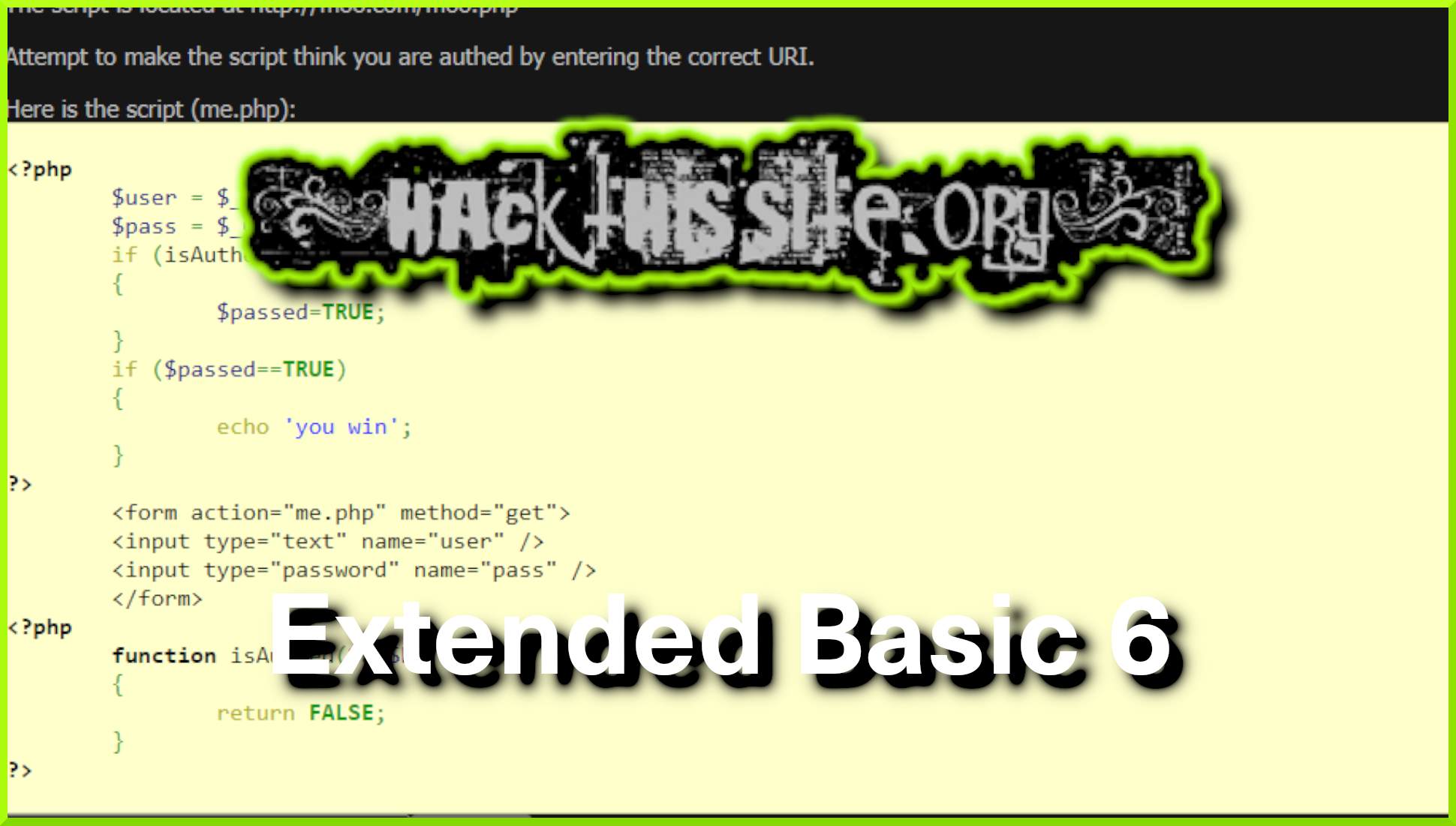
The image below shows the PHP that makes up the authentication mechanism. Furthermore, This is the code that we need to exploit in order to bypass the authentication mechanism. The introduction text at the top explains that the sysadmin is a noob and that the script is located at http://moo.com/moo.php. Therefore, to solve this challenge we need to append the correct syntax to the end of the URL and submit it to the submission form.
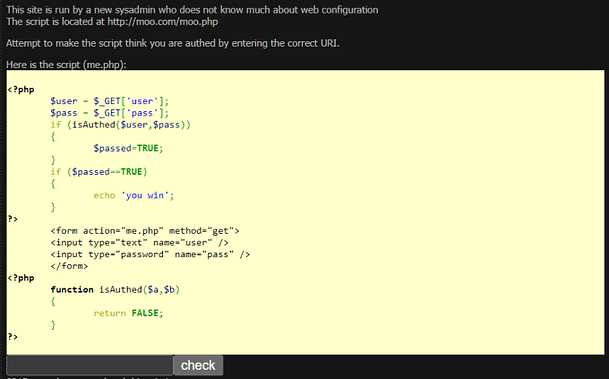
The PHP Code
The snippet below is the exact code we’re going to be exploiting. Furthermore, there is no backend database to worry about, just some simple PHP logic that we can leverage for our own nefarious purposes.
<?php
$user = $_GET['user'];
$pass = $_GET['pass'];
if (isAuthed($user,$pass))
{
$passed=TRUE;
}
if ($passed==TRUE)
{
echo 'you win';
}
?>
<form action="me.php" method="get">
<input type="text" name="user" />
<input type="password" name="pass" />
</form>
<?php
function isAuthed($a,$b)
{
return FALSE;
}
?>Breaking Down The Code
We’re going to break the code down line by line in order to solve this challenge. Once we understand what the code is doing, we will be able to use its own logic against it and bypass authentication.
First, the code starts with it a tag telling us what language it is.
<?phpNext, we have two variables being set from user input. The $user and $pass variables are populated by the values of ‘user’ and ‘pass’. This is more evident later on when looking at the HTML form.
$user = $_GET['user'];
$pass = $_GET['pass'];This is where the logic beings. When the user submits their username and password, the data is passed to an if statement. If the values of the variables ‘$user’ and ‘$pass’ are correct then the variable ‘$passed’ is set to true.
if (isAuthed($user,$pass))
{
$passed=TRUE;
}After that, the application uses another if statement to check whether the value of the variable ‘$passed’ is set to true. If ‘$passed’ is set to true then the application echos out “you win”. This also ends the first section of PHP.
if ($passed==TRUE)
{
echo 'you win';
}
?>Now, we move on to the HTML. This is the login form that the user will send when loading the page in their browser. It is fairly standard and just performs a get request to me.php. The contents of the get request or the values of the input for ‘user’ and ‘password’. The user input type is text and the password input type is password.
<form action="me.php" method="get">
<input type="text" name="user" />
<input type="password" name="pass" />
</form>Finally, we have the last section of PHP. This is the function that checks to see whether the username and password are correct. This function compares the values of variables ‘$user’ and ‘$pass’ with the variables ‘$a’ and ‘$b’. If they match then it is the first if statement is executed.
<?php
function isAuthed($a,$b)
{
return FALSE;
}
?>The Extended Basic 6 Solution
With that rather long explanation out the way, we can now move on to solving the challenge. It’s pretty simple if you know how to PHP site URL’s work. We know that in order for us to authenticate, the variable ‘$passed’ needs to be set to ‘TRUE’
PHP allows you to specify variables and their contents in the URL. For example, a dynamic PHP website using a CMS like WordPress may have a URL like HTTP://site.com/index.php?page=1. The question mark indicates that what follows is a variable and in this case, the variable is ‘$page’. Furthermore, we can specify that we want the value of the page variable to be 1.
With this in mind, we can take the provided URL of HTTP://moo.com/moo.php and append a question mark followed by the variable passed equals TRUE, as seen below.
http://moo.com/moo.php?passed=TRUESubmitting this to the input box will solve the challenge.