Hello world and welcome to haxez, where today, we’re looking at Hack This Site Basic Web Challenges level 10. This challenge requires us to manipulate cookies in order to authenticate against the application. A cookie is a small file that contains data, the data is utilised by the applications to make decisions. For example, if you add an item to your shopping basket then the website could issue a cookie which contains that information. That way, when you revisit the application, the item is still in your basket. If you haven’t see my previous posts in this series then you can do so here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7, Part 8, and Part 9.

Testing The Basic 10 Web Application
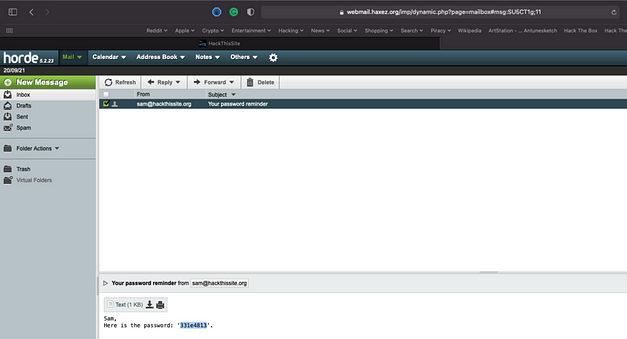
After logging in to the application, you will be presented with the following page. There aren’t any hints this time, this time it’s just a password submission form. The image for the challenge mentions having to know your way around Javascript. I’ve looked at the source and didn’t find anything interesting.
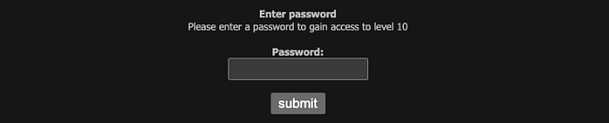
I then fed the application some test data to see how it would respond. I tested a number of characters associated with various types of attacks but they were all sanitised. Submitting generic strings to the password input box results in an authorisation error.

Exploiting The Web Application
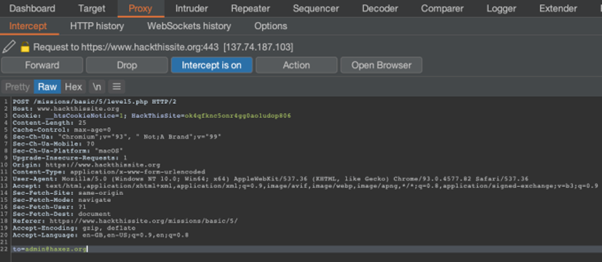
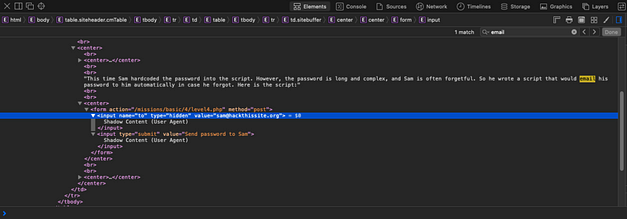
In order to investigate the application further, I used Burp Suite to intercept the request. The image below shows that the request is setting a cookie called “level10_authorized”. The cookie is set to no, but it can be manipulated through Burp Suite.
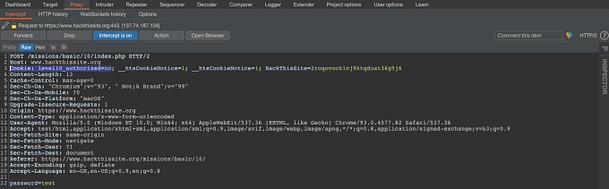
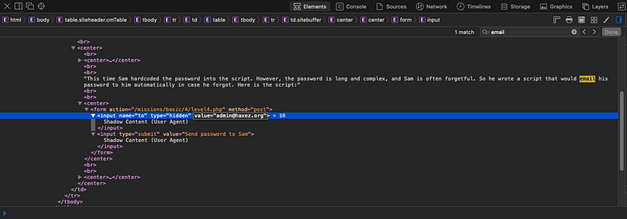
Burp Suite allows you to intercept the request and modify it before forwarding the data to the application. As we have captured the request, let’s change the value of the “level10_authorized” cookie from no to yes and forward the request. You will also need to forward any subsequent requests too.
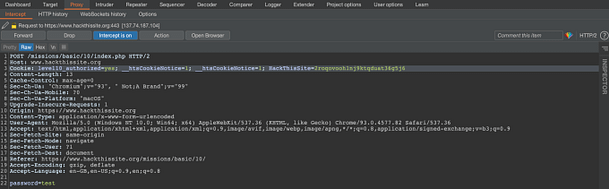
Completing The Challenge
After changing the value to yes and forwarding the requests, you should have completed the challenge. This was a fun challenge that shows the importance properly implementing cookies. Using yes/no cookies for authentication is not a good method for authenticating users. Cookies are used for user sessions to keep users logged in. However, those cookies are set after the user has successfully authenticated with a password.