Hello World, welcome to haxez where today we will be looking at the Javascript Mission 5 on Hack This Site. This mission was a lot of fun and even gave me an excuse to use the GCHQ CyberChef tool to deobfuscate some encoded text. The mission is fairly simple provided you know what to do with the data that you find.
The Javascript 5 Mission
Upon navigating to the mission we are greeted with a password input form and some text asking if Faith spelled Runescape wrong. This comes into play a bit later as it is referencing a Javascript function that is used to encode or decode text. We could input some text into the password form and submit it but without the correct text, we will get an error message to notify us that the password is wrong.
The Javascript 5
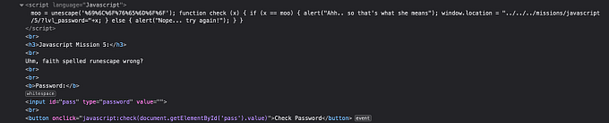
However, If we inspect the password form or view the page source we can see the Javascript. Furthermore, the first part of the script is declaring a variable named ‘moo‘ and says that it is equal to unescape. The ‘unescape()‘ function computes a new string in which hexadecimal escape sequences are replaced with the character that it represents. In addition to the declaration of the ‘moo‘ variable and the ‘unescape’ function we have the following encoded string ‘%69%6C%6F%76%65%6D%6F%6F‘.
Javascript Deobfuscation
In order to decode the string, we can use our favorite Government developed decoding tool, CyberChef. Surprisingly, CyberChef works really well considering it came from the public sector (please don’t arrest me). As can be seen from the image below, the interface is simple. You choose a recipe, then paste in your encoded text, and then it works its magic and decodes it for you. It even has a magic recipe that will automatically detect what you’re inputting. It really is a great application.
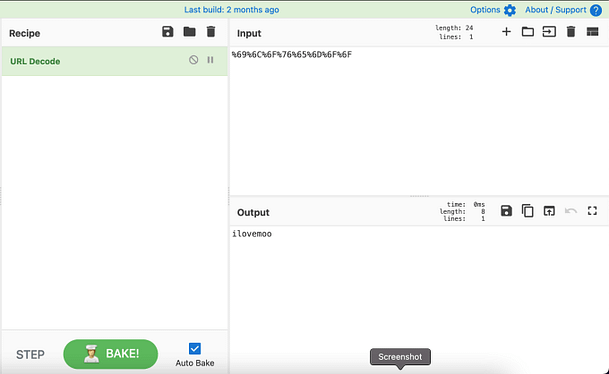
The Solution
As shown above, the decoded text turns out to be ‘ilovemoo‘. If you submit that to the password form then you should complete the mission.
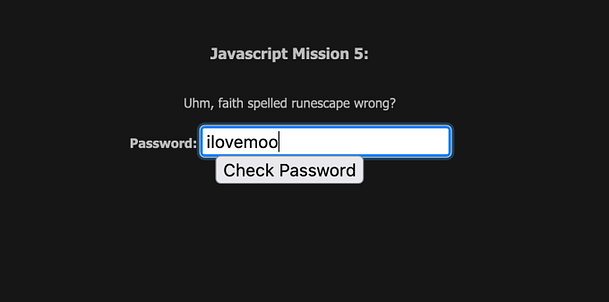
Congratulations you have now completed Javascript mission 5.