Hello and welcome to haxez, today we’re looking at Hack This Site Realistic Web Mission Level 4. I liked this challenge although I was confused about the syntax used to complete the mission. The mission requires you to perform a UNION ALL SQL Injection in order to grab email addresses from a database. Once you have the email address, you need to email them to the client. If you haven’t seen my other posts are the realistic series you can do so here: Part 1, Part 2 and Part 3.
The mission should you chose to accept it is to hack the FAP website and steal the email addresses of everyone on the mailing list. Why?, because FAP kills animals to sell their pelts to rich customers. SaveTheWhales has kindly asked us if we can get the mailing list and send it to him so that he may “contact them”.
Exploring The Realistic 4 Website
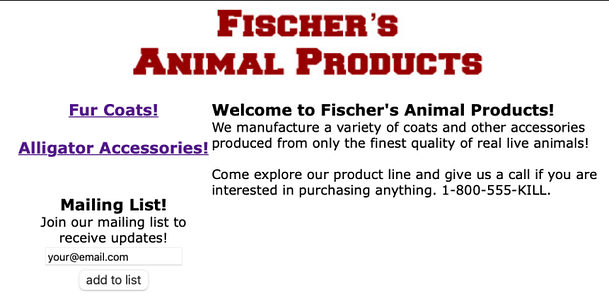
Visiting the website, you’re greeted with a fairly simple page that explains what the web application is about. There is a submission box to add your email address to the mailing list. There are also two links, one to Fur Coats and one to Alligator Accessories (poor Alligators). We could try attacking the mailing list submission system but for now, let’s continue exploring the application.
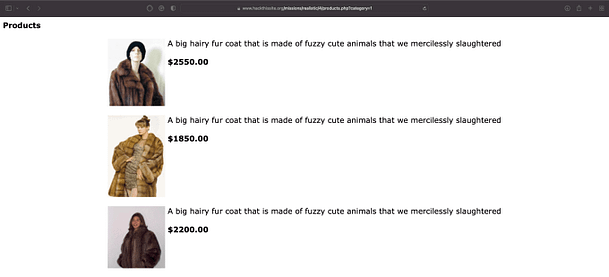
Following the Fur Coats and Alligator Accessories links takes you to the corresponding product pages. These pages appear to be dynamic, as though they were being generated by an SQL Query. If we look at the structure of the page, it can be broken down into three database columns Picture, Description, and Price. We can also assume that there is a table for email addresses.
The Website Hack
Although the application didn’t error when appending a single quotation mark. We can still attempt to perm a UNION SQL injection. The syntax for the specific SQL injection to retrieve the data confuses me slightly. For example, W3Schools and Portswigger have excellent articles on UNION SELECT and UNION SQL injections. W3Schools explains that the difference between UNION SELECT and UNION ALL SELECT is that UNION ALL SELECT will include duplicate values whereas, UNION SELECT won’t. The information that we exfiltrate from the database doesn’t have duplicate values but the UNION SELECT injection doesn’t work. Furthermore, Portswigger has a number of examples and they all start with a single quotation mark to break out of the existing SQL query. Adding a single quotation mark to the UNION ALL SELECT command here doesn’t work. I’m probably misunderstanding what’s going on but feel free to leave me a comment.
Anyway, back to the hack. So we know there are likely three table columns. One for the product picture, one for the product description, and one for the product price. We also know that there is likely a table called email, or emails. With this information, we can structure our UNION ALL SELECT command.
SQL Injection
Firstly, in order to perform an SQL injection on realistic 4, we need to tell the application what type of query we’re performing.
UNION ALL SELECTSecondly, we tell the database what columns we want and what column we want to inject our data into. This works with both columns two and three. However, if you inject it into column two your font will be normal but if you inject it into column three your font will be bold. This matches the formatting of the website.
NULL, *, NULL, NULLFinally, we tell it where we want to query the data from. For example, we want to pull the data from the email table. We also need to end the query with a semicolon.
FROM EMAIL;Put it all together and you should have an SQL injection that looks like the following.
UNION ALL SELECT NULL, *, NULL, NULL FROM email;Moving forward, we need to append the SQL injection to the end of the URL after the 1. The query should look something similar to the image below depending on your injection point and the case of your characters.

Once you have done that, hit return on your keyboard and you should see the web application load with some additional information. The email addresses from the mailing list have been included with the product queries.
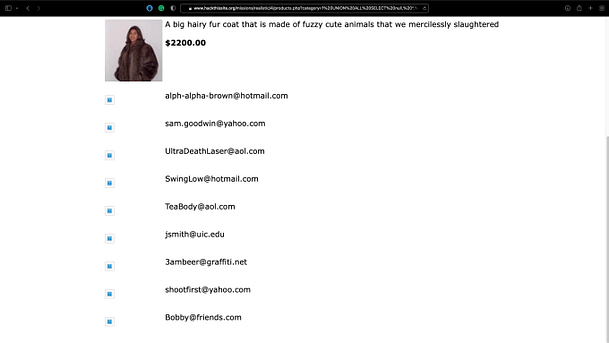
Copy the email addresses from the page and head back to the main HackThisSite website. Click your name on the left-hand side and then when your profile loads, click it again. You will now a send message box. Change the recipient to SaveTheWhales and send them the list of email addresses that you hacked from the FAP website.
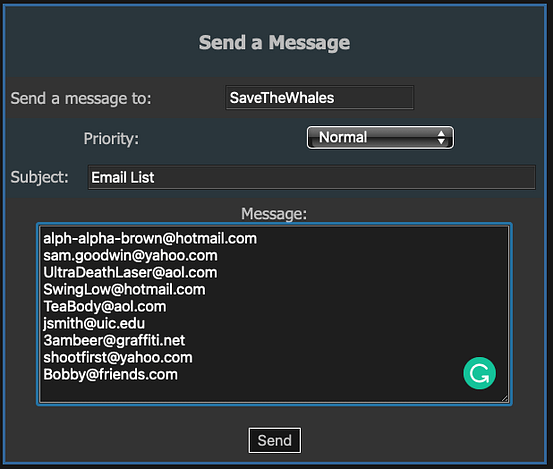
That’s it, you should now have completed this mission. This was a fun mission that uses a practical exploitation technique in the form of a UNION-based SQL injection. While I argue that the syntax is a bit odd and will wait for someone to correct me before changing my mind, it is a good example. What we can learn from this is that queries to back-end databases should use prepared statements. Use prepared statements!!!
Anyway, thats Realistic 4 hacked and that’s it for today. I hope you enjoyed it. Please check out the video and I will see you next time.

