Hello world and welcome to haxez, in this post we are looking at Hack This Site Basic Web Challenge Level 4. If you haven’t read through my previous posts in this series then you can find them here: Part 1, Part 2 and Part 3. This challenge requires the user to have some knowledge of HTML. The objective of this challenge is to recover the password however sneaky Sam has added an email script to the application.
Viewing The Basic 4 Web App
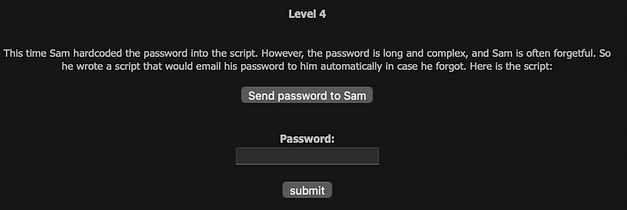
After logging in to Hack This Site and navigating to the basic web challenge level 4, you will be presented with the screen below. The text reads as follows “This time Sam hardcoded the password into the script. However, the password is long and complex, and Sam is often forgetful. So he wrote a script that would email his password to him automatically in case he forgot. Here is the script:”
Inspecting The Basic 4 Web Page Source
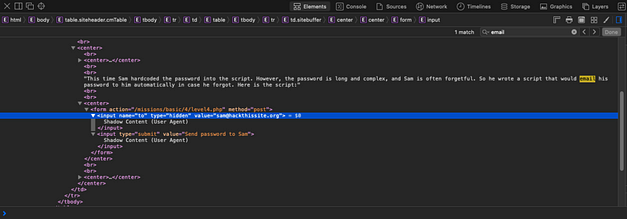
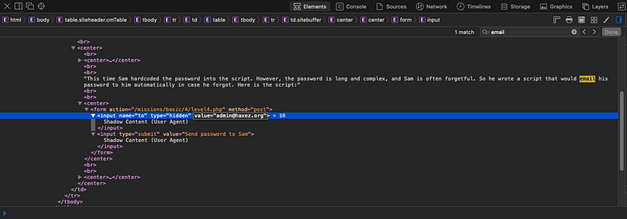
The concept behind this is simple, if Sam needs the password he will press the button and email it to himself. We need to manipulate the script so that the password is sent to us instead of Sam. To do that we need to view the web page source and see what the script is doing. The screenshot below shows that the email address sam@hackthissite.org is being posted to level4.php when the button is clicked.
Modifying The Basic 4 Page
We can modify the page source directly through developer mode. By double-clicking the current email address, we can replace it with our own. Once we have changed the email address we can click the “Send password to Sam” button and it will send the password to our email address.
Submitting The Web Request
After clicking submit go and check your mailbox to see if the password has arrived. The email will be from sam@hackthissite.org and will contain the password. If you open the email you should be able to copy the password and paste it into the password submission system.
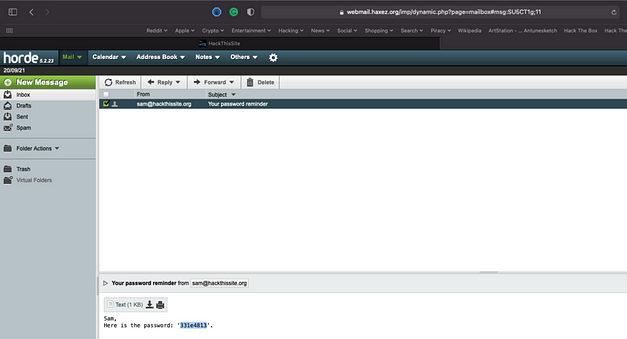

This was a fun challenge that teaches a valuable lesson about hardcoding passwords or other credentials within applications. If the code is rendered client-side then no sensitive information should be included in the code.