Hello World and welcome to haxez, today I’m going to be covering Vulnerability Scanning. Vulnerability scanning is the process of using tools to scan your target for vulnerabilities. There are many different tools that can perform vulnerability scans and the type of target you are scanning will determine what tools you use. For example, if you’re looking for vulnerabilities that affect services on the host then you could use Nmap, Nessus, OpenVAS, and many others. However, if you’re attacking a web application then you would likely use Nikto, Burp Suite, OWASP ZAP, or some other tool.
Nmap Vulnerability Scanning
If you haven’t seen my post on Nmap then I would recommend giving it a read. It covers Nmap in more detail than I intend to do here. With that said, Nmap is a fantastic vulnerability scanner. Early in my IT career, I had many misconceptions about Nmap. I thought it was merely a network scanner used to identify what hosts were online and what services were running. How naive, Nmap is a comprehensive network auditing tool that can identify and exploit vulnerabilities. I use it on almost every project I’m on. I highly recommend reading more about the different flags and scripts before recklessly running them like I’m about to do.
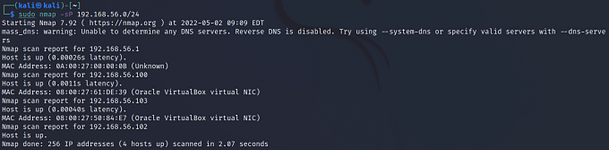
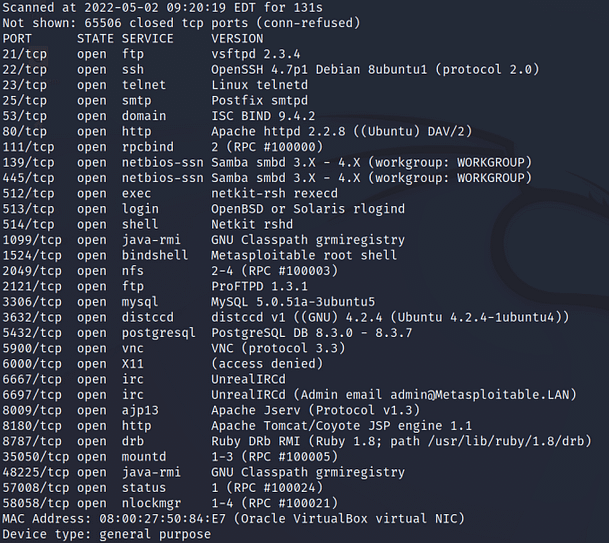
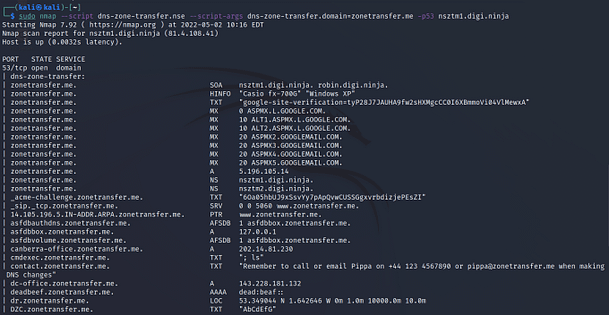
The image below shows the output of a Nmap scan configured to find vulnerabilities. You can see from the results that it has found some CVEs. I first specified the ‘-g’ flag to set the source port to 53. This is useful for firewall evasion as some firewalls may be configured to allow DNS traffic in from any source. I then specified the ‘-f’ flag to fragment the packets. This works by splitting the packets into multiples of 8 which can also be beneficial for firewall evasion. Then, I specified ‘-sV’ to get the service versions and ‘-p0-‘ for all ports. Next, I specified the ‘–script’ argument followed by various categories of scripts to execute. Finally, I added the IP address and the ‘-T5’ to speed it up.
This configuration is incredibly reckless and you should never use it against production environments. I’m merely using it to demonstrate the power of Nmap. Do NOT do this.
sudo nmap -g 53 -f -sV -p0- -O --script vuln,auth,exploit 10.0.2.5 -T5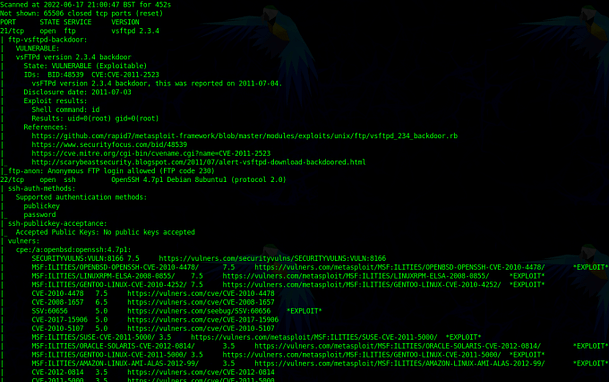
Nessus
Where to start! Nessus from Tenable is a powerful multifunctional vulnerability scanning and auditing solution. It can be used to scan entire ranges of IP addresses or perform audits from uploaded configuration files. Whether you’re on team red or blue, chances are you’ve used it or at least heard of it. Nessus is likely going to be your tool of choice when performing vulnerability assessments or full-on penetration tests. I will probably create a separate article and video focusing on Nessus as part of the Hacker Tools series. All you need to know for the moment is that it is an effective vulnerability scanner. They offer an essential version for you to play around and I highly recommend giving it a go. However, the professional version has many more cool toys.
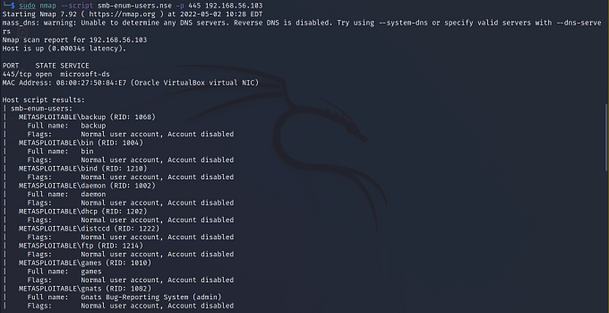
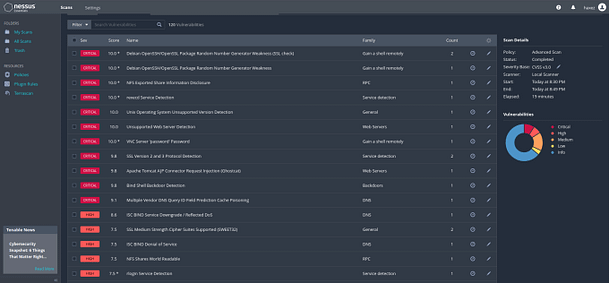
The image below is of an advanced scan that I performed against the Metasploitable 2 virtual machine. I configured it to scan all ports (0–65535) and turned off the Denial of Service plugin. Other than that I only changed the reporting to report as much as possible. As you can see it has found a bunch of issues (as expected).
Nikto Web Application Scanning
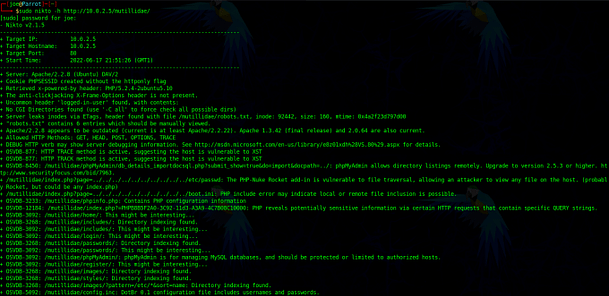
Nikto is a free CLI web application vulnerability scanner. It will search for interesting directories and files, analyze response headers, check for outdated software, and look for vulnerabilities. It’s a good place to start when performing web application security assessments. Granted, it won’t hack into the website for you, but it will give you a good idea of things to look at during the early stages of the assessment. Nikto can be intrusive and I have seen web applications suffer performance issues when scanning them. However, the hardware that those apps were hosted on wasn’t fit for purpose. I’ve also found that Nikto can be tricked by web application firewalls. It will report a 200 response for every directory that it brute forces, even though it doesn’t exist. Or it will misidentify a vulnerability or some other incorrect server-side configuration.
Burp Suite Web Application Scanning
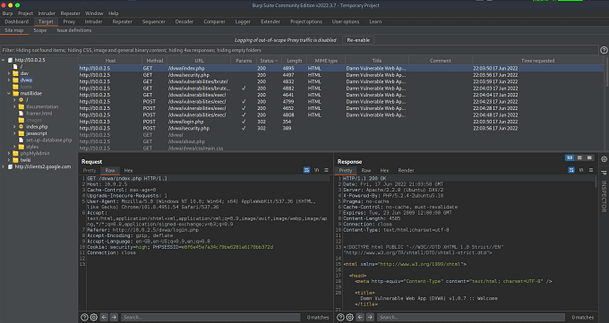
No vulnerability scanning article would be complete without Burp Suite from Portswigger. This is the Bugatti Veyron of web application vulnerability scanners. Unfortunately, I only have the community version installed in my home lab but I use the pro version almost daily. The pro version has many more features that allow for automated scanning and vulnerability detection. You still need to manually go through and verify those findings but Burp takes out a lot of the guesswork. It also has an extensive list of additional plugins that you can install to increase the functionality. If you’re looking to get a job in cybersecurity then knowing how to use Burp Suite will probably improve your chances once it comes to that technical test.
Conclusions
I know I have only scraped the surface on the different vulnerability scanners that are available. However, to cover them all would take forever and I only wanted to cover the ones that you are likely to come across first. Granted there are some amazing alternatives out there. Where you have Nessus, you also have OpenVAS. Where you have Burp Suite, you also have OWASP Zap. I’m not saying that one is better than the other, I suppose that comes down to personal preference and these tools are my personal preference. I know a guy who almost refuses to touch anything that isn’t command line based. Archie, I salute you. Anyway, definitely give these tools a try against your own test virtual machines. They are a lot of fun.