WayWitch is a very easy web challenge created by Xclow3n on Hack The Box. To complete this challenge you need an understanding of JWT. Hello world, welcome to haxez where today I am going to complete the WayWitch web challenge. This challenge was a lot of fun and was fairly easy to complete. While I already understood JWT, it was good to refresh that knowledge.
WayWitch Application Enumeration
To load the application, I needed to specify HTTPS. The challenges I have completed so far have all been HTTP. Attempting to connect via HTTP returned a connection reset error. After loading the application, it was evident that it was some type of ticketing system. There was no login or any other functionality.
Source Code Review
The web challenges allow you to download the source code. This allows for a white box style assessment in that you get to see the code behind the application. After downloading the zip file, I opened the routes.js. The routes file typically controls the logic behind navigating the application. For example, index.html is a route. As you can see below, there is a route for tickets.
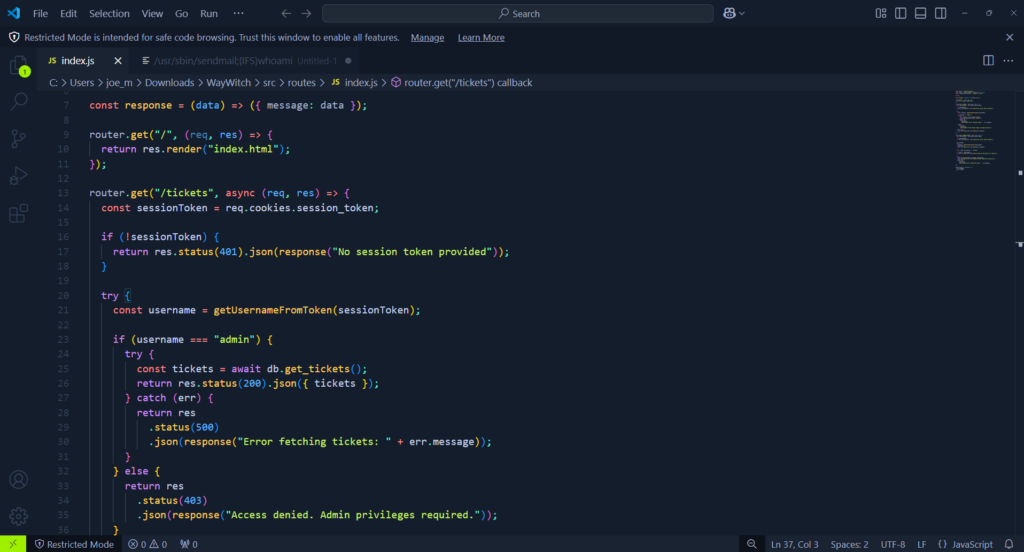
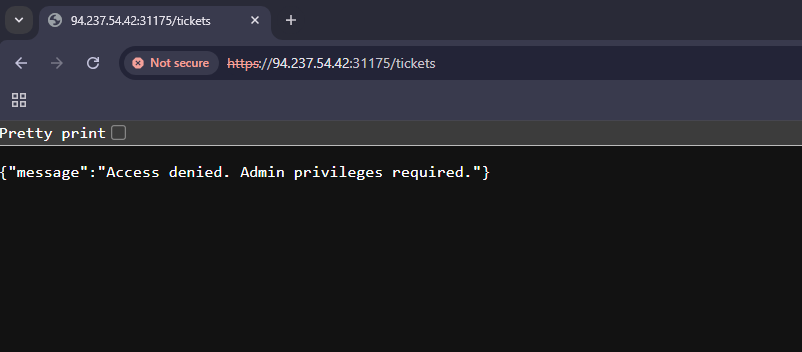
I attempted to navigate to the tickets route or page and received an error explaining that access was denied and that admin privileges were required. This was expected as the source code of the application has an if statement based on the contents of the session token. As seen above, the if statement checks the session token to see whether username is equal to admin. If it matches, it will allow the user to view the tickets route. With that in mind, I knew that I could forge a JWT cookie to contain the username admin. However, in order to do that we need the JWT secret signing key.
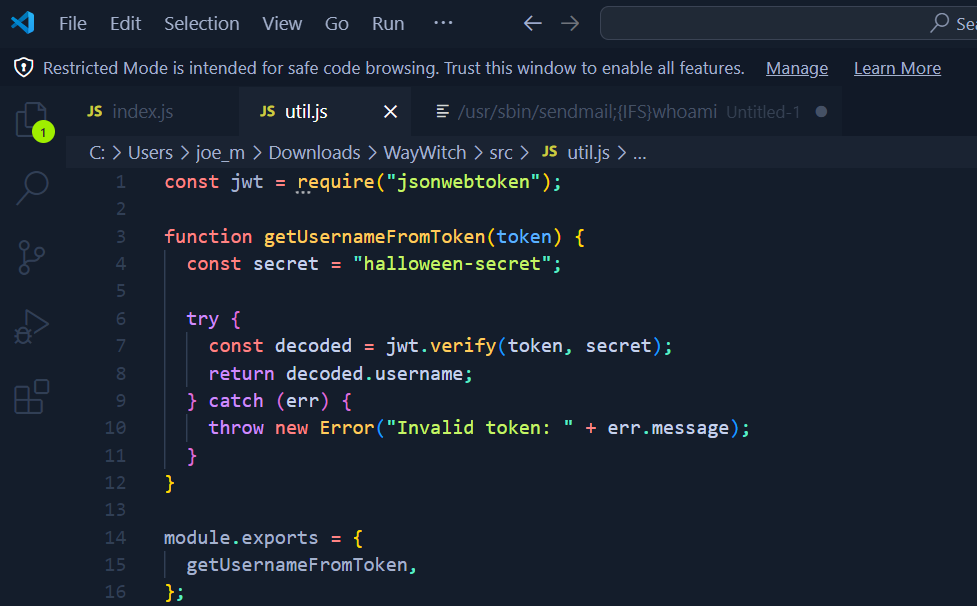
WayWitch Secret
I opened the util.js code and the secret was there. Furthermore, the secret can also be obtained by inspecting the web applications page source. This demonstrates why it is always important to view the page source of an application when testing it. This is something I neglect to do more than I care to admit. However, with this example now demonstrating the importance of doing so, I will be sure to be more diligent.
Forging The JWT
I took the existing cookie from my browser by inspecting the page and heading to the application tab. From there I took the value of the session_token cookie and pasted it in to jwt.io. Next, I updated the username to admin and changed the secret key to the one found in the source code (halloween-secret).
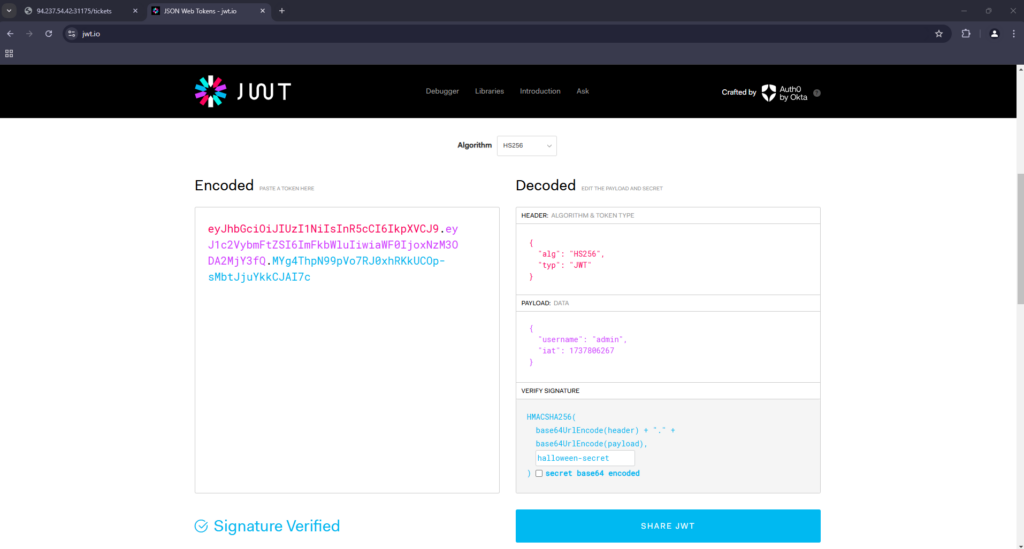
I then copied the returned encoded JWT and pasted it in to the value of the session_token in my browser. Next, I refreshed the page and the spooky black magic had worked. I now had access to the tickets route and could see all the tickets that had been previously submitted. Furthermore, the tickets contained the flag thus allowing me to solve the challenge.
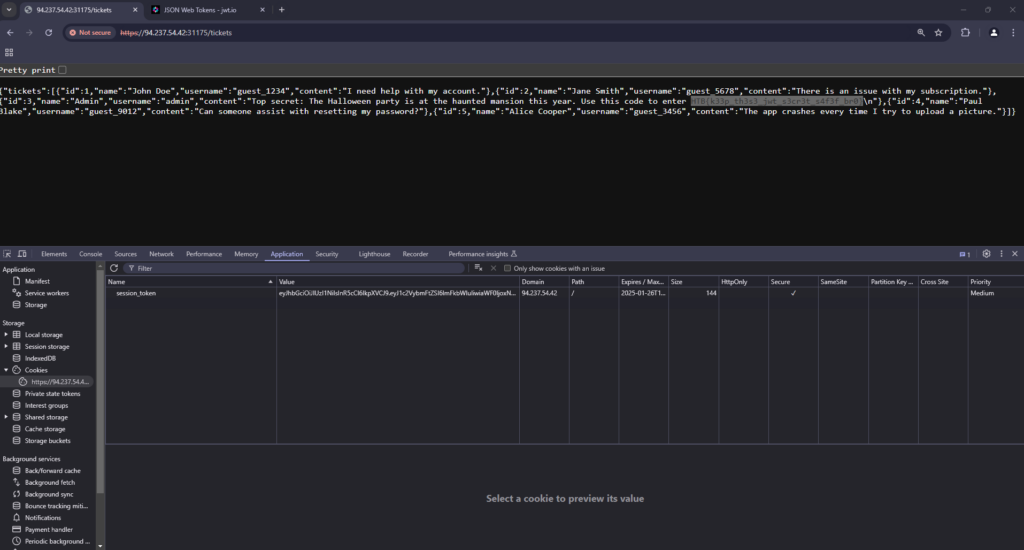
HTB{k33p_th3s3_jwt_s3cr3t_s4f3f_br0}WayWitch Learnings
This was an very fun challenge. It wasn’t too difficult and the code was easy to understand. It was very obvious that in order to access the tickets page, I needed to meet the conditions set out in the if statement (having the username be admin). With that said, I believe that if I hadn’t found the JWT secret in the page source, I might have got stuck for a bit trying to submit the new cookie without the secret. This was another great web challenge and I’m enjoying going through them. I suspect I will start hitting a wall when I get to the easy and medium challenges.

