Hello and welcome to haxez, today we are looking at Hack This Site Basic Web Challenge level 8. This challenge requires you to perform a Server Side Include injection in order to retrieve the password. A server side include is a chunk of code in a separate file that you can include in different pages. For example, if you had a website with a header and a side menu. You could put the header and side menu in separate files and then include them on other pages with a single line such as “<!–#include virtual=”includes/header.shtml” –>“. A Server Side Include Injection attack exploits web forms that accept user input to generate files.
If you haven’t see my previous posts in this series then you can do so here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, and Part 7.

Testing The Basic 8 Web Application
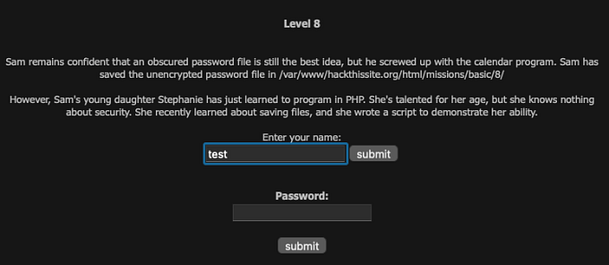
Once you’ve logged in and navigated to level 8 you will see the page below. The information reads as follows:
Sam remains confident that an obscured password file is still the best idea, but he screwed up with the calendar program. Sam has saved the unencrypted password file in /var/www/hackthissite.org/html/missions/basic/8/
However, Sam’s young daughter Stephanie has just learned to program in PHP. She’s talented for her age, but she knows nothing about security. She recently learned about saving files, and she wrote a script to demonstrate her ability.
Security Sam
There are two pieces of important information hidden in the text. Firstly, the full file path is mentioned. This suggests to me, that we will need to know the structure of the application in order to exploit it. Secondly, Sam’s daughter has been learning PHP but doesn’t know anything about security. This is likely going to be the part of the application that we need to attack. So first, we are going to submit a basic value to the application and see what happens.
As you can see from the image below, submitting the test string has written it to a shtml file. The script appears to doing same basic arithmetic to calculate the number of letters in the submitted value. However, the thing to notice here is that it’s writing to an shtml file. This suggests, that the application could be vulnerable to a Server Side Include Injection attack. It is also worth nothing that the files are written to the tmp directory but the location of the password is one directory above that.

Exploiting The Web Application
In order to exploit the application, we can submit a basic Server Side Include Injection payload. The payload is going to use the cmd directive to execute the ls Linux command. Additionally, we are going to tell the ls command to list out the files of the directory above it. When we submit the payload, the application will include it in the script that generates the shtml page. It will execute the payload and store the results in the shtml file.
<!--#exec cmd="ls ../"-->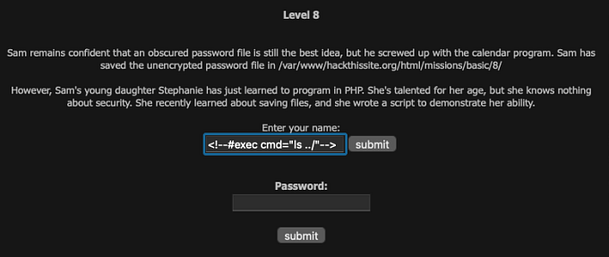
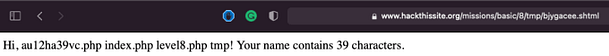
As you can see from the image below, the payload has been executed by the PHP script and the results have been stored in the shtml file. The au12ha39vc.php file appears to be the one we are looking for.
Recovering The Passowrd
Copy the file name of the php file and append it to the URL and you will be able to recover the password.
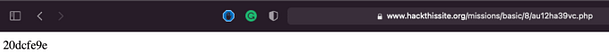
You can then go and submit the password and you will have solved the challenge.


