Hello world, welcome to haxez where today we’re looking at Hack This Site Realistic Web Mission 13. This is a fun challenge that requires you to gather information from error messages. After obtaining that information, you need to discover the hidden URL to access the admin area. Ultimately, this mission requires knowledge of web application errors, password hashes, and hash cracking. If you haven’t seen my other posts on the realistic series you can do so here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7 and, Part 8.
Realistic 13 Introduction
We’ve received a message from Fr0zenB1t which explains that they are part of Anarchists of Elbonia. The reason for the message is because they would like us to thwart the upcoming election by hacking into their competitor’s web application. Furthermore, they explain that hacking into the application and taking it down, even temporarily could help delay the election.
Exploring The Realistic 13 Web Application
The application is fairly basic. Notably, we have a navigation menu with a number of links. In the center, we have the content of those links. There is a mailing list that allows you to submit your email address but it isn’t vulnerable to any type of injection.
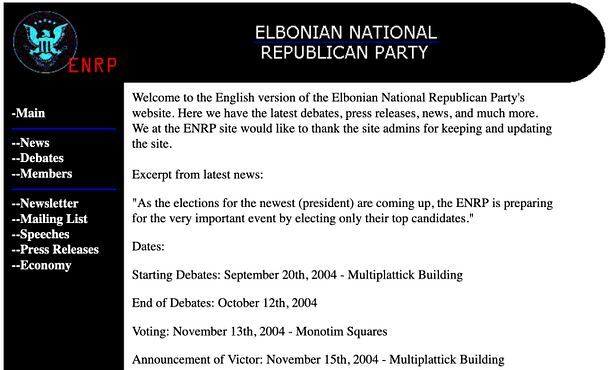
The newsletter page has some interesting information that is worth making note of. It claims that there is a hidden login URL that requires a password. We could brute force the hidden URL using tools like DIRB or Go-Buster. However, that could take a long time depending on the naming of the directory.

Web Application Errors
If we poke around on the pages a bit more and append question marks to the end of the URL, we can generate errors. This is possible because the pages are expecting something after the question mark. The image below shows an error on the Press Releases page. Notably, the error mentions the file path '/speeches/passwords;. However, it also mentions '.md5('Speeches')'. This suggests that there is a directory named with the md5 hash of the word Speeches.

Realistic 13 Hashing The Path
In order to discover what this directory is called, we need to create an md5 hash of the word Speeches (case sensitive). It is important to note that when creating the hash, you need to include the '-n' flag. Otherwise, the hash will be created with a newline resulting in the hash being completely different from the intended one. The code below demonstrates how to create an md5 hash from the word Speeches in bash.
Josephs-MacBook-Pro:~ Joe$ echo -n Speeches | md5
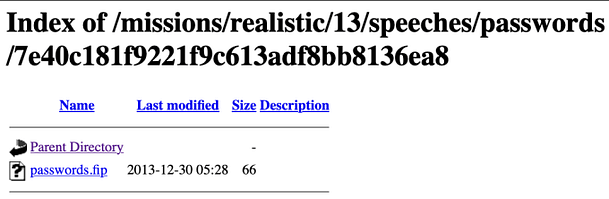
7e40c181f9221f9c613adf8bb8136ea8After creating the hash, we can append it to the URL after '/speeches/password'. Visting that URL will produce a directory listing showing a 'passwords.fip' as shown in the image below.
Clicking on the link to the file will open it in your browser. The file contains a long string or two strings separated by a colon. The strings appear to be password hashes. We could guess what the hashes are likely to be from the length of them.
7bc35830abab8fced52657d38ea048df:21232f297a57a5a743894a0e4a801fc3Realistic 13 Hash Identification
Or we could use a hash identification tool. I found such a tool on homebrew called name-that-hash. It’s a simple tool that is easy to install and use. By analyzing the hash we are able to identify that the most likely candidate for the hash is an md5. With this information, we can attempt to crack it to reveal what the unencrypted string is.
name-that-hash -t '7bc35830abab8fced52657d38ea048df'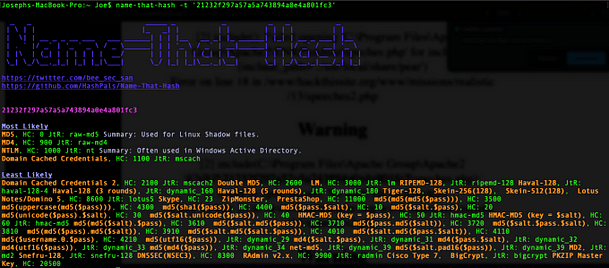
Cracking The Hash
Hashcat is a popular password cracking tool and can also be found via the homebrew website. By placing the discovered hashes into a text file, we can ask Hashcat to crack the hashes for us. I used the wordlist rockyou.txt to crack the hashes. I have included the syntax and a screenshot of the cracked hashes below.
hashcat –m 0 hash.txt /path/to/wordlists/rockyou.txt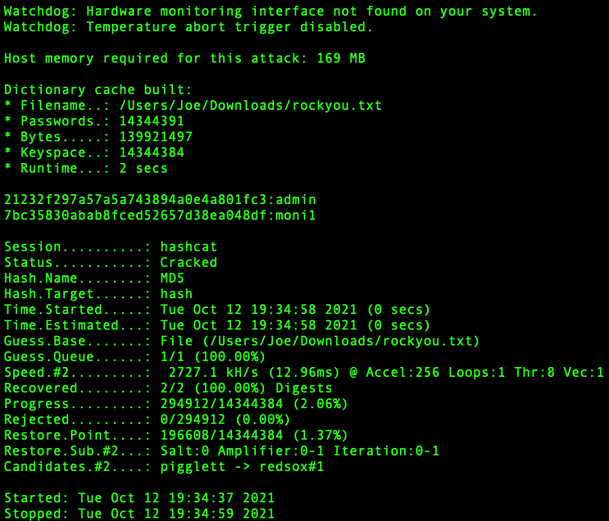
The results are in and we have our two words. They appear to be a username and password combination.
21232f297a57a5a743894a0e4a801fc3:admin
7bc35830abab8fced52657d38ea048df:moni1With the hashes cracked, we can head to the admin area and attempt to log in. However, neither combination of the username and password works. We have been bamboozled.
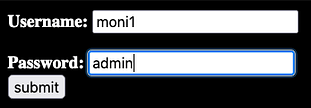
Web Application Complete
Remember back to the press release page where it suggested there was a secret directory? what if they weren’t referring to the md5 Speeches directory. What if the /admin login page that we’re attempting to login to is fake? It turns out that it is fake and that the correct directory is the md5 hash of the word admin. By appending ‘21232f297a57a5a743894a0e4a801fc3’ to the URL, you get the proper login page and with that, you complete the mission.
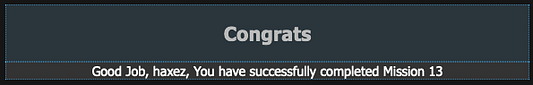
Conclusions
This was a fun challenge that shows the importance of minimizing information disclosure on web applications. It also shows the importance of using a strong encryption mechanism. Anyway, with that, I’m done. Feel free to check out the video below. Thanks.

